
Creating a Serverless Development Environment: A Step-by-Step Guide
This comprehensive guide provides a step-by-step approach to establishing a serverless development environment, covering crucial aspects from choosing...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide provides a step-by-step approach to establishing a serverless development environment, covering crucial aspects from choosing...
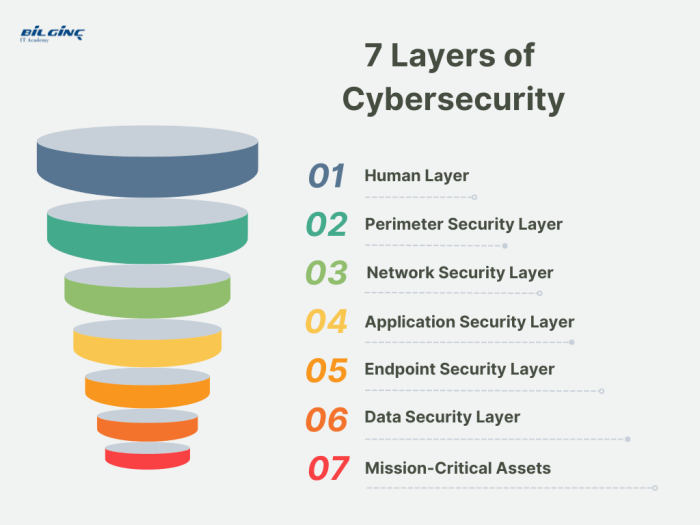
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
Embarking on a cloud migration requires a thorough understanding of your organization's readiness. This comprehensive guide provides a step-by-step ap...

Cloud systems demand constant vigilance to ensure both security and optimal performance. This guide outlines essential strategies and best practices f...

Building an effective DevOps toolchain requires careful consideration of your team's needs, budget, and long-term goals. This comprehensive guide expl...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...
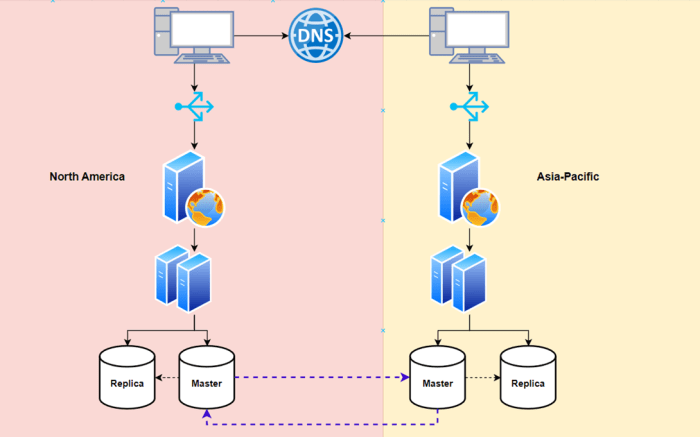
This comprehensive guide explores Continuous Data Replication (CDR) as a powerful solution for modern data migration needs. The article delves into t...

This comprehensive guide provides a detailed roadmap for creating effective cloud architecture diagrams, essential for visualizing and understanding c...
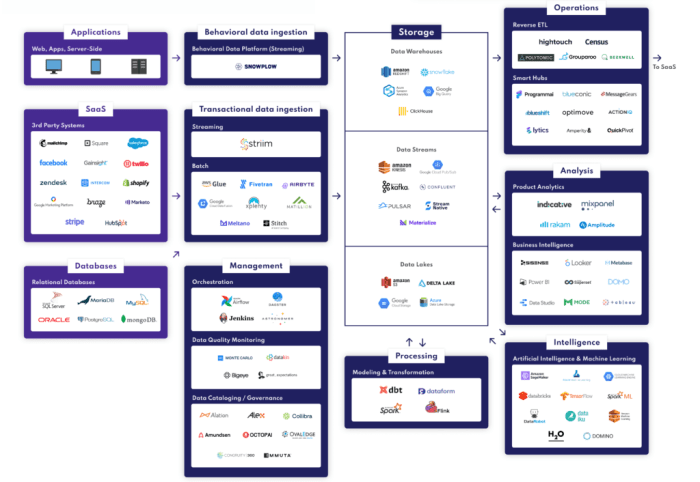
This article provides a comprehensive overview of the modern data stack, exploring its key components and functionalities, from data ingestion and sto...

This article provides a comprehensive overview of best practices for designing API gateways, essential components in modern software architecture. It...
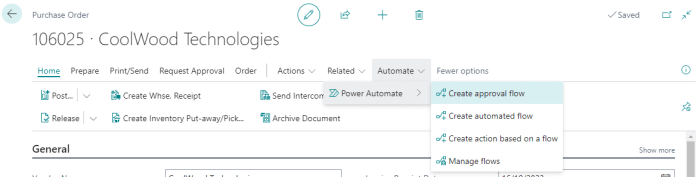
This article delves into the critical process of automating database schema migrations, exploring the benefits of automation and the challenges of man...

Zero Trust networking is revolutionizing application security by moving away from implicit trust to a "verify everything" approach. This article delve...