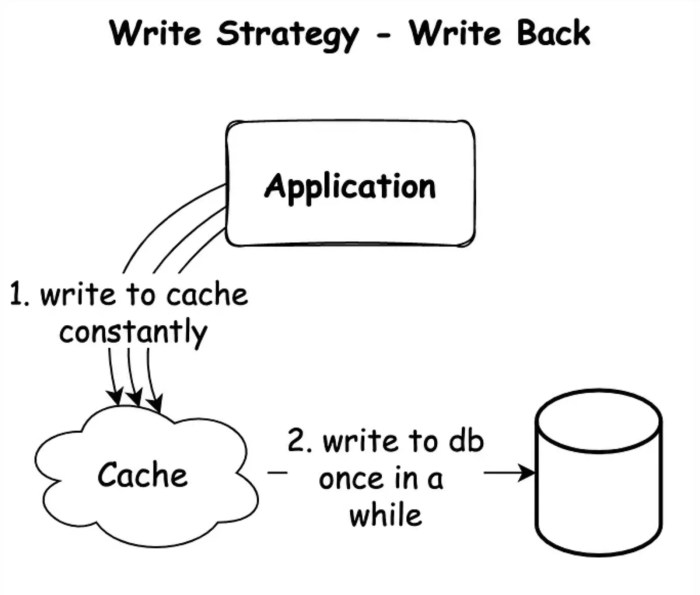
Write-Through vs. Write-Back Caching: A Comprehensive Guide
This article delves into the critical distinctions between write-through and write-back caching, two fundamental strategies for optimizing data access...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article delves into the critical distinctions between write-through and write-back caching, two fundamental strategies for optimizing data access...
Technology migration projects are complex, but learning from the successes and failures of other companies can significantly improve your own outcomes...
Large-scale message processing systems rely on effective strategies for handling high volumes and ensuring reliable delivery. The "Claim Check Patter...

This article provides a comprehensive introduction to Kubernetes, the leading platform for container orchestration. It demystifies the complexities of...

Cloud computing's scalability necessitates a robust approach to cost management. This guide provides a comprehensive overview of implementing a cloud...
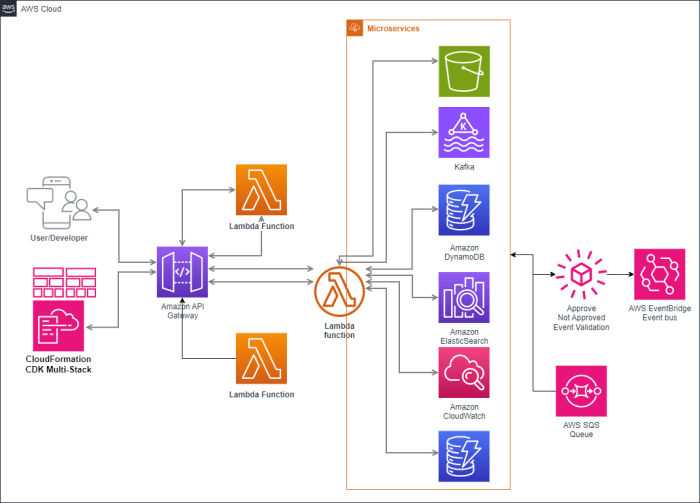
This comprehensive guide explores the power of the AWS Cloud Development Kit (CDK) for infrastructure provisioning, offering a deep dive into its bene...

Selecting the right data visualization tool is crucial for architects to effectively communicate complex information. This comprehensive guide provide...
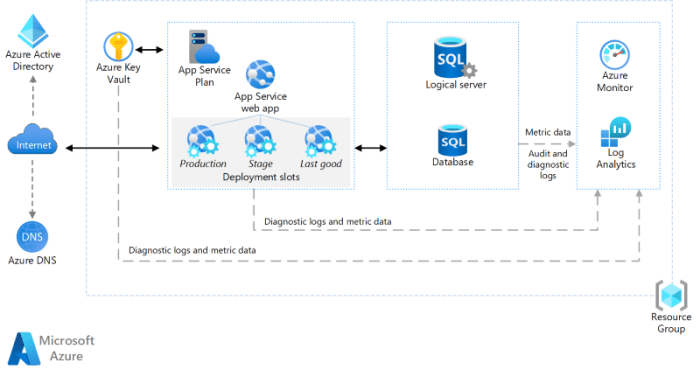
This comprehensive guide provides a strategic roadmap for planning and implementing robust network connectivity to the cloud, covering fundamental con...
This comprehensive article meticulously examines the crucial differences between unit testing and integration testing, offering a clear understanding...

This article delves into the crucial role of the health check API endpoint in software development, explaining its function as a vital monitoring tool...

Understanding cloud environments requires diligent monitoring of key metrics across resource utilization, network performance, application behavior, a...
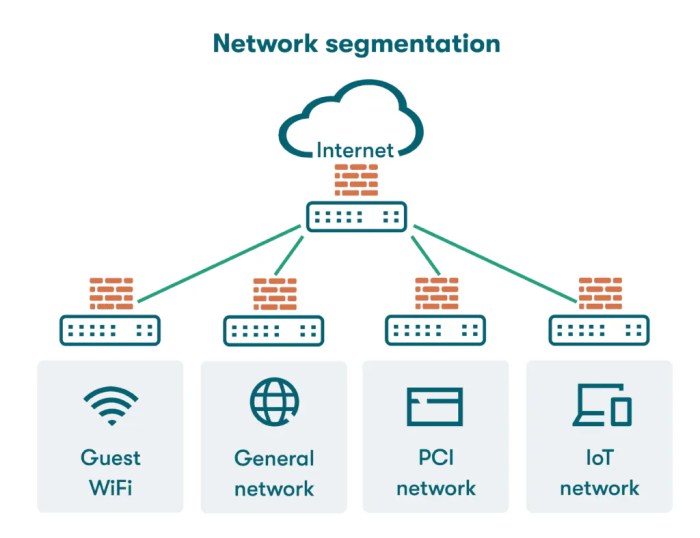
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...