
Setting Up a Honeypot: A Guide to Detecting and Trapping Cyber Attackers
Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...
152 posts in this category

Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...

Discover how Open Policy Agent (OPA) is transforming policy enforcement in modern software development. This guide explores OPA's capabilities in mana...
Protecting your organization from internal cybersecurity risks is paramount. This guide, "How to Detect and Respond to Insider Threats," offers a comp...
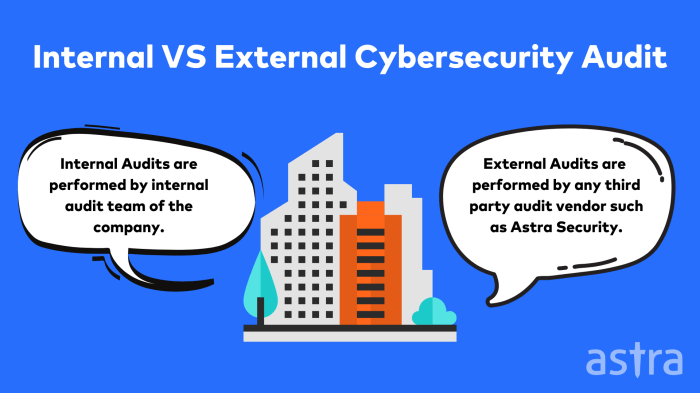
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...

This comprehensive article explores the evolving landscape of cloud security, addressing current threats and vulnerabilities while examining the impac...
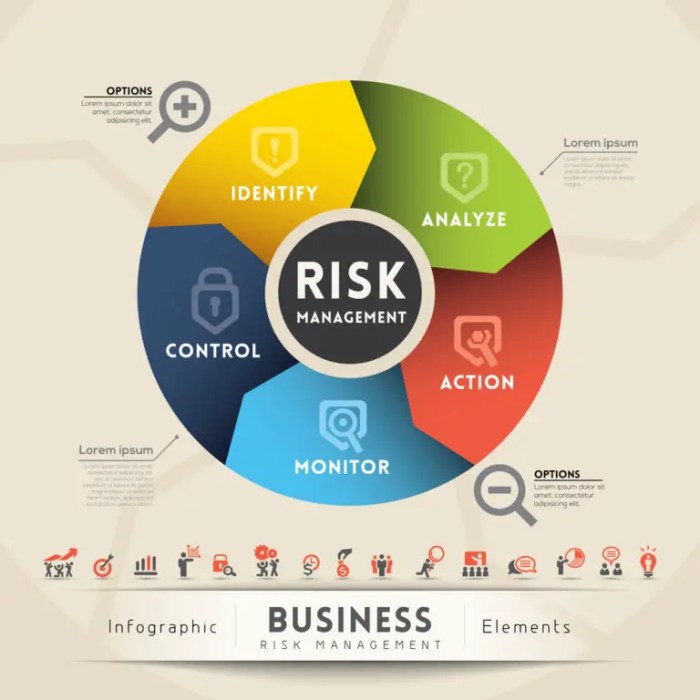
Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...
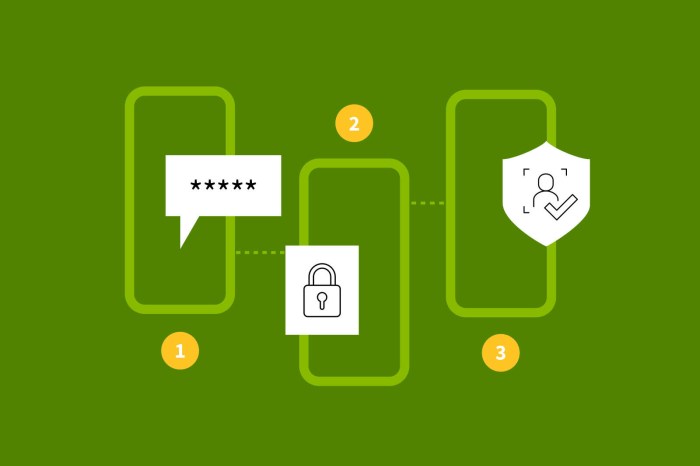
Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...
In an increasingly cloud-dependent business environment, establishing a strong cloud security team is crucial for protecting valuable data and applica...