The landscape of IT infrastructure is in constant flux, with organizations perpetually seeking to optimize their resources and enhance operational efficiency. A critical aspect of this evolution is the migration of applications to new environments, whether driven by cost savings, scalability needs, or the adoption of innovative technologies. Successfully navigating this process hinges on a meticulous understanding of application characteristics and the strategic selection of appropriate migration approaches.
This document delves into the methodologies required to assess and classify applications, providing a roadmap for informed decision-making.
This exploration provides a structured framework for evaluating application migration suitability. We will dissect the essential elements, including application characteristics, business requirements, infrastructure compatibility, code complexity, security considerations, and risk mitigation. Furthermore, we’ll examine various migration strategies, from rehosting to refactoring, and explore the tools and technologies that streamline the classification process. The ultimate goal is to empower organizations to make well-informed choices, minimize risks, and achieve successful application migrations.
Understanding Application Migration Suitability
Application migration suitability assessment is a critical process in modern IT infrastructure management. It determines the feasibility and optimal strategy for moving an application from its current environment to a new one, such as from on-premises infrastructure to the cloud, or between different cloud providers. This assessment considers various factors to minimize risks, reduce costs, and maximize the benefits of migration.
Definition of Application Migration Suitability
Application migration suitability, at its core, is the evaluation of an application’s characteristics to determine its readiness and optimal approach for relocation. This evaluation involves analyzing an application’s technical architecture, dependencies, performance requirements, security posture, and business criticality. The outcome of this assessment guides the selection of the most appropriate migration strategy, such as rehosting (lift-and-shift), replatforming, refactoring, or rearchitecting, as well as identifying potential challenges and mitigation strategies.
Primary Goals of Assessing Application Migration Suitability
The primary goals of assessing application migration suitability are multifaceted and aim to ensure a successful and efficient migration process.
- Minimize Risk: Accurately assessing suitability helps identify potential risks associated with migrating an application. This includes technical risks, such as compatibility issues and performance degradation, as well as operational risks, such as downtime and data loss. By identifying these risks early, organizations can develop mitigation strategies to minimize their impact. For example, if an application relies heavily on legacy code that is incompatible with the target environment, the assessment would flag this, prompting the organization to consider refactoring or rearchitecting the application before migration.
- Reduce Costs: A thorough suitability assessment can help optimize migration costs. By understanding an application’s resource requirements and dependencies, organizations can choose the most cost-effective migration strategy and target environment. For instance, if an application is highly optimized for on-premises hardware, a lift-and-shift approach to the cloud might be the most cost-effective solution initially. Conversely, if an application requires significant performance improvements, refactoring or rearchitecting could prove more cost-effective in the long run by reducing operational expenses.
- Maximize Benefits: Assessing suitability helps organizations capitalize on the benefits of migration, such as improved scalability, agility, and innovation. By understanding an application’s capabilities and limitations, organizations can select the migration strategy that best aligns with their business goals. For example, an application that is easily containerized and designed for microservices could benefit significantly from being migrated to a cloud-native platform, allowing for rapid scaling and deployment.
- Optimize Performance: The assessment helps identify performance bottlenecks and areas for optimization. Understanding the application’s resource consumption and performance characteristics allows organizations to choose the right infrastructure and configuration to ensure optimal performance in the new environment. This includes selecting the appropriate compute instances, storage solutions, and network configurations.
Key Benefits of Accurately Classifying Applications for Migration
Accurately classifying applications for migration offers several key benefits that contribute to a successful and efficient migration process.
- Informed Decision-Making: Classification provides a comprehensive understanding of each application, enabling informed decisions about the migration strategy. This includes selecting the appropriate migration approach (e.g., rehost, replatform, refactor), choosing the optimal target environment, and estimating the associated costs and timelines. For example, a financial institution migrating its core banking system would need to carefully classify the application, considering factors like data security, regulatory compliance, and performance requirements.
The classification would inform the decision to potentially refactor the application to ensure compatibility with the new cloud environment while maintaining stringent security protocols.
- Improved Resource Allocation: Accurate classification allows for efficient allocation of resources, including budget, personnel, and infrastructure. By understanding the specific requirements of each application, organizations can prioritize migration efforts and allocate resources accordingly. This prevents overspending on unnecessary infrastructure or under-resourcing critical applications. A practical example involves a retail company migrating its e-commerce platform. Classifying the application would reveal its high availability and scalability requirements, prompting the organization to allocate resources for a robust cloud infrastructure that can handle peak traffic during sales events.
- Enhanced Risk Management: Classification facilitates proactive risk management by identifying potential challenges and vulnerabilities associated with each application. This allows organizations to develop mitigation strategies and contingency plans to minimize the impact of migration-related risks. Consider a healthcare provider migrating its patient records system. Classification would highlight the importance of data privacy and security, leading the organization to implement robust encryption and access control measures to protect sensitive patient information during and after the migration.
- Increased Migration Speed: By streamlining the migration process and reducing the likelihood of unexpected issues, accurate classification contributes to a faster migration timeline. This can result in quicker realization of the benefits of migration, such as cost savings, improved performance, and enhanced agility. An example is a software company migrating its customer relationship management (CRM) system. Through proper classification, the company can identify dependencies and potential integration issues early on, enabling a more efficient migration process and allowing the company to quickly take advantage of the cloud-based CRM features.
Identifying Application Characteristics for Assessment
Assessing application characteristics is a critical step in determining migration suitability. This involves a thorough examination of various attributes to understand the application’s complexity, dependencies, and potential challenges during migration. This analysis informs the choice of migration strategy, the resources required, and the overall risk associated with the migration project.
Critical Application Characteristics for Evaluation
Evaluating application characteristics requires a systematic approach, considering several factors. This structured evaluation ensures a comprehensive understanding of the application’s suitability for migration.
- Application Architecture: The architectural design significantly impacts migration complexity. Monolithic applications, for instance, might necessitate a complete rewrite or significant refactoring for cloud-native environments, while microservices architectures offer greater flexibility.
- Technology Stack: The programming languages, frameworks, and databases used by the application are crucial. Legacy technologies might pose compatibility issues in modern cloud environments, requiring careful consideration of migration options, such as re-platforming or refactoring.
- Data Storage and Management: The way the application stores, accesses, and manages data is a key factor. Considerations include data volume, data security requirements, data governance policies, and the compatibility of the current database system with the target environment.
- Dependencies: Applications often rely on external services, libraries, and other applications. Identifying and understanding these dependencies is essential for planning the migration strategy. This includes both internal and external dependencies, as well as any third-party integrations.
- Performance Requirements: Understanding the application’s performance characteristics, such as response times, throughput, and scalability needs, is critical. This information helps determine the appropriate target environment and ensures the migrated application meets performance expectations.
- Security and Compliance: Applications must comply with security and regulatory requirements. The assessment should evaluate the application’s security posture, including authentication, authorization, and data encryption. Compliance requirements, such as GDPR or HIPAA, must also be considered.
- Business Impact: Understanding the application’s importance to the business and its impact on operations is essential. This includes assessing the criticality of the application, its user base, and the potential impact of downtime during the migration process.
- Operational Considerations: The application’s operational characteristics, such as monitoring, logging, and backup/recovery procedures, must be evaluated. These factors are crucial for ensuring the migrated application is manageable and maintainable in the target environment.
Application Architectures and Their Relevance to Migration
Different application architectures present varying levels of complexity and suitability for migration. The architecture significantly influences the choice of migration strategy and the effort involved.
- Monolithic Architecture: In this architecture, all application components are tightly coupled and deployed as a single unit. Migrating a monolithic application can be challenging. Options include:
- Rehosting (Lift and Shift): Moving the entire application to a new infrastructure with minimal changes. This is often the quickest approach but may not fully leverage cloud benefits.
- Replatforming: Making minor changes to the application to leverage cloud features, such as moving to a new database or operating system.
- Refactoring: Restructuring and optimizing the application code without changing its functionality.
- Re-architecting: Redesigning the application to adopt a microservices architecture, enabling greater scalability and flexibility. This is the most complex approach but offers the most benefits.
Example: A legacy Java application deployed on-premises might be rehosted to a virtual machine in the cloud for a quick migration, or refactored to utilize cloud-native services like managed databases and object storage.
- Microservices Architecture: This architecture comprises small, independent services that communicate over a network. Microservices architectures are generally more suitable for cloud migration due to their inherent scalability and flexibility. Migration strategies include:
- Containerization: Packaging each microservice into a container (e.g., Docker) for easy deployment and portability.
- Orchestration: Using container orchestration platforms (e.g., Kubernetes) to manage the deployment, scaling, and operation of microservices.
- Service Mesh: Implementing a service mesh (e.g., Istio, Linkerd) to manage service-to-service communication, security, and observability.
Example: An e-commerce platform built with microservices, where services like product catalog, shopping cart, and payment processing are independently deployable and scalable. Each service can be migrated independently to a cloud environment.
- Serverless Architecture: This architecture allows developers to build and run applications without managing servers. Serverless applications are highly scalable and cost-effective. Migration strategies include:
- Function as a Service (FaaS): Migrating application logic to serverless functions (e.g., AWS Lambda, Azure Functions, Google Cloud Functions).
- Managed Services: Leveraging managed services for databases, storage, and other infrastructure components.
Example: A web application that uses serverless functions to process image uploads and store them in cloud storage.
Assessing Application Dependencies
Identifying and analyzing application dependencies is crucial for a successful migration. This process involves mapping all internal and external dependencies to understand the impact of the migration on each component.
- Dependency Mapping: Creating a comprehensive map of all dependencies, including:
- Internal Dependencies: Components and modules within the application itself.
- External Dependencies: Services, APIs, libraries, and databases that the application relies on.
- Third-Party Integrations: Connections to external services provided by third-party vendors.
- Dependency Analysis: Evaluating each dependency to determine its:
- Compatibility: Assessing whether the dependency is compatible with the target environment.
- Availability: Ensuring the dependency is available and accessible in the target environment.
- Performance: Evaluating the performance impact of the dependency on the application.
- Cost: Estimating the cost of using the dependency in the target environment.
- Dependency Management: Developing a plan to manage dependencies during and after the migration:
- Re-platforming: Migrating dependencies to compatible versions in the target environment.
- Replacement: Replacing dependencies with alternative solutions that are compatible with the target environment.
- Integration: Integrating the application with existing dependencies in the target environment.
Example:Consider an application that relies on an on-premises database, a third-party payment gateway, and several internal APIs.
The dependency mapping would identify the database, the payment gateway, and each API.
The analysis would assess the compatibility of the database with the cloud environment (e.g., is there a managed database service that supports the same database type?), the availability and security of the payment gateway in the cloud, and the performance of each API after migration.
Dependency management might involve migrating the database to a managed service, ensuring the payment gateway integrates seamlessly with the cloud environment, and refactoring the APIs to optimize performance in the cloud.
Evaluating Business Requirements and Objectives

The successful migration of an application hinges not only on technical feasibility but also on a deep understanding of its impact on the business. This involves a rigorous evaluation of how the migration aligns with the organization’s strategic goals and objectives, including considerations of cost, performance, scalability, and risk. A thorough assessment helps prioritize applications for migration and ensures that the chosen migration strategy maximizes business value.
Assessing Business Impact of Application Migration
Understanding the potential business impact is critical for making informed migration decisions. This assessment involves quantifying the effects of migration on key business metrics.
- Revenue Generation: Migration can directly affect revenue through improved application performance, leading to increased customer satisfaction and sales. For example, a faster e-commerce platform can translate into more transactions and higher revenue. Conversely, downtime during migration can lead to lost sales. A study by Gartner suggests that one hour of downtime can cost a business upwards of $300,000, depending on the industry and size.
- Cost Savings: Migration to cloud environments often promises cost reductions. This can be achieved through reduced infrastructure costs, decreased operational expenses, and optimized resource utilization. Cost savings can be realized through various strategies, including leveraging pay-as-you-go pricing models and eliminating the need for on-premises hardware maintenance.
- Operational Efficiency: Migrating applications can streamline operational processes. This can result in reduced manual effort, improved automation, and faster time-to-market for new features and services. For example, automating deployment processes can reduce the time required to deploy new application versions, leading to greater agility.
- Risk Mitigation: Migration can also mitigate risks, such as those related to security vulnerabilities, hardware obsolescence, and disaster recovery. For instance, migrating to a cloud platform with robust security features can reduce the risk of data breaches and cyberattacks.
- Compliance: Migration may impact compliance with industry regulations. Organizations must assess how the migration affects their ability to meet regulatory requirements. Cloud providers often offer services to assist with compliance, such as data encryption and audit trails.
Comparing Migration Objectives
Different migration objectives drive the selection of specific migration strategies. Each objective presents a unique set of trade-offs.
- Cost Reduction: This is often a primary driver for migration. Cost reduction can be achieved through reduced infrastructure expenses, optimized resource utilization, and the elimination of on-premises hardware maintenance. Cloud providers offer various pricing models, such as pay-as-you-go, reserved instances, and spot instances, to facilitate cost optimization. A study by the Cloud Security Alliance found that cloud adoption can reduce IT infrastructure costs by up to 30%.
- Scalability: Migrating to a cloud environment can enhance scalability, allowing applications to dynamically scale up or down based on demand. This is particularly important for applications with fluctuating workloads. Auto-scaling features in cloud platforms enable organizations to automatically adjust resources to meet changing demands, ensuring optimal performance and cost efficiency.
- Performance Improvement: Migrating to a modern infrastructure can improve application performance. This can be achieved through faster processing speeds, reduced latency, and improved responsiveness. Cloud providers offer a wide range of compute, storage, and networking options that can be tailored to meet specific performance requirements. Content Delivery Networks (CDNs) can be used to cache content closer to users, reducing latency and improving application responsiveness.
- Business Agility: Migration can increase business agility by enabling faster deployment of new features and services. This can be achieved through automation, streamlined development processes, and improved collaboration. Cloud platforms offer a variety of tools and services that facilitate agile development methodologies, such as DevOps and CI/CD pipelines.
- Disaster Recovery and Business Continuity: Migration can improve disaster recovery and business continuity capabilities. Cloud platforms offer features such as automated backups, replication, and failover mechanisms, enabling organizations to quickly recover from outages and minimize downtime.
Identifying Critical Business Requirements
The critical business requirements significantly influence the application migration decisions. These requirements must be carefully considered during the assessment phase.
- Performance Requirements: These define the acceptable levels of application performance, including response times, throughput, and availability. Applications with stringent performance requirements may require specific infrastructure configurations and migration strategies to ensure optimal performance in the target environment. For example, applications that handle real-time transactions may require low-latency networking and high-performance storage.
- Security Requirements: Security requirements are paramount. These encompass data protection, access control, and compliance with industry regulations. The migration strategy must address security concerns, such as data encryption, vulnerability management, and identity and access management. For instance, applications that handle sensitive customer data must adhere to strict security protocols, such as those mandated by the Payment Card Industry Data Security Standard (PCI DSS).
- Compliance Requirements: These are dictated by industry regulations and legal requirements. The migration strategy must ensure that the application and its data remain compliant with relevant regulations, such as GDPR, HIPAA, or SOX. Cloud providers often offer compliance certifications and tools to help organizations meet their compliance obligations.
- Availability Requirements: These define the desired level of application uptime and availability. Applications with high availability requirements may need to be deployed across multiple availability zones or regions to ensure resilience against outages. High availability requirements often necessitate the use of redundant infrastructure components and automated failover mechanisms.
- Cost Constraints: Migration projects must be aligned with budgetary constraints. Cost optimization is a key consideration, and the migration strategy must balance cost savings with other objectives, such as performance and security. Organizations should carefully evaluate the total cost of ownership (TCO) of the migration, including infrastructure costs, operational expenses, and migration-related costs.
- Integration Requirements: Applications often need to integrate with other systems and services. The migration strategy must consider integration requirements, ensuring that the application can seamlessly interact with existing systems in the target environment. This may involve the use of APIs, message queues, or other integration technologies.
Technical Assessment

Assessing the technical aspects of application migration suitability is critical to ensure the chosen target platform can effectively support the application’s functionality, performance, and security requirements. This involves a detailed examination of the application’s dependencies on the underlying infrastructure and its compatibility with the proposed target environment. A comprehensive technical assessment minimizes risks and informs the selection of the most appropriate migration strategy.
Infrastructure Compatibility
Determining the compatibility of the application’s infrastructure with the target platform is a multi-faceted process. It involves analyzing the application’s current infrastructure footprint, including operating systems, networking configurations, storage solutions, and middleware components, and comparing these with the capabilities of the target environment.
- Operating System Compatibility: Evaluate the compatibility of the application with the target operating system. Consider factors such as the application’s reliance on specific system libraries, drivers, and APIs. For example, an application designed for Windows Server 2012 might not be directly compatible with a Linux-based PaaS environment without significant code modifications or the use of compatibility layers like Wine.
- Networking Requirements: Analyze the application’s network configuration, including firewall rules, load balancing, and network protocols. Ensure the target platform supports these configurations and offers similar performance characteristics. For instance, if an application relies on specific IP addresses or network port ranges, the target environment must accommodate these requirements.
- Storage Solutions: Assess the application’s storage needs, including the type and size of storage required, data access patterns, and backup and recovery requirements. The target platform should provide storage options that meet these needs, considering factors such as performance (e.g., IOPS), capacity, and cost.
- Middleware and Dependencies: Identify all middleware components, such as application servers, message queues, and caching solutions, that the application relies on. Verify that the target platform supports these components or offers equivalent alternatives. For example, an application using Apache Tomcat needs to ensure a compatible version or a functionally equivalent container is available on the target environment.
- Security Considerations: Evaluate the application’s security posture, including authentication, authorization, and encryption mechanisms. The target platform must provide security features and services that meet or exceed the application’s security requirements. This includes considering the availability of security groups, network security, and compliance with relevant industry standards.
Database Compatibility Evaluation
Database compatibility is a critical aspect of application migration. A systematic approach is needed to assess database compatibility with the target environment.
- Database Schema Analysis: Perform a thorough analysis of the database schema, including data types, constraints, indexes, and stored procedures. This analysis helps identify potential compatibility issues with the target database system. For example, a database using proprietary data types or complex stored procedures might require significant modifications to function correctly on a different database platform.
- Data Migration Strategies: Determine the most appropriate data migration strategy, considering factors such as data volume, downtime tolerance, and data transformation requirements. This might involve using tools for data extraction, transformation, and loading (ETL) or leveraging native database migration utilities.
- Database Performance Testing: Conduct performance testing to ensure the target database environment meets the application’s performance requirements. This involves measuring metrics such as query response times, transaction throughput, and resource utilization.
- Database Connectivity and Drivers: Verify the availability and compatibility of database drivers and connectivity options in the target environment. The application needs to be able to connect to the target database using a supported driver and configuration.
- Data Security and Compliance: Assess the target database’s security features and compliance with relevant regulations. This includes data encryption, access controls, and audit logging.
Infrastructure Option Comparison
Choosing the right infrastructure option (IaaS, PaaS, or SaaS) is crucial for a successful application migration. Each option offers different levels of control, management overhead, and cost.
| Infrastructure Option | Description | Pros | Cons | Suitability Considerations |
|---|---|---|---|---|
| Infrastructure as a Service (IaaS) | Provides virtualized computing resources over the internet. |
|
|
|
| Platform as a Service (PaaS) | Provides a complete development and deployment environment in the cloud. |
|
|
|
| Software as a Service (SaaS) | Delivers software applications over the internet. |
|
|
|
Assessing Code and Data Complexity
Evaluating code and data complexity is crucial for determining the effort, cost, and risks associated with application migration. Complex applications often require more sophisticated migration strategies and can present significant challenges. A thorough assessment helps in selecting the appropriate migration approach, whether it’s rehosting, refactoring, or replatforming. This section provides a guide for evaluating code and data complexity.
Evaluating Application Code Complexity
Assessing code complexity involves examining various factors that contribute to the difficulty of understanding, maintaining, and migrating the application’s codebase. These factors influence the overall effort required for migration.
- Code Size: The volume of code, typically measured in lines of code (LOC), directly impacts complexity. Larger codebases generally imply higher complexity. However, LOC alone is not a definitive measure, as code style and efficiency vary.
- Code Structure: The organization and modularity of the code significantly affect complexity. Well-structured code with clear separation of concerns is easier to understand and migrate. Poorly structured code, with extensive use of “spaghetti code,” presents a greater challenge.
- Cyclomatic Complexity: Cyclomatic complexity measures the number of linearly independent paths through a code segment. Higher cyclomatic complexity indicates more complex logic and a greater risk of errors. Tools like SonarQube and PMD can be used to calculate cyclomatic complexity.
Cyclomatic Complexity = E – N + 2P
Where:
E = the number of edges in the control flow graph
N = the number of nodes in the control flow graph
P = the number of connected components (typically 1 for a single program)For example, a function with a cyclomatic complexity of 10 has ten different paths through its code. Migrating such code requires a careful analysis of each path.
- Code Dependencies: The relationships between different code modules and external libraries influence complexity. High coupling (dependencies between modules) and low cohesion (modules not focused on a single task) increase complexity. Identifying and managing dependencies is crucial for successful migration.
- Use of Obsolete Technologies: Code written using outdated programming languages, frameworks, or libraries adds to the complexity. Migration may involve translating the code to a modern technology stack, which can be time-consuming and require specialized expertise.
- Code Comments and Documentation: The presence and quality of code comments and documentation impact understandability. Well-documented code is easier to migrate. Lack of documentation increases the risk of misinterpretation and errors during the migration process.
- Error Handling and Exception Handling: Robust error handling is essential, but complex error-handling mechanisms can increase complexity. Thoroughly understanding and migrating these mechanisms is vital for ensuring application stability post-migration.
Assessing Application Data Size and Structure
Data complexity is determined by the size, structure, and interrelationships of the data managed by the application. Evaluating data complexity is essential for selecting appropriate migration strategies and ensuring data integrity.
- Data Volume: The total amount of data, measured in terabytes or petabytes, significantly impacts the migration process. Large datasets require robust data transfer and storage solutions.
- Data Structure: The organization of data, whether it’s structured (e.g., relational databases), semi-structured (e.g., JSON, XML), or unstructured (e.g., text documents, images), influences migration complexity. Structured data is typically easier to migrate than unstructured data.
- Database Schema Complexity: The complexity of the database schema, including the number of tables, relationships between tables, and the use of complex data types, affects migration effort. Highly complex schemas may require significant schema transformation during migration.
- Data Relationships: The relationships between different data elements, such as foreign keys and referential integrity constraints, impact migration complexity. Preserving data relationships is critical for maintaining data consistency.
- Data Quality: The accuracy, completeness, consistency, and validity of the data influence migration effort. Poor data quality can lead to data cleansing requirements and increased migration time.
- Data Security and Compliance: Data security and compliance requirements, such as GDPR or HIPAA, can increase the complexity of data migration. Compliance mandates may dictate specific data storage and access controls.
- Data Transformation Requirements: The need to transform data during migration, such as converting data formats or mapping data fields, adds to complexity. Data transformation can be time-consuming and error-prone.
Complex Code and Data Scenarios and Migration Implications
Certain code and data characteristics present significant challenges during migration. Understanding these scenarios allows for proactive planning and the selection of suitable migration strategies.
- Scenario 1: Legacy Monolithic Applications with High Code Complexity
Description: A large, monolithic application with high cyclomatic complexity, numerous dependencies, and extensive use of obsolete technologies.
Migration Implications: This type of application is best suited for re-architecting or replatforming. The migration effort is likely to be substantial, requiring code refactoring, dependency management, and potentially a complete rewrite of parts of the application. The migration may involve breaking down the monolith into microservices or moving the application to a cloud-native architecture. A phased approach is often recommended to mitigate risk.
- Scenario 2: Complex Database Schemas with Large Data Volumes
Description: A database with a complex schema, numerous tables, intricate relationships, and a very large data volume (e.g., hundreds of terabytes).
Migration Implications: Migrating such data may require specialized tools and techniques for data transfer and transformation. Strategies include using database-specific migration tools, implementing data compression, and performing the migration in batches. Careful planning is needed to minimize downtime and ensure data consistency. The choice of target database technology (e.g., from on-premises to cloud) depends on business needs.
- Scenario 3: Applications with Deeply Embedded Third-Party Libraries
Description: An application heavily reliant on third-party libraries and frameworks, particularly those that are no longer supported or have compatibility issues with the target environment.
Migration Implications: This situation requires careful dependency management and potentially replacing or refactoring code that utilizes the outdated libraries. Identifying and testing the compatibility of all dependencies with the target environment is crucial. Migration might involve rewriting sections of the application to use modern, supported libraries, which can increase complexity and effort.
- Scenario 4: Applications with Extensive Custom Code and Logic
Description: Applications with significant amounts of custom code, particularly those that implement highly specific business logic or complex algorithms.
Migration Implications: The custom code needs to be thoroughly analyzed and potentially rewritten or adapted for the target environment. This requires detailed documentation and a deep understanding of the application’s functionality. The migration may involve extensive testing and validation to ensure the application behaves as expected post-migration. Consider using automated testing tools to streamline the process.
- Scenario 5: Applications with Real-Time Data Processing and Low Latency Requirements
Description: Applications that process real-time data streams and have strict latency requirements, such as financial trading systems or IoT applications.
Migration Implications: Migrating these applications demands careful consideration of network latency, data transfer speed, and the performance of the target environment. The migration strategy should prioritize minimal downtime and ensure the application can maintain its real-time processing capabilities. Consider cloud-based solutions with high-performance computing and low-latency networking to support real-time data processing. Data streaming technologies may be needed.
Security and Compliance Considerations
Application migration suitability is profoundly impacted by security and compliance requirements. Ensuring data protection, adhering to regulatory mandates, and maintaining operational integrity are paramount during the migration process. A comprehensive evaluation of these aspects is crucial for mitigating risks and ensuring a successful transition. This section explores the critical elements of security and compliance in application migration, offering a framework for informed decision-making.
The Role of Security in Application Migration Suitability
Security considerations are integral to determining application migration suitability. A robust security posture is not just a technical requirement but a business imperative. Migrating an application without adequately addressing security vulnerabilities can expose sensitive data, disrupt operations, and damage an organization’s reputation. Therefore, a thorough security assessment is crucial.
- Data Protection: Migrating applications necessitates the careful handling of sensitive data. This includes data at rest, in transit, and in use. Security measures must be implemented to prevent unauthorized access, data breaches, and data loss. For example, if an application handles Personally Identifiable Information (PII), the migration strategy must include robust encryption, access controls, and data masking techniques.
- Threat Landscape: Applications are constantly exposed to evolving cyber threats. The migration process provides an opportunity to address existing vulnerabilities and incorporate enhanced security measures. This involves identifying potential attack vectors, such as SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks, and implementing appropriate security controls.
- Compliance Adherence: Security practices must align with relevant compliance regulations. Failing to comply with these regulations can result in significant financial penalties, legal liabilities, and reputational damage.
- Business Continuity: Security incidents can disrupt business operations. The migration strategy should include plans for incident response, disaster recovery, and business continuity to minimize the impact of security breaches.
Relevant Compliance Regulations that Affect Application Migration Decisions
Numerous compliance regulations influence application migration decisions, dictating specific security requirements and data handling practices. Understanding these regulations is essential for determining the feasibility and suitability of a migration strategy. Failure to comply with these regulations can lead to substantial legal and financial repercussions.
- General Data Protection Regulation (GDPR): GDPR, applicable to organizations that process the personal data of individuals within the European Union (EU), mandates strict requirements for data protection, including consent, data minimization, and the right to be forgotten. During migration, organizations must ensure compliance with GDPR principles, such as pseudonymization and encryption of personal data.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA, relevant to the healthcare industry in the United States, sets standards for protecting patient health information (PHI). Migrating applications that handle PHI requires implementing stringent security measures, including access controls, audit trails, and data encryption. For instance, a healthcare provider migrating its patient portal to the cloud must ensure that the cloud provider complies with HIPAA regulations.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS applies to organizations that process credit card data. Migration projects involving payment processing applications must adhere to PCI DSS requirements, which include secure network configurations, data encryption, and vulnerability management.
- California Consumer Privacy Act (CCPA): CCPA, effective in California, grants consumers rights regarding their personal data. Organizations migrating applications that handle consumer data must comply with CCPA requirements, such as providing consumers with the right to access, delete, and opt-out of the sale of their personal information.
- Sarbanes-Oxley Act (SOX): SOX, relevant to publicly traded companies in the United States, mandates requirements for financial reporting and internal controls. Migrating financial applications requires careful consideration of SOX compliance, including access controls, audit trails, and data integrity measures.
Methods for Assessing the Security Posture of Applications Before Migration
A comprehensive security assessment is essential before migrating an application. This assessment helps identify vulnerabilities, assess risks, and inform the migration strategy. Various methods can be employed to evaluate the security posture of an application.
- Vulnerability Scanning: Vulnerability scanning involves using automated tools to identify known security vulnerabilities in the application’s code, infrastructure, and dependencies. These tools analyze the application for common weaknesses, such as outdated software versions, misconfigurations, and coding errors. A vulnerability scan might reveal that an application uses an outdated version of a web server with known security flaws.
- Penetration Testing: Penetration testing, or “pen testing,” simulates real-world cyberattacks to identify security weaknesses. Ethical hackers attempt to exploit vulnerabilities in the application to assess the effectiveness of existing security controls. Pen testing can uncover vulnerabilities that automated scanning tools may miss, such as logic flaws or misconfigured access controls.
- Static Code Analysis: Static code analysis involves examining the application’s source code to identify potential security vulnerabilities. This method analyzes the code without executing it, identifying issues such as buffer overflows, SQL injection vulnerabilities, and insecure coding practices. For example, static code analysis might detect a hardcoded password in the application’s source code.
- Dynamic Application Security Testing (DAST): DAST involves testing the application while it is running to identify security vulnerabilities. DAST tools simulate user interactions and attempt to exploit vulnerabilities in real-time. This approach can identify vulnerabilities that may not be apparent during static code analysis.
- Security Audits: Security audits involve a comprehensive review of the application’s security controls, policies, and procedures. These audits are often conducted by independent security experts to assess the overall security posture of the application. The audit might assess the effectiveness of access controls, data encryption, and incident response plans.
- Threat Modeling: Threat modeling involves identifying potential threats to the application and assessing the associated risks. This process helps prioritize security efforts and develop appropriate mitigation strategies. For example, threat modeling might identify the risk of a denial-of-service attack and recommend implementing measures to mitigate this risk.
Risk Assessment and Mitigation Strategies
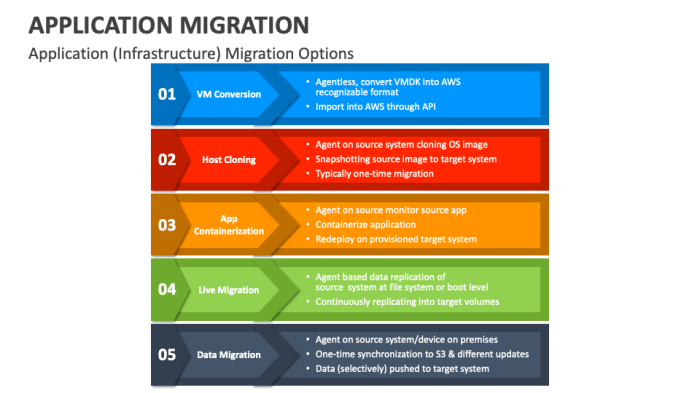
Application migration is inherently complex, introducing potential disruptions and challenges. A systematic risk assessment is crucial to proactively identify, analyze, and address these potential issues, ensuring a smoother and more successful migration process. Effective risk management minimizes negative impacts, optimizes resource allocation, and increases the likelihood of achieving the desired business outcomes.
Risk Assessment Process
The risk assessment process involves several key steps to identify and manage potential problems. This structured approach enables organizations to anticipate challenges and develop appropriate mitigation strategies.
- Risk Identification: This initial phase involves systematically identifying potential risks associated with the application migration. This can be achieved through brainstorming sessions, reviewing project documentation, consulting with stakeholders, and analyzing historical data from previous migration projects. The goal is to create a comprehensive list of potential risks.
- Risk Analysis: Once risks are identified, they must be analyzed to determine their likelihood of occurrence and potential impact. This often involves qualitative and quantitative analysis. Qualitative analysis uses subjective judgments, while quantitative analysis uses numerical data and statistical techniques. The output of this analysis is a risk score that reflects the severity of each risk.
- Risk Prioritization: Risks are then prioritized based on their risk scores. This helps in focusing resources on the most critical risks that pose the greatest threat to the project’s success. Prioritization typically involves creating a risk matrix that visualizes the likelihood and impact of each risk.
- Risk Response Planning: For each prioritized risk, a response plan is developed. This plan Artikels the specific actions that will be taken to mitigate the risk. Mitigation strategies can include avoiding the risk, transferring the risk, mitigating the risk, or accepting the risk.
- Risk Monitoring and Control: Throughout the migration process, risks must be continuously monitored and controlled. This involves tracking the status of risks, evaluating the effectiveness of mitigation strategies, and updating the risk register as needed. Regular reviews and updates ensure that the risk management plan remains relevant and effective.
Common Migration Risks and Mitigation Strategies
Application migrations are subject to a variety of risks, each requiring a tailored mitigation strategy. Understanding these risks and proactively addressing them is essential for project success.
- Data Loss or Corruption: This is a significant risk, particularly when migrating large datasets. Mitigation strategies include:
- Data Backup and Recovery: Implementing comprehensive backup and recovery procedures before, during, and after the migration.
- Data Validation: Rigorous data validation checks to ensure data integrity during the migration process. This can involve comparing data before and after the migration to identify discrepancies.
- Pilot Migrations: Conducting pilot migrations on a small scale to test data migration processes and identify potential issues before migrating the entire dataset.
- Downtime and Service Disruption: Minimizing downtime is critical to maintaining business continuity. Mitigation strategies include:
- Phased Migration: Migrating applications in phases to minimize the impact of any single outage.
- Redundancy and Failover: Implementing redundant systems and failover mechanisms to ensure that services remain available even if one system fails.
- Careful Planning and Scheduling: Meticulous planning and scheduling of migration activities, including off-peak migration windows to minimize disruption during business hours.
- Compatibility Issues: Ensuring that the migrated application is compatible with the new environment. Mitigation strategies include:
- Thorough Testing: Conducting comprehensive testing to identify and resolve compatibility issues. This includes functional testing, performance testing, and user acceptance testing.
- Environment Validation: Validating that the target environment meets the application’s requirements, including hardware, software, and network configurations.
- Code Remediation: Modifying application code to ensure compatibility with the new environment. This may involve refactoring code or updating dependencies.
- Cost Overruns: Unexpected costs can derail a migration project. Mitigation strategies include:
- Detailed Budgeting: Developing a detailed budget that includes all anticipated costs, such as labor, infrastructure, software licenses, and data migration.
- Contingency Planning: Including a contingency fund to cover unexpected expenses.
- Cost Optimization: Exploring cost-effective migration options, such as leveraging cloud services or automating migration processes.
- Security Vulnerabilities: Migrating applications can introduce new security risks. Mitigation strategies include:
- Security Assessments: Conducting security assessments to identify and address potential vulnerabilities. This includes vulnerability scanning, penetration testing, and code reviews.
- Security Hardening: Implementing security hardening measures to protect the migrated application. This may involve configuring firewalls, intrusion detection systems, and access controls.
- Compliance Adherence: Ensuring that the migrated application complies with all relevant security and compliance regulations.
Prioritizing Risks Based on Impact
Prioritizing risks is essential for allocating resources effectively. This involves assessing the potential impact of each risk and developing mitigation strategies accordingly.
Risk prioritization typically involves using a risk matrix, a visual tool that maps risks based on their likelihood of occurrence and their potential impact. The impact can be assessed based on several factors:
- Financial Impact: The potential financial loss if the risk materializes.
- Reputational Impact: The potential damage to the organization’s reputation.
- Operational Impact: The potential disruption to business operations.
- Compliance Impact: The potential for non-compliance with regulations.
The risk matrix helps in categorizing risks into different levels of priority, such as high, medium, and low. Risks with a high likelihood and a high impact are considered high-priority risks and require immediate attention. Risks with a low likelihood and a low impact are considered low-priority risks and may require less attention. The risk matrix allows for a structured and data-driven approach to risk management, enabling organizations to focus their efforts on the most critical risks.
Migration Strategies
The selection of an appropriate migration strategy is a critical decision point in the application modernization journey. Each strategy offers a unique balance of cost, time, and risk, and the optimal choice depends heavily on the application’s characteristics, business requirements, and technical constraints. A thorough understanding of these strategies is paramount for successful application migration.
Rehosting, Refactoring, Replatforming, and Retiring
Different migration strategies cater to diverse application needs. The following sections will explore these strategies and their suitability for different application types.
- Rehosting (Lift and Shift): This strategy involves moving an application to a new infrastructure environment with minimal changes to the application’s code. The primary goal is to quickly migrate the application while minimizing development effort. Rehosting often involves moving an application from an on-premises data center to a cloud environment. This approach is suitable for applications that are relatively simple, have limited dependencies, and do not require significant architectural changes.
- Refactoring: Refactoring involves restructuring the application’s code to improve its internal structure and maintainability without changing its external behavior. This may include changes to the application’s architecture, design patterns, or code quality. Refactoring is often performed to improve the application’s performance, scalability, or security. This strategy is beneficial for applications that need to be modernized but don’t require a complete rewrite.
- Replatforming: Replatforming involves making significant changes to the application’s underlying platform, such as migrating from an on-premises database to a cloud-based database or changing the operating system. This strategy aims to take advantage of the features and benefits of a new platform while retaining the core functionality of the application. Replatforming can lead to improved performance, scalability, and cost savings.
- Retiring: Retiring involves decommissioning an application and removing it from the production environment. This is often done when an application is no longer needed, its functionality is duplicated by another application, or the cost of maintaining it outweighs its value. Retiring is a viable option for applications that are outdated, underutilized, or have significant security vulnerabilities.
Advantages and Disadvantages of Rehosting Versus Refactoring
A comparison of rehosting and refactoring reveals their distinct trade-offs. The selection between these two strategies hinges on the application’s specific characteristics and business objectives.
- Rehosting Advantages:
- Speed: Rehosting is typically the fastest migration strategy because it involves minimal code changes. Applications can be migrated to the new environment quickly.
- Low Initial Cost: The initial investment in rehosting is often lower than refactoring, as it requires less development effort.
- Reduced Risk: Because the code is largely unchanged, the risk of introducing new bugs or breaking functionality is relatively low.
- Rehosting Disadvantages:
- Limited Optimization: Rehosting doesn’t optimize the application for the new environment. It may not fully leverage the benefits of the new infrastructure, such as cloud-native features.
- Potential for Performance Issues: Without code optimization, performance issues from the original environment might persist or worsen in the new environment.
- Technical Debt Transfer: Rehosting carries over existing technical debt, such as poorly written code or outdated dependencies.
- Refactoring Advantages:
- Improved Application Quality: Refactoring can improve the application’s code quality, maintainability, and scalability.
- Enhanced Performance: Refactoring can optimize the application’s performance, making it more efficient and responsive.
- Modernization Benefits: Refactoring can prepare the application for future enhancements and integration with modern technologies.
- Refactoring Disadvantages:
- Time-Consuming: Refactoring is a time-intensive process, as it requires significant code changes.
- Higher Cost: Refactoring typically involves a higher development cost than rehosting.
- Increased Risk: Introducing code changes can introduce new bugs and potentially break existing functionality.
Decision Tree for Determining the Most Appropriate Migration Strategy
A decision tree provides a structured approach to selecting the most suitable migration strategy. This analytical tool helps guide the decision-making process based on specific application characteristics and business objectives.
The decision tree follows a series of questions to determine the most suitable strategy. The process begins with assessing the application’s current state, the business’s objectives, and the technical constraints.
- Question 1: Is the primary goal to minimize disruption and quickly move the application?
- Yes: Consider Rehosting (Lift and Shift).
- No: Proceed to Question 2.
- Question 2: Does the application require significant performance improvements or modernization?
- Yes: Proceed to Question 3.
- No: Consider Rehosting (if not already chosen) or Retiring.
- Question 3: Is the application tightly coupled to its current platform?
- Yes: Consider Replatforming, evaluating if the platform change is worth the effort.
- No: Proceed to Question 4.
- Question 4: Are there specific code quality or architectural issues that need to be addressed?
- Yes: Consider Refactoring.
- No: Replatforming or Rehosting might be suitable, depending on previous answers.
- Final Decision: Based on the answers to the questions, select the migration strategy that best aligns with the application’s needs and the organization’s goals. The decision should consider the trade-offs of each strategy, including cost, time, risk, and potential benefits.
Example: An organization has an aging, on-premises application that needs to be moved to the cloud. The primary goal is to quickly reduce operational costs and improve availability. The application has limited dependencies and is relatively straightforward. Following the decision tree, the answer to Question 1 is “Yes,” indicating that rehosting is the most suitable strategy.
Tools and Technologies for Application Classification
Application classification is significantly streamlined by leveraging specialized tools and technologies. These resources automate and accelerate the assessment process, providing more accurate and efficient evaluations of migration suitability. They offer capabilities ranging from automated code analysis to dependency mapping and cost estimation, providing insights that would be difficult or time-consuming to gather manually. The effective utilization of these tools is critical for making informed decisions regarding application migration strategies.
Available Tools for Assessing Application Migration Suitability
A variety of tools exist to assist in the application classification process, each offering unique functionalities and strengths. These tools are typically categorized based on their primary focus, such as code analysis, dependency mapping, or cost estimation. Choosing the right tool or combination of tools depends on the specific requirements of the application portfolio and the overall migration goals.
- Automated Code Analysis Tools: These tools automatically scan application code to identify potential issues related to migration, such as compatibility problems, deprecated features, and code complexity. They can also provide insights into code quality and maintainability. Examples include:
- SonarQube: An open-source platform for continuous inspection of code quality. It analyzes code for bugs, vulnerabilities, code smells, and code coverage.
- CAST Highlight: A software intelligence platform that provides insights into application portfolios, including code quality, security vulnerabilities, and technical debt.
- Micro Focus Fortify: A suite of security testing tools that identifies and helps remediate security vulnerabilities in software code.
- Dependency Mapping Tools: These tools automatically discover and map dependencies between applications, services, and infrastructure components. Understanding these dependencies is crucial for planning migration order and minimizing disruption. Examples include:
- ServiceNow: A platform that provides service mapping capabilities, allowing organizations to visualize and manage dependencies between applications and services.
- AppDynamics: An application performance monitoring (APM) tool that can automatically discover and map application dependencies.
- SolarWinds Network Performance Monitor: This tool offers network performance monitoring and mapping capabilities, including dependency visualization.
- Cloud Assessment Tools: Specifically designed to evaluate the suitability of applications for cloud migration, these tools often provide cost estimation, performance analysis, and compatibility assessments. Examples include:
- AWS Migration Evaluator (formerly TSO Logic): Analyzes on-premises infrastructure and provides recommendations for cloud migration, including cost estimations.
- Azure Migrate: A service offered by Microsoft Azure that helps assess and migrate on-premises servers, applications, and data to Azure.
- Google Cloud Assessment Manager: A tool that helps assess and plan for migrating workloads to Google Cloud Platform.
- Cost Estimation Tools: These tools help estimate the costs associated with migrating and running applications in the cloud. They consider factors such as compute, storage, networking, and operational costs. Examples include:
- AWS Pricing Calculator: A web-based tool that allows users to estimate the cost of AWS services.
- Azure Pricing Calculator: A tool provided by Microsoft Azure for estimating the cost of Azure services.
- Google Cloud Pricing Calculator: A tool for estimating the cost of Google Cloud Platform services.
Technologies that Assist in Application Classification
Several technologies play a crucial role in assisting with application classification, often working in conjunction with the tools mentioned above. These technologies provide the underlying infrastructure and capabilities that enable automated analysis, data collection, and decision support.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML algorithms can automate many aspects of the classification process, such as code analysis, dependency mapping, and risk assessment. They can analyze large datasets to identify patterns, predict migration outcomes, and provide recommendations. For example, ML models can be trained to predict the likelihood of successful migration based on historical data and application characteristics.
- Containerization Technologies: Technologies like Docker and Kubernetes facilitate the packaging and deployment of applications, making them more portable and easier to migrate. Containerization simplifies the identification of application dependencies and allows for consistent execution across different environments.
- Infrastructure as Code (IaC): IaC tools, such as Terraform and Ansible, allow for the automated provisioning and management of infrastructure. This enables the rapid deployment of test environments and the consistent replication of infrastructure configurations, which is critical for testing and validating migration strategies.
- API Integration: The use of APIs to integrate various tools and services into a unified classification workflow. This allows for the seamless exchange of data and the automation of tasks across different stages of the process. For instance, an API can be used to automatically extract data from code analysis tools and feed it into a dependency mapping tool.
Role of Automation in the Application Classification Process
Automation is a key component of a successful application classification process. It significantly reduces the time and effort required for assessment, improves accuracy, and provides valuable insights that might otherwise be missed. Automation streamlines the entire process, from initial data gathering to final recommendations.
- Automated Data Collection: Automation enables the collection of data from various sources, such as code repositories, infrastructure monitoring tools, and application logs. This reduces the need for manual data gathering and minimizes the risk of human error.
- Automated Code Analysis: Automated code analysis tools can quickly identify potential migration blockers, such as incompatible libraries, deprecated features, and security vulnerabilities. This helps prioritize applications for migration and identify the need for code remediation.
- Automated Dependency Mapping: Dependency mapping tools automatically discover and visualize dependencies between applications, services, and infrastructure components. This information is crucial for planning migration order and minimizing disruption.
- Automated Risk Assessment: Automation can be used to assess the risks associated with application migration, such as security vulnerabilities, performance bottlenecks, and compatibility issues. This helps prioritize mitigation strategies and ensure a smooth transition.
- Automated Reporting and Dashboards: Automation allows for the creation of automated reports and dashboards that provide a comprehensive overview of the application portfolio. This enables stakeholders to easily track progress, identify issues, and make informed decisions.
Creating a Migration Suitability Matrix
A Migration Suitability Matrix provides a structured framework for assessing and classifying applications based on their readiness for migration. It offers a standardized approach, ensuring consistency and facilitating informed decision-making. The matrix typically incorporates various criteria, assigning scores to each based on pre-defined scales. This process streamlines the application portfolio analysis, enabling efficient prioritization and resource allocation for migration efforts.
Designing a Matrix for Classifying Applications
The design of the migration suitability matrix involves defining key assessment criteria, assigning weights to each criterion based on its importance, and establishing a scoring system. The matrix should be easily understandable, adaptable, and capable of accommodating diverse application types. A well-designed matrix promotes transparency and facilitates communication among stakeholders.The matrix’s structure should be organized for clarity and ease of use.
The following table Artikels a sample structure:
| Assessment Criteria | Description | Scoring Scale | Weighting (%) |
|---|---|---|---|
| Business Criticality | The importance of the application to the business operations, measured by its impact on revenue, customer satisfaction, and compliance. | 1 (Low) – 5 (High) | 25 |
| Technical Complexity | The intricacy of the application’s architecture, including the number of dependencies, integrations, and the use of legacy technologies. | 1 (Low) – 5 (High) | 20 |
| Code and Data Complexity | The complexity of the application’s codebase, including the size, quality, and maintainability of the code, as well as the volume and structure of the data. | 1 (Low) – 5 (High) | 15 |
| Security and Compliance | The application’s adherence to security standards and regulatory requirements, including data protection, access controls, and audit trails. | 1 (Low) – 5 (High) | 20 |
| Cost of Migration | The estimated financial resources required for the migration, including labor, tools, infrastructure, and potential downtime. | 1 (Low) – 5 (High) | 10 |
| Dependency on On-Premises Infrastructure | The degree to which the application relies on on-premises hardware, software, and network configurations. | 1 (Low) – 5 (High) | 10 |
Demonstrating How to Use the Matrix to Assign Suitability Scores
Assigning suitability scores involves evaluating each application against the defined criteria and assigning a score based on the scoring scale. The weighting assigned to each criterion determines its contribution to the overall suitability score. The process typically involves a team of experts, including application owners, architects, and security specialists, to ensure a comprehensive assessment.To illustrate, consider an example:An application, “SalesForce CRM,” is being assessed.* Business Criticality: The application is critical for managing customer relationships and driving sales.
Score: 5
Technical Complexity
The application has a well-defined architecture with a manageable number of dependencies. Score: 3
Code and Data Complexity
The application has a relatively clean codebase and a structured database. Score: 3
Security and Compliance
The application complies with industry security standards and regulations. Score: 4
Cost of Migration
The migration is estimated to be moderately expensive. Score: 3
Dependency on On-Premises Infrastructure
The application has no dependency on on-premises infrastructure. Score: 1The overall suitability score is calculated as follows:
(5
- 0.25) + (3
- 0.20) + (3
- 0.15) + (4
- 0.20) + (3
- 0.10) + (1
- 0.10) = 3.45
Based on the overall score, the application can be categorized as suitable for migration, potentially cloud-ready, or requiring further analysis. The specific thresholds for each category should be defined beforehand. For instance, a score of 4.0-5.0 might indicate “Highly Suitable,” 3.0-3.9 “Suitable,” 2.0-2.9 “Potentially Suitable with modifications,” and below 2.0 “Not Suitable.”
Documentation and Reporting for Migration Readiness
Comprehensive documentation and well-structured reporting are critical components of a successful application migration strategy. These practices provide a transparent record of the assessment process, facilitate informed decision-making, and ensure accountability throughout the migration lifecycle. Proper documentation aids in knowledge transfer, risk mitigation, and efficient execution of the migration plan.
Importance of Documentation in the Application Migration Process
Documentation serves as the foundation for effective application migration, providing a structured approach to managing the complexities inherent in the process. It ensures that all stakeholders have access to the necessary information, facilitating clear communication and collaboration.
- Comprehensive Assessment Record: Documents the application assessment findings, including identified characteristics, business requirements, technical specifications, and potential migration strategies. This record provides a detailed baseline for understanding the application’s current state and its suitability for migration.
- Risk Mitigation and Management: Captures potential risks associated with the migration, along with proposed mitigation strategies. This proactive approach enables early identification and resolution of issues, minimizing disruptions and ensuring business continuity.
- Knowledge Transfer and Retention: Serves as a repository of knowledge, documenting application architecture, dependencies, and operational procedures. This facilitates knowledge transfer between teams, reducing reliance on individual expertise and ensuring long-term maintainability.
- Decision Support: Provides the necessary information for making informed decisions about migration strategies, resource allocation, and project timelines. The documented evidence supports the selection of the most appropriate migration approach, such as rehosting, replatforming, or refactoring.
- Compliance and Auditability: Ensures compliance with regulatory requirements and industry standards. Documentation provides an auditable trail of the migration process, demonstrating adherence to best practices and facilitating audits.
- Project Management and Tracking: Supports effective project management by providing a framework for tracking progress, managing tasks, and monitoring key performance indicators (KPIs). This ensures that the migration project stays on track and within budget.
Guidelines for Creating Reports on Application Migration Readiness
Reports on application migration readiness should provide a clear, concise, and actionable summary of the assessment findings, including key risks, recommendations, and proposed migration strategies. They should be tailored to the intended audience, ranging from technical teams to business stakeholders.
- Define the Report’s Purpose and Audience: Clearly state the report’s objectives and identify the target audience (e.g., technical team, project manager, business stakeholders). This helps to tailor the content and level of detail appropriately.
- Executive Summary: Provide a concise overview of the key findings, conclusions, and recommendations. This section should enable decision-makers to quickly understand the report’s essence.
- Application Overview: Describe the application’s functionality, architecture, and key characteristics. This context helps readers understand the application’s role within the organization.
- Assessment Methodology: Artikel the assessment approach, including the tools, techniques, and criteria used to evaluate the application. This ensures transparency and reproducibility of the assessment results.
- Findings and Analysis: Present the assessment findings in a clear and organized manner, using tables, charts, and diagrams to illustrate key data points. Analyze the findings to identify strengths, weaknesses, and potential risks.
- Migration Strategy and Recommendations: Propose a recommended migration strategy based on the assessment findings. Provide detailed recommendations, including the preferred migration approach, target environment, and estimated costs.
- Risk Assessment and Mitigation: Identify potential risks associated with the migration and propose mitigation strategies. This section should include a risk register, outlining the likelihood and impact of each risk.
- Timeline and Budget: Provide an estimated timeline and budget for the migration project. This information helps stakeholders to understand the scope and cost of the project.
- Appendices: Include supporting documentation, such as detailed assessment results, technical specifications, and vendor information.
Example Report: Application Migration Readiness Assessment
This is an example report detailing key findings and recommendations. This report assesses the readiness of “Customer Relationship Management (CRM) Application” for migration to a cloud environment.
- Executive Summary: The CRM application is suitable for migration to a cloud-based platform. The assessment identified some minor technical challenges, but these are readily addressable. Replatforming the application to a Platform-as-a-Service (PaaS) environment is the recommended migration strategy.
- Application Overview: The CRM application is a web-based application used for managing customer interactions and sales processes. It utilizes a three-tier architecture (web, application, and database) and is currently hosted on-premises.
- Assessment Methodology: The assessment involved a review of the application’s architecture, code, data, security, and business requirements. Tools used included static code analysis, database profiling, and performance testing.
- Key Findings:
- Business Requirements: The CRM application supports critical business processes, including sales, marketing, and customer service. Migration to the cloud will improve scalability, availability, and cost-effectiveness.
- Technical Assessment: The application is compatible with cloud-based platforms. Some code refactoring is required to optimize performance in the new environment.
- Security and Compliance: The application meets security and compliance requirements. Data encryption and access controls are in place.
- Risk Assessment: Potential risks include data migration challenges and application downtime during migration. Mitigation strategies involve thorough testing and a phased migration approach.
- Recommendations:
- Migration Strategy: Replatform the CRM application to a PaaS environment (e.g., AWS Elastic Beanstalk or Azure App Service).
- Target Environment: Choose a PaaS environment that supports the application’s technology stack.
- Timeline: The migration is estimated to take three months, including planning, testing, and execution.
- Budget: The estimated budget for the migration is $150,000, including infrastructure costs, labor, and software licenses.
- Risk Mitigation Strategies:
- Data Migration: Develop a detailed data migration plan, including data validation and testing.
- Application Downtime: Implement a phased migration approach to minimize downtime.
- Performance Issues: Conduct performance testing in the target environment and optimize the application code as needed.
Ultimate Conclusion
In conclusion, classifying applications for migration suitability is a multifaceted endeavor that demands a holistic perspective. By systematically evaluating application attributes, business objectives, and technical considerations, organizations can chart a course toward successful migrations. The strategies, tools, and methodologies Artikeld provide a robust framework for navigating the complexities of application migration. Through careful planning, rigorous assessment, and a commitment to continuous improvement, businesses can optimize their IT infrastructure, unlock new levels of agility, and realize the full potential of their digital assets.
Query Resolution
What is the primary difference between rehosting and refactoring?
Rehosting (also known as “lift and shift”) involves moving an application to a new infrastructure with minimal code changes, while refactoring entails modifying the application’s code to optimize it for the new environment, potentially including changes to its architecture.
How does application size affect migration suitability?
Larger applications often present greater complexity, increasing the time, cost, and risk associated with migration. They may also require more detailed planning and testing.
What role does automation play in the application classification process?
Automation streamlines the assessment process by identifying dependencies, analyzing code, and generating reports, thereby accelerating decision-making and reducing manual effort.
What are the key considerations for database migration?
Database migration requires assessing compatibility with the target environment, data volume, schema complexity, and the need for data transformation or conversion. Considerations for downtime during migration also apply.