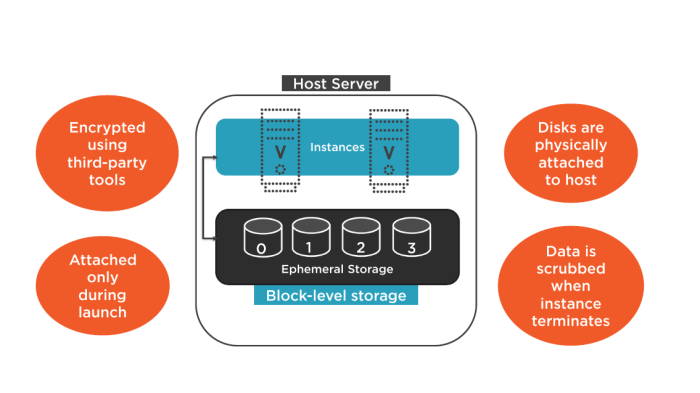
Understanding Ephemeral Storage in Serverless Functions
This article delves into the world of ephemeral storage within serverless functions, exploring its characteristics, advantages, and limitations. Reade...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article delves into the world of ephemeral storage within serverless functions, exploring its characteristics, advantages, and limitations. Reade...
Cloud computing offers immense benefits, but managing its costs effectively is crucial. This guide provides a comprehensive approach to crafting and o...
Handling cardholder data in the cloud necessitates adherence to Payment Card Industry Data Security Standard (PCI DSS) compliance. This guide provides...
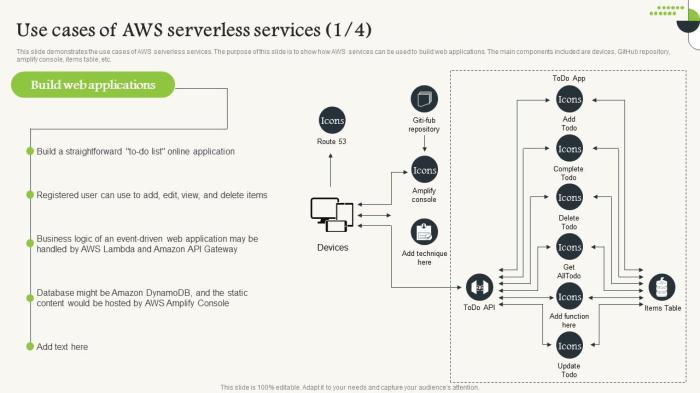
The serverless-first development approach is revolutionizing software architecture by making serverless computing the cornerstone of application desig...
This article delves into the vital practice of explicitly declaring and isolating dependencies, a key component of robust and scalable software develo...

This article delves into the intricacies of identity federation, explaining its core concepts, components, and the benefits it offers for streamlined...
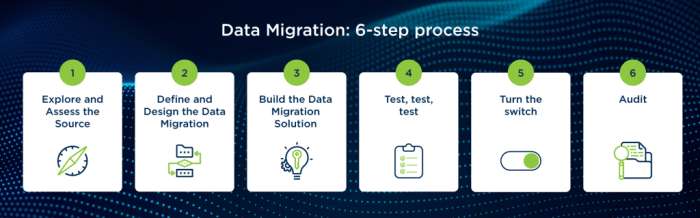
Migrating a CRM system is a complex undertaking, requiring careful planning and execution to ensure a successful transition. This comprehensive guide...

Organizing your organization's data starts with a well-defined tagging policy, serving as a crucial roadmap for discoverability and efficient informat...

This comprehensive guide delves into the Observer Pattern, a crucial design pattern for building flexible and maintainable systems. The article provid...

This article delves into the critical world of database version control, exploring its core concepts, benefits, and the common challenges encountered....

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
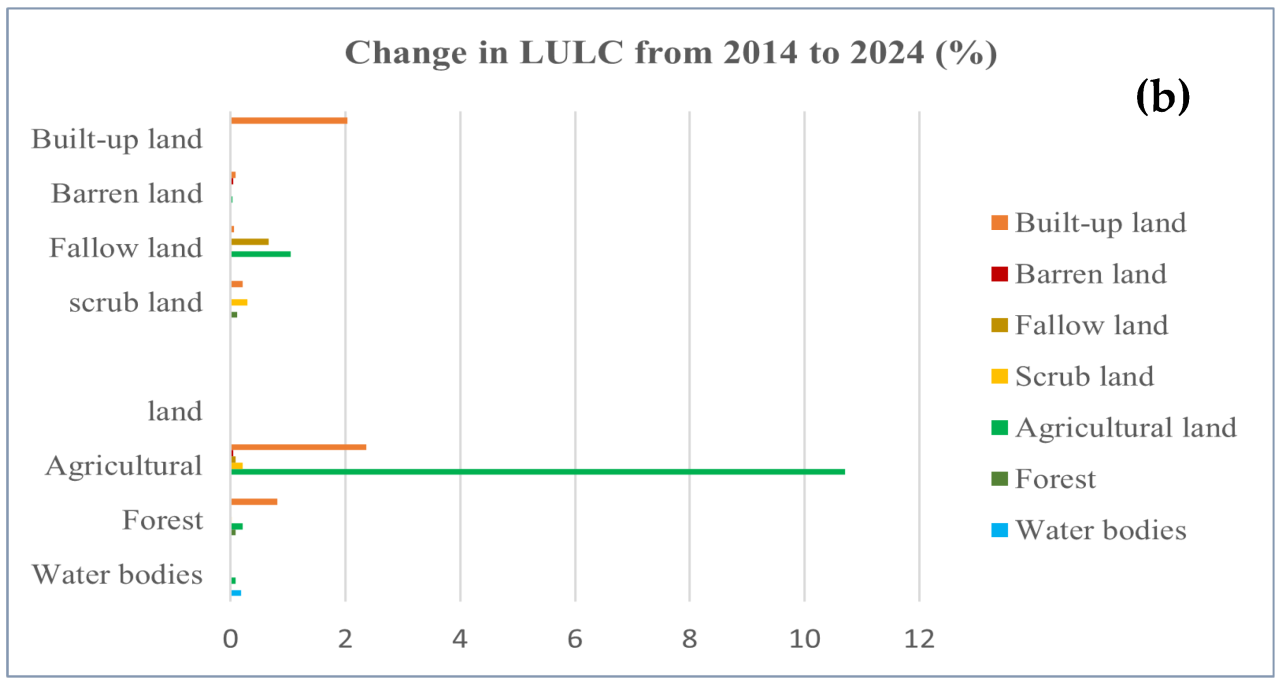
This comprehensive guide provides a detailed walkthrough of Google Cloud Functions, covering everything from initial setup and deployment to advanced...