
Unified Cloud Cost Management: Achieving a Single View
Cloud computing's diverse landscape of providers and billing structures creates significant challenges in understanding and managing costs. This artic...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Cloud computing's diverse landscape of providers and billing structures creates significant challenges in understanding and managing costs. This artic...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...
Cloud migration offers significant advantages, but demands a well-defined strategy. This article explores the "6 R's" framework, a crucial methodology...

This comprehensive guide provides a roadmap for establishing a robust cloud governance model, starting with foundational definitions and principles. T...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...
In today's dynamic digital environment, automating security policy enforcement is paramount. This guide provides a comprehensive overview, covering es...
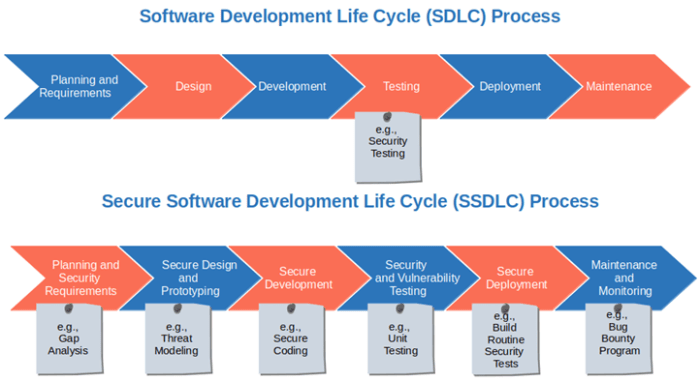
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...
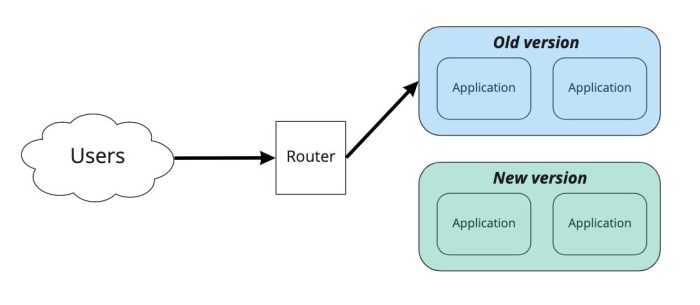
This article provides a comprehensive guide to implementing blue-green deployments, a powerful strategy for achieving zero-downtime releases. It cover...
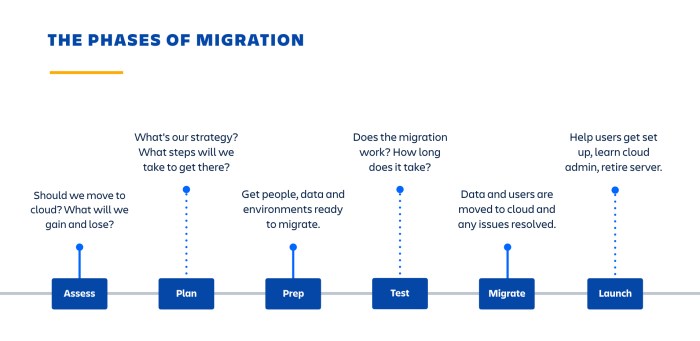
Facing the complexities of data and application migration? This article offers a strategic analysis of the process, emphasizing the automation of key...
Optimizing cloud database costs is crucial for efficient IT budgeting and sustainable business growth. This comprehensive guide explores the key facto...

This comprehensive guide outlines the critical steps for enforcing mandatory tagging across all resources, ensuring improved organization, compliance,...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...