
Implementing Interactive Application Security Testing (IAST): A Practical Guide
This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...
152 posts in this category

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...

Navigating the complexities of cloud security requires a proactive approach, beginning with a comprehensive incident response plan. This guide highlig...
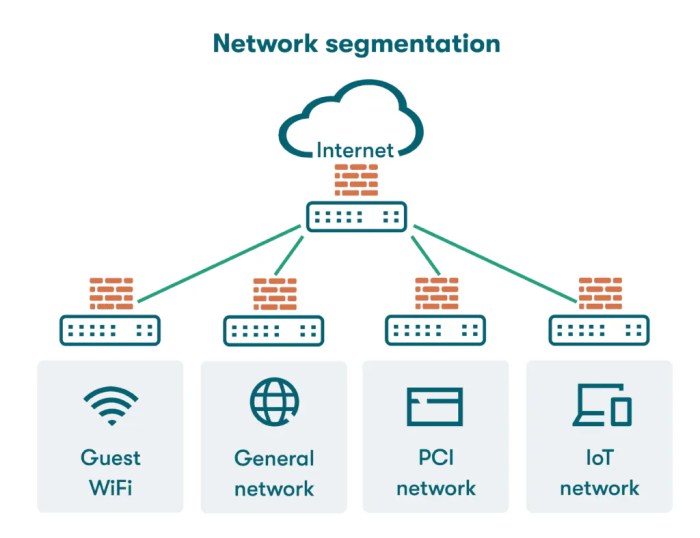
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...
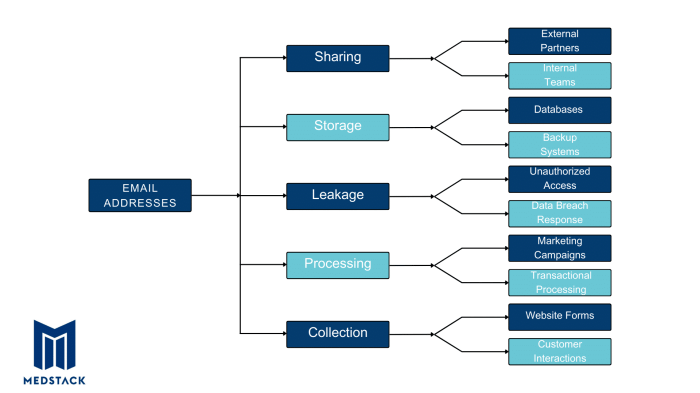
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...

This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...
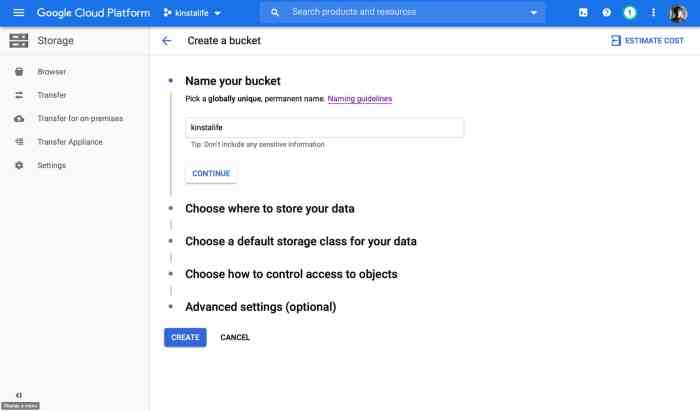
With the increasing reliance on cloud storage, securing your buckets from misconfiguration is crucial. This article delves into the unique security ch...

This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...

This comprehensive guide explores the ISO 27001 standard, a globally recognized framework for information security management. From its core principl...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...

Cloud systems demand constant vigilance to ensure both security and optimal performance. This guide outlines essential strategies and best practices f...
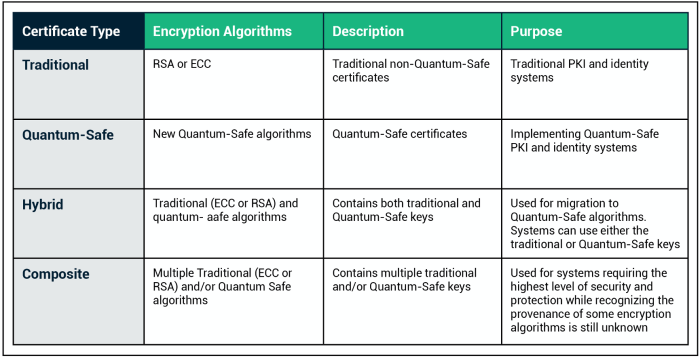
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...

This article provides a comprehensive guide to preventing SQL injection attacks specifically within cloud application environments. It covers critical...