Encrypting Data in the Cloud: Best Practices for Data at Rest and in Transit
Protecting sensitive data in the cloud requires robust security measures, and this guide provides a comprehensive overview of data encryption. It delv...
152 posts in this category

Protecting sensitive data in the cloud requires robust security measures, and this guide provides a comprehensive overview of data encryption. It delv...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
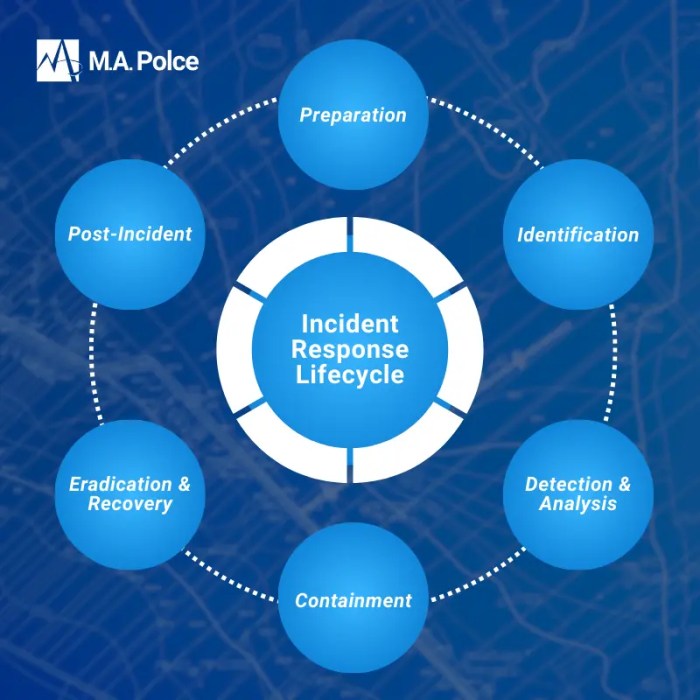
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...
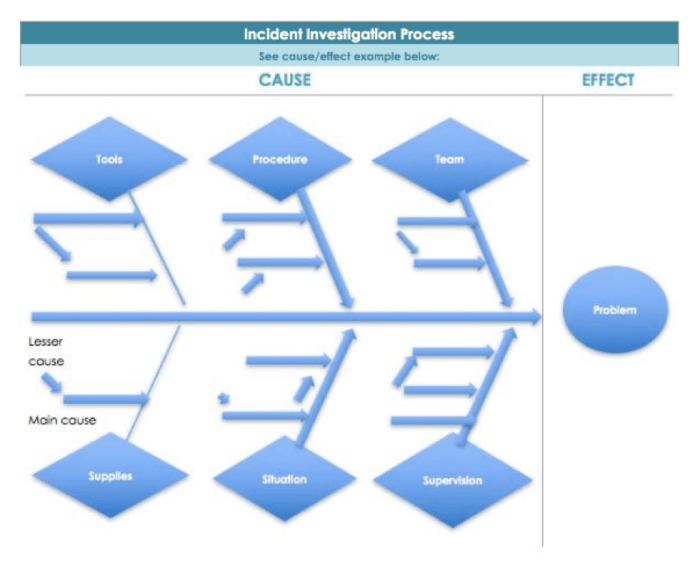
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
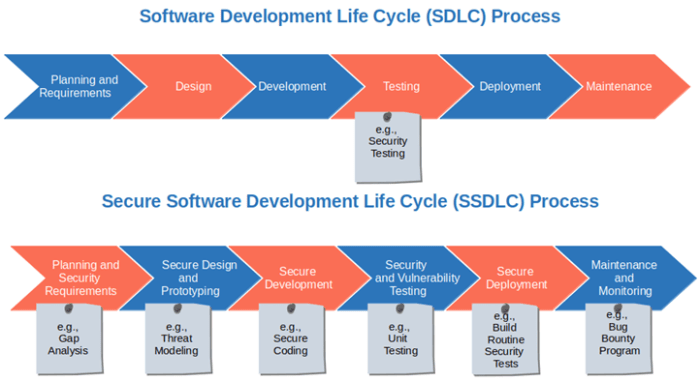
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...

In the modern cloud-centric business environment, robust data and infrastructure security is critical. Security Information and Event Management (SIEM...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
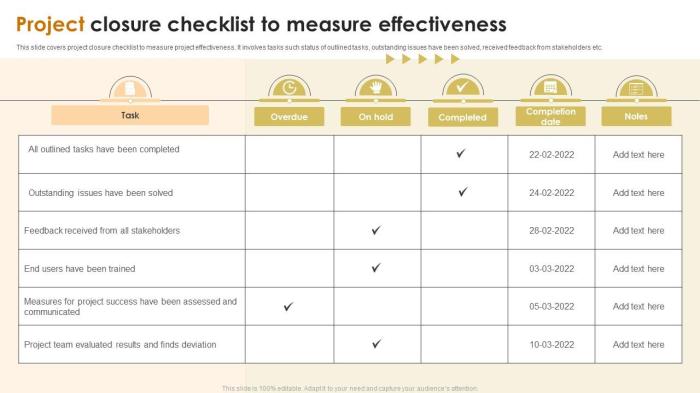
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...
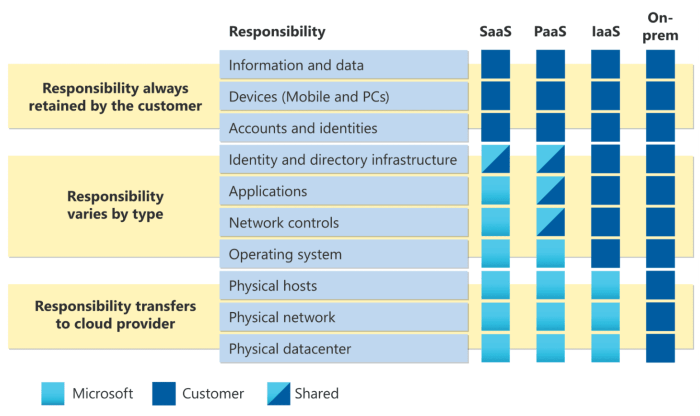
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...