
Identifying and Eliminating Waste: A Guide to Terminating Unused Cloud Resources
Unused cloud resources silently drain budgets and can create security vulnerabilities, making their identification and termination crucial for optimal...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Unused cloud resources silently drain budgets and can create security vulnerabilities, making their identification and termination crucial for optimal...
Understanding Availability Zones (AZs) is crucial for building resilient cloud applications. This article provides a comprehensive overview of AZs, ex...
This comprehensive guide explores the transformative power of Continuous Delivery (CD) in automating application deployment, highlighting its core pri...
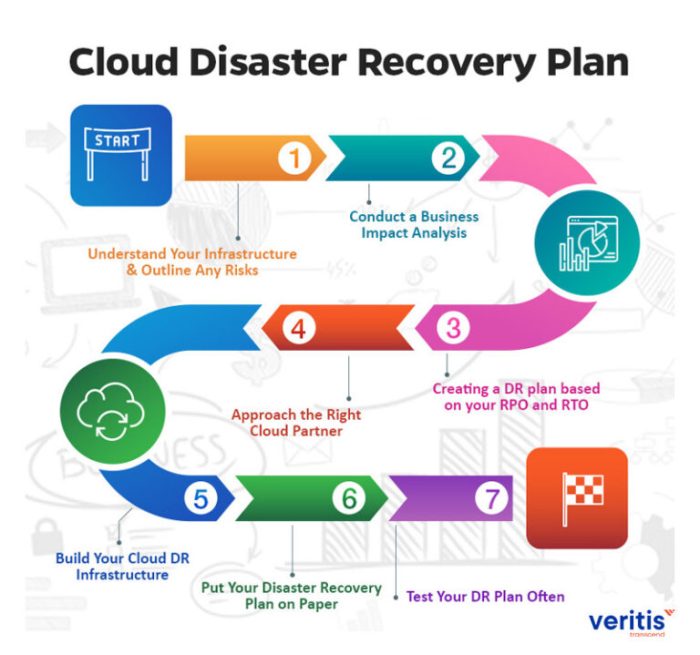
This comprehensive guide explores the critical elements of a cloud disaster recovery plan, covering everything from understanding core objectives and...

The FinOps Maturity Model offers a vital framework for organizations seeking to optimize their cloud spending. This structured approach provides a roa...

This article provides a comprehensive overview of service meshes, elucidating their core functionalities, role in microservices architecture, and bene...
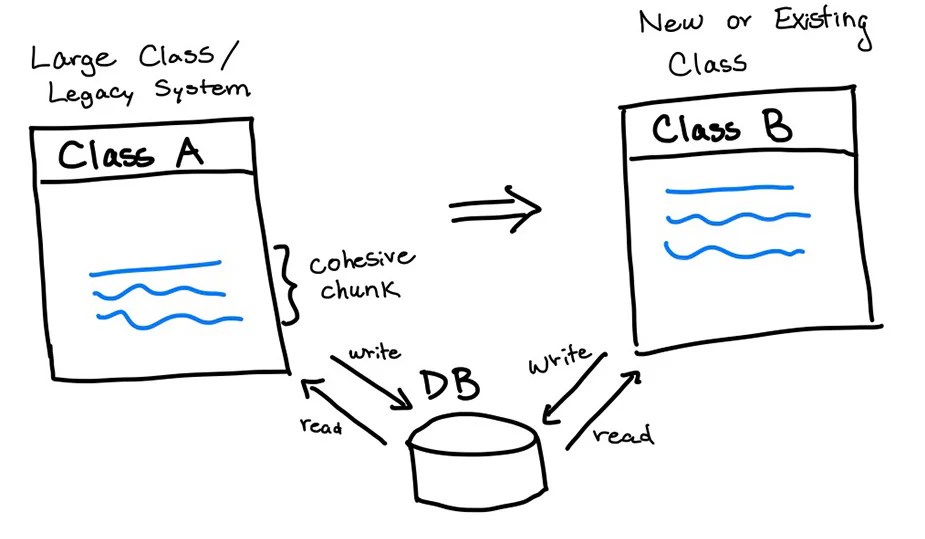
Facing the complexities of application modernization? The Strangler Fig pattern provides a strategic and controlled approach to incrementally update l...

This article provides a comprehensive overview of cost allocation tags and business tags, detailing their distinct purposes and functionalities within...
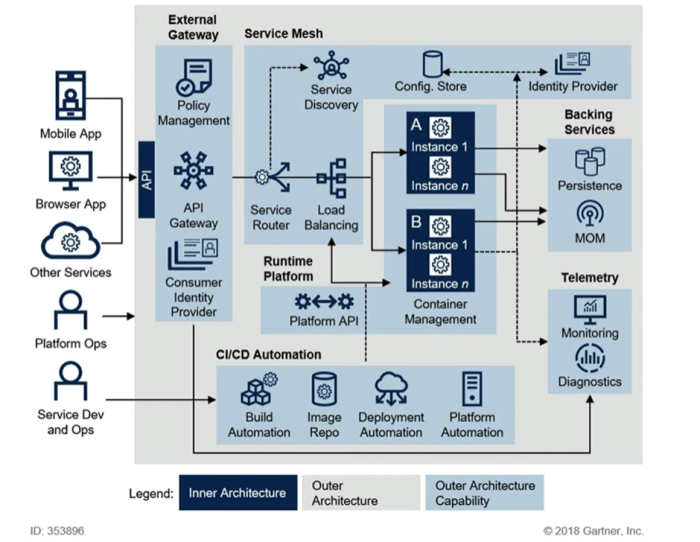
Rebuilding an application for cloud native architecture demands a fundamental shift in design, deployment, and operation, extending far beyond infrast...
This article provides a comprehensive overview of cloud landing zones, explaining their core function as a secure and scalable foundation for cloud en...
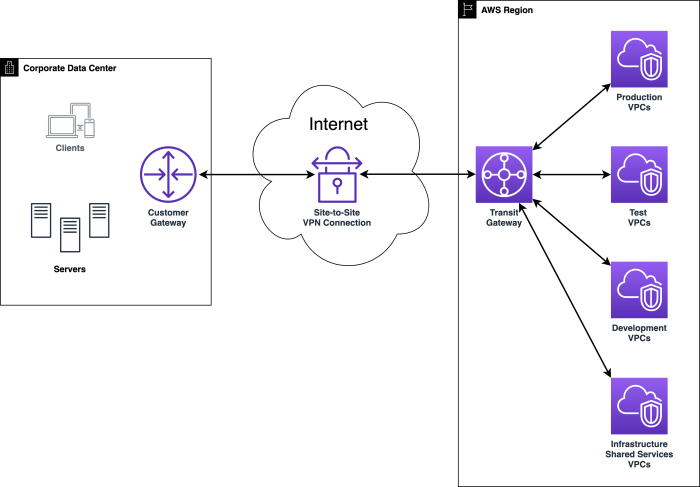
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...
Serverless environments utilizing Lambda functions are susceptible to injection attacks, a critical security concern arising from vulnerabilities in i...