
Docker Compose for Local Development: A Comprehensive Guide
Docker Compose offers a streamlined solution for local WordPress development by containerizing dependencies, ensuring consistent environments across d...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Docker Compose offers a streamlined solution for local WordPress development by containerizing dependencies, ensuring consistent environments across d...

This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...
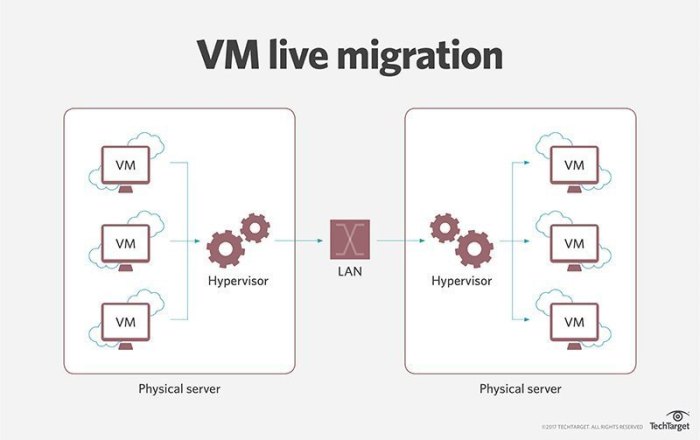
This comprehensive guide outlines the crucial steps involved in migrating your virtual machines to the cloud, from initial assessment and strategy pla...
This article provides a comprehensive guide to implementing a Zero Trust security model within cloud environments, covering key principles, asset iden...
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...

Ensuring data consistency is paramount when designing and deploying microservices architectures. This comprehensive guide explores the challenges of m...

"Shifting Left" in software development provides a proactive strategy for cost awareness by integrating financial considerations early in the developm...
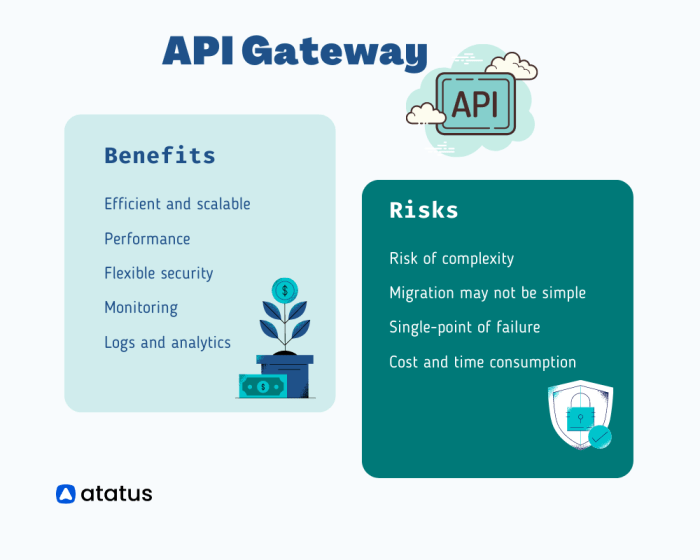
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...
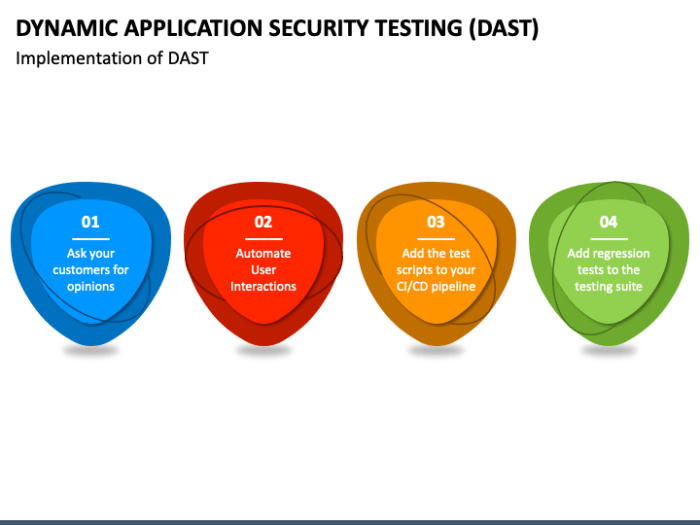
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...
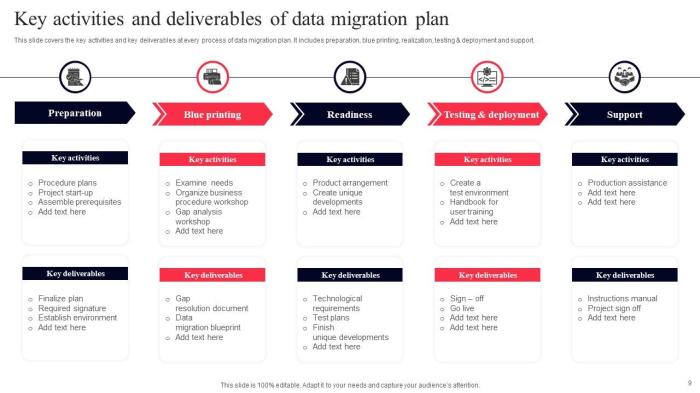
This article provides a comprehensive guide to data migration plan templates, outlining their essential purpose, benefits, and the risks associated wi...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...