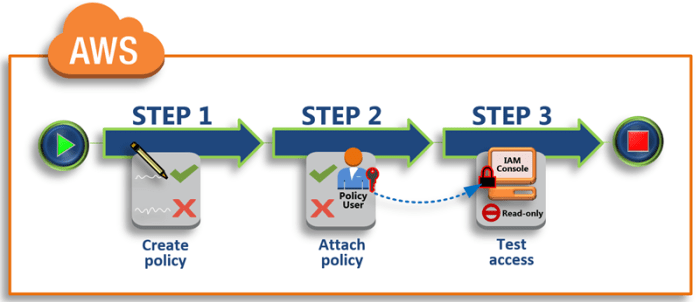
IAM Policies: Understanding and Implementing Secure Access Control
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...
152 posts in this category

This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...

This article delves into the intricacies of identity federation, explaining its core concepts, components, and the benefits it offers for streamlined...
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...

This comprehensive guide provides a detailed overview of securing the Kubernetes control plane, covering essential aspects from authentication and aut...

Data security is crucial for modern businesses, highlighting the need for effective backup and disaster recovery (BDR) strategies. This guide provides...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...

This comprehensive guide explores the multifaceted landscape of container security, outlining critical best practices to protect your deployments from...

A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...
This comprehensive guide explores the transformative power of Zero Trust Network Access (ZTNA) in modern cybersecurity, outlining its core principles...
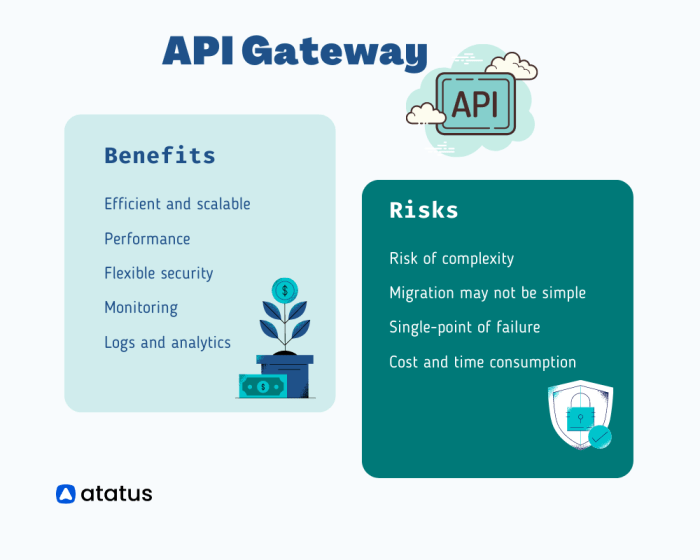
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...

Privacy-preserving computation offers a groundbreaking approach to data security, enabling the processing of encrypted data without the need for decry...