
Container Vulnerability Scanning: A Comprehensive Guide
This comprehensive guide delves into the critical practice of container vulnerability scanning, explaining its core concepts and importance in securin...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide delves into the critical practice of container vulnerability scanning, explaining its core concepts and importance in securin...

APIs are fundamentally reshaping modern architecture by enabling seamless communication and data exchange between different software applications. Thi...

Minimize disruptions and maximize success by understanding and reducing your change failure rate. This comprehensive guide delves into identifying roo...
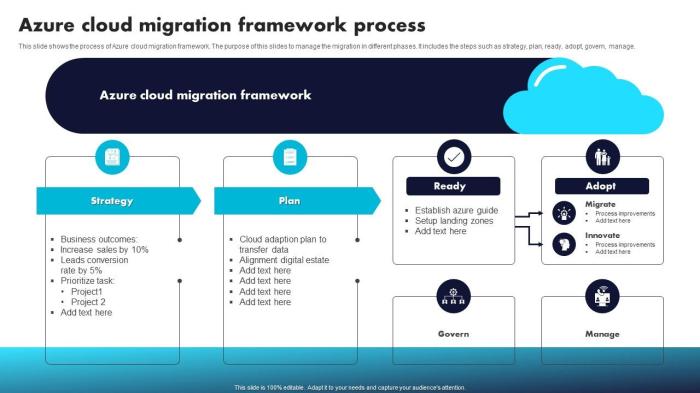
Successfully navigating a cloud migration requires a robust cloud governance framework to mitigate risks and ensure compliance. This comprehensive gui...
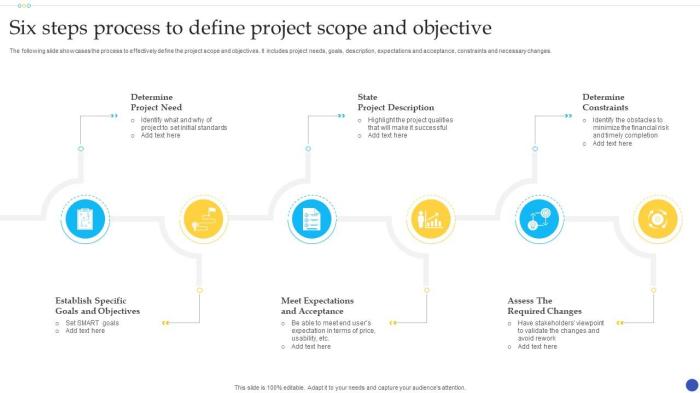
To successfully navigate a FinOps journey, establishing clear goals for each iteration is crucial. This involves more than just cutting costs; it's ab...
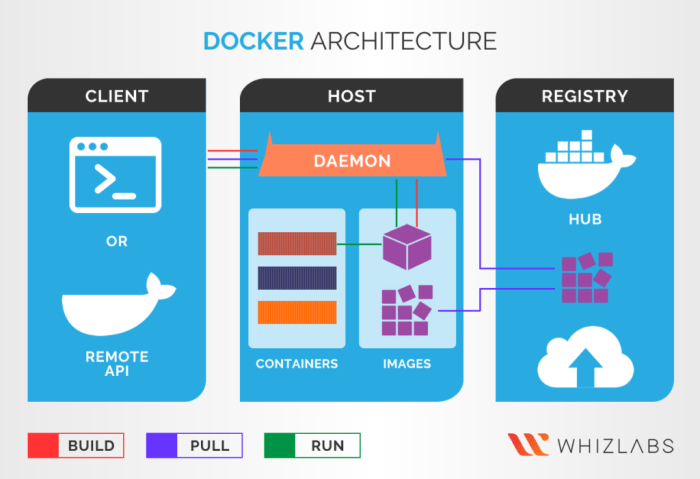
This comprehensive article offers a detailed comparison of Docker Swarm and Kubernetes, two leading container orchestration platforms. Through explori...
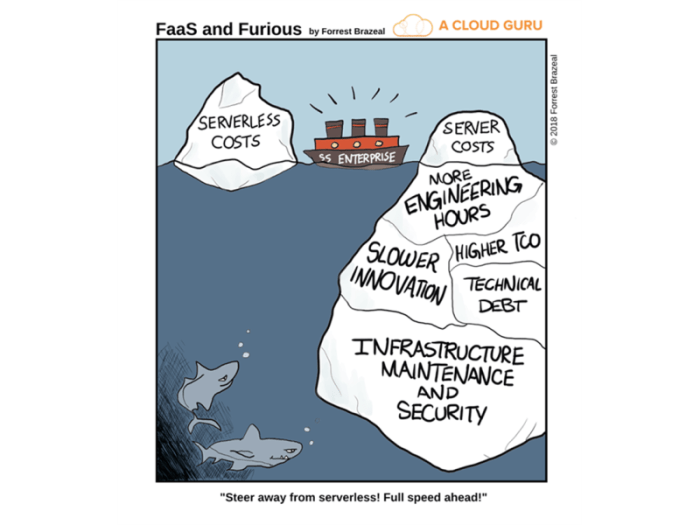
This article delves into the often-overlooked cost implications of serverless cold starts, a crucial factor in optimizing application performance and...

This comprehensive guide provides a deep dive into implementing a service mesh for microservices, covering everything from the core functionalities an...

Optimizing cloud spending requires accurate forecasting, and this article explores how AI models can revolutionize the process. Learn about the specif...

Successfully migrating a system is only the initial phase; long-term operational tasks are crucial for sustained success. This article delves into th...

Facing Lambda deployment size limitations and slow cold starts? This comprehensive guide explores how to effectively manage large deployment packages...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...