Building a FinOps Culture: A Practical Guide for Organizations
This article provides a crucial roadmap for organizations seeking to establish a FinOps culture and optimize cloud spending. It outlines the key steps...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a crucial roadmap for organizations seeking to establish a FinOps culture and optimize cloud spending. It outlines the key steps...
Protecting sensitive data in the cloud requires robust security measures, and this guide provides a comprehensive overview of data encryption. It delv...

Facing a large-scale data migration? Discover the power of the Migration Factory approach, a systematic methodology designed to streamline and automat...

Creating a compelling business case is essential for successful cloud migration projects. This strategic shift requires articulating the value proposi...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...

Migrating from a monolithic architecture to microservices offers significant advantages in scalability and agility. This guide provides a structured f...

This comprehensive guide explores the critical architectural considerations for achieving HIPAA compliance, covering essential areas such as data secu...
This comprehensive guide explores the Retry Pattern with Exponential Backoff, a crucial strategy for building resilient and fault-tolerant systems. Fr...
This article dives into the crucial concept of disposability within the framework of 12-factor applications, highlighting its importance in modern clo...
The FinOps X Framework represents a significant evolution in cloud financial management, moving beyond traditional practices to offer a more comprehen...
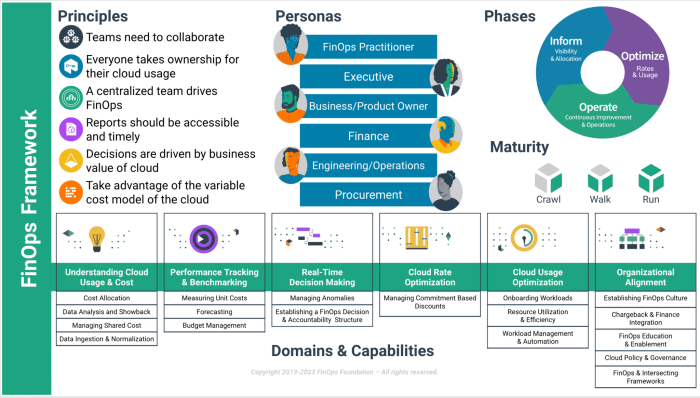
The "Operate" phase of the FinOps lifecycle is the critical action stage where cost optimization strategies are implemented and monitored. This phase...
This comprehensive guide explores the creation of serverless project templates, offering a deep dive into the benefits and considerations of this mode...