Embarking on the journey of ISO 27001 certification is a significant step towards bolstering your organization’s information security posture. This guide provides a clear roadmap, offering a detailed overview of the entire process, from understanding the fundamental principles of ISO 27001 to maintaining your certification and fostering continuous improvement. We’ll navigate the essential steps, key components, and best practices to help you achieve and sustain this globally recognized standard.
This Artikel will cover everything you need to know, including prerequisites, the certification process, selecting a certification body, developing and implementing an Information Security Management System (ISMS), and maintaining your certification. We’ll also delve into the importance of documentation, internal audits, and management reviews. This comprehensive approach will equip you with the knowledge and tools necessary to navigate the complexities of ISO 27001 certification effectively.
Understanding ISO 27001
ISO 27001 is the internationally recognized standard for Information Security Management Systems (ISMS). It provides a framework for establishing, implementing, maintaining, and continually improving an organization’s information security. This standard helps organizations manage and protect their valuable information assets, ensuring confidentiality, integrity, and availability.
Core Principles of ISO 27001 and its Purpose
ISO 27001’s core principles center on a risk-based approach to information security. This means organizations identify, assess, and treat information security risks specific to their operations. The standard’s purpose is to provide a structured approach to managing sensitive information so that it remains secure.The key principles include:
- Confidentiality: Ensuring that information is accessible only to authorized individuals. For example, employee payroll information is only accessible to authorized HR and finance personnel.
- Integrity: Maintaining the accuracy and completeness of information. An example of this is protecting financial records from unauthorized alteration.
- Availability: Ensuring that information and systems are accessible when needed. A website remaining online during peak traffic periods is a demonstration of availability.
- Risk Management: The systematic identification, assessment, and treatment of information security risks.
- Continual Improvement: Regularly reviewing and enhancing the ISMS to adapt to changing threats and business needs.
Definition of an Information Security Management System (ISMS)
An Information Security Management System (ISMS) is a systematic and documented approach to managing sensitive company information so that it remains secure. It encompasses a set of policies, procedures, and controls designed to manage information security risks.An ISMS, within the context of ISO 27001, provides a structured framework for:
- Defining the scope of the ISMS.
- Conducting a risk assessment.
- Selecting and implementing security controls.
- Monitoring and measuring the effectiveness of the controls.
- Continually improving the ISMS.
The ISMS helps organizations protect their information assets, reduce the likelihood of security incidents, and meet legal and regulatory requirements.
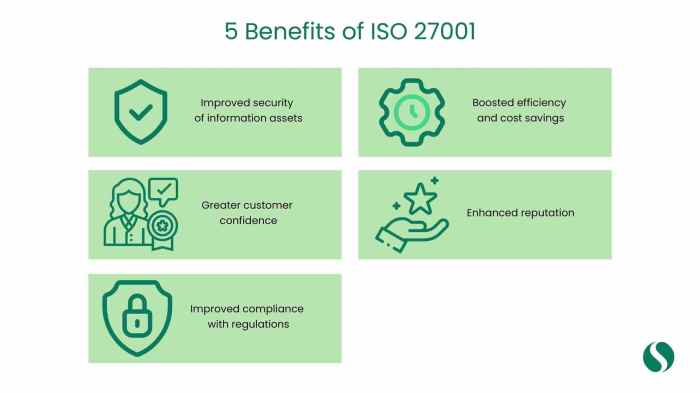
Benefits of ISO 27001 Certification
Achieving ISO 27001 certification offers a multitude of benefits to an organization, both tangible and intangible. It demonstrates a commitment to information security and can significantly enhance an organization’s reputation and operational efficiency.The benefits include:
- Enhanced Security Posture: ISO 27001 certification helps organizations identify and mitigate information security risks, leading to a stronger security posture. For instance, a company might reduce the number of successful phishing attacks after implementing ISO 27001 controls.
- Improved Customer Trust and Confidence: Certification signals to customers, partners, and stakeholders that the organization takes information security seriously. This builds trust and can lead to increased business opportunities.
- Compliance with Legal and Regulatory Requirements: ISO 27001 helps organizations comply with various data protection laws and regulations, such as GDPR, by providing a framework for managing sensitive information.
- Competitive Advantage: Certification can differentiate an organization from competitors, particularly in industries where information security is a critical factor. For example, in the financial sector, ISO 27001 certification is often a prerequisite for doing business.
- Reduced Risk of Data Breaches and Security Incidents: By implementing and maintaining an ISMS, organizations can significantly reduce the likelihood of data breaches and other security incidents. A real-world example includes a 30% reduction in security incidents reported by a certified organization.
- Cost Savings: While there are costs associated with implementing and maintaining an ISMS, the benefits often outweigh the expenses. Organizations can reduce costs related to data breaches, legal fees, and reputational damage.
- Improved Operational Efficiency: The implementation of an ISMS can streamline security processes, reduce redundancies, and improve overall operational efficiency.
- Better Management of Information Security Risks: The ISO 27001 framework provides a systematic approach to identifying, assessing, and managing information security risks, which can lead to a more proactive and effective risk management program.
Prerequisites for Certification
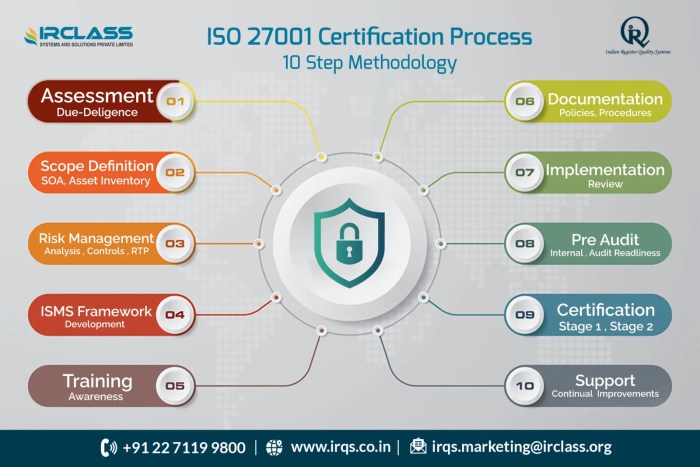
Achieving ISO 27001 certification is a significant undertaking, demonstrating an organization’s commitment to information security. Before embarking on this journey, several prerequisites must be met to ensure a successful certification process. These prerequisites lay the groundwork for a robust Information Security Management System (ISMS) and ensure the organization is prepared for the rigorous audit process.
Eligibility Requirements
Organizations of all sizes and types, whether public, private, or non-profit, are eligible for ISO 27001 certification. However, there are fundamental requirements that must be in place.
- Scope Definition: The organization must clearly define the scope of its ISMS. This involves identifying the boundaries of the system, specifying the assets, processes, and locations covered by the ISMS. A well-defined scope is crucial for focusing the certification effort and ensuring the ISMS addresses the relevant information security risks. For example, a financial institution might include all its core banking systems and customer data within the scope, while excluding less critical internal systems.
- Commitment from Top Management: Demonstrable commitment from top management is essential. This includes providing resources (financial, human, and technological), setting the strategic direction for information security, and actively participating in the ISMS. Management commitment is vital for fostering a security-conscious culture throughout the organization. Without this, the ISMS will likely fail to gain traction and effectiveness.
- Established ISMS: The organization must have an established and operational ISMS. This involves implementing the necessary controls based on the chosen risk assessment methodology and the requirements of ISO 27001. This includes creating and implementing policies, procedures, and documented information (records) related to information security.
- Risk Assessment and Treatment: A documented risk assessment process must be in place, including identifying information security risks, analyzing their likelihood and impact, and developing a risk treatment plan. Risk treatment options typically include avoidance, transfer, mitigation, or acceptance. The chosen treatment options must be documented and implemented.
- Internal Audit: The organization must conduct internal audits to assess the effectiveness of its ISMS. These audits should be performed by qualified individuals who are independent of the activities being audited. The findings of the internal audits must be documented and used to drive improvements to the ISMS.
- Management Review: Top management must regularly review the ISMS to ensure its suitability, adequacy, and effectiveness. This review should cover the results of internal audits, feedback from interested parties, risk assessment results, and other relevant information. The management review should result in decisions and actions to improve the ISMS.
Importance of a Gap Analysis
A gap analysis is a critical step in preparing for ISO 27001 certification. It involves comparing the organization’s current information security practices against the requirements of the standard to identify any gaps or areas where the organization falls short.
- Identifying Deficiencies: A gap analysis pinpoints areas where the organization’s current security controls and practices are insufficient to meet the requirements of ISO 27001. This might include missing policies, inadequate procedures, or a lack of appropriate security controls.
- Prioritizing Remediation Efforts: The gap analysis helps prioritize remediation efforts by highlighting the most significant gaps. Organizations can then focus their resources on addressing the most critical deficiencies first, based on the level of risk they pose.
- Creating a Roadmap for Implementation: The gap analysis provides a roadmap for implementing the ISMS. It identifies the specific actions that need to be taken to achieve compliance with ISO 27001. This roadmap can include a timeline, resource allocation, and assignment of responsibilities.
- Improving Efficiency and Reducing Costs: By identifying and addressing gaps proactively, organizations can avoid costly mistakes and rework during the certification process. It helps streamline the implementation process, reducing the time and resources required to achieve certification.
- Documenting Current State: The gap analysis process itself often involves documenting the current state of information security within the organization. This documentation serves as a valuable baseline for future improvements and audits.
Required Documentation for the Audit
Organizations must prepare a comprehensive set of documentation to demonstrate compliance with ISO 27001 during the certification audit. This documentation provides evidence that the ISMS is implemented, maintained, and effective.
- Scope of the ISMS: A formal document clearly defining the scope of the ISMS, including the boundaries, assets, processes, and locations covered.
- Information Security Policy: A high-level policy outlining the organization’s commitment to information security and the overall framework for managing information security risks.
- Risk Assessment and Treatment Plan: Documentation of the risk assessment process, including identified risks, analysis, treatment plans, and implemented controls. This includes the risk assessment methodology used and the results of the risk assessments.
- Statement of Applicability (SoA): A document that lists all the controls from Annex A of ISO 27001 and indicates which controls are applicable to the organization’s ISMS and the justification for any exclusions. This document is a crucial part of the ISMS documentation.
- Security Procedures and Guidelines: Detailed procedures and guidelines for implementing the security controls, including access control, incident management, change management, and data backup.
- Records of Training and Awareness: Documentation of training programs and awareness initiatives to ensure employees understand their information security responsibilities. This includes records of training attendance and assessments.
- Internal Audit Reports: Reports from internal audits, including findings, corrective actions, and follow-up activities. These reports demonstrate the effectiveness of the internal audit process.
- Management Review Minutes: Minutes of management review meetings, including discussions, decisions, and actions taken to improve the ISMS. These minutes demonstrate management’s commitment and oversight of the ISMS.
- Incident Management Procedures and Records: Procedures for handling information security incidents, and records of any incidents that have occurred, including details of the incident, actions taken, and lessons learned.
- Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP): Plans to ensure business continuity in the event of a disruption, including procedures for data recovery and system restoration. These plans demonstrate the organization’s ability to maintain operations during and after a disruptive event.
Steps in the Certification Process
Obtaining ISO 27001 certification is a structured process designed to assess an organization’s Information Security Management System (ISMS) against the standard’s requirements. This process involves several key stages, from initial application to ongoing surveillance. Understanding each step is crucial for organizations aiming to achieve and maintain certification successfully.
Application and Documentation Review
The certification process begins with an application to a certification body (CB) accredited to ISO 27001. The CB will review the organization’s documentation to ensure it aligns with the standard’s requirements. This initial phase sets the foundation for the subsequent audit stages.
- Application Submission: The organization submits a formal application to the chosen CB. This application typically includes information about the organization’s scope of certification, its ISMS, and the number of employees.
- Document Review: The CB reviews the organization’s ISMS documentation, including the Statement of Applicability (SoA), policies, procedures, and records. This review assesses whether the documentation adequately addresses the requirements of ISO 27001.
- Gap Analysis (Optional): Some CBs offer a pre-assessment or gap analysis to identify any potential weaknesses in the ISMS before the formal audit. This can help the organization prepare for the audit.
Stage 1 Audit (Documentation Review)
The Stage 1 audit, also known as the documentation review, focuses on assessing the organization’s ISMS documentation. This stage ensures the ISMS is adequately designed and documented to meet the ISO 27001 standard.
- Purpose: To evaluate the organization’s readiness for the Stage 2 audit.
- Activities: Reviewing ISMS documentation, including policies, procedures, and the SoA. Interviewing key personnel to understand their roles and responsibilities.
- Output: A report identifying any gaps or areas of non-compliance. The CB will determine if the organization is ready for the Stage 2 audit.
- Duration: Typically, this audit takes one to two days, depending on the organization’s size and complexity.
Stage 2 Audit (Implementation Audit)
The Stage 2 audit is a comprehensive on-site assessment of the organization’s ISMS implementation. The CB auditors verify that the ISMS is effectively implemented and meets the requirements of ISO 27001.
- Purpose: To assess the effectiveness of the ISMS and its implementation.
- Activities: Conducting on-site audits, reviewing records, interviewing employees, and observing processes. This includes assessing the implementation of the controls Artikeld in Annex A of ISO 27001.
- Audit Sampling: Auditors use sampling techniques to evaluate the ISMS across different areas of the organization. The sampling approach ensures a representative assessment of the ISMS.
- Non-Conformities: The auditors identify any non-conformities (NCs) with the standard. These are categorized based on severity, ranging from minor to major.
- Output: An audit report detailing the findings, including any non-conformities. The report also includes recommendations for improvement.
- Duration: The duration of the Stage 2 audit depends on the size and complexity of the organization. Typically, it takes several days to a week or more.
Corrective Action and Certification Decision
After the Stage 2 audit, the organization must address any non-conformities identified by the auditors. The CB reviews the corrective actions taken by the organization to ensure they are effective. The certification decision is then made based on the audit findings and the organization’s response.
- Corrective Action Plan: The organization develops a corrective action plan (CAP) to address each non-conformity. The CAP Artikels the actions to be taken, the responsible parties, and the deadlines for completion.
- Implementation of Corrective Actions: The organization implements the corrective actions. This may involve updating policies, procedures, or implementing new controls.
- Verification of Corrective Actions: The CB verifies the effectiveness of the corrective actions. This may involve reviewing documentation, conducting follow-up audits, or requesting evidence of implementation.
- Certification Decision: Based on the audit findings and the effectiveness of the corrective actions, the CB makes a certification decision. If the organization meets the requirements of ISO 27001, the CB issues a certificate.
Surveillance Audits and Recertification
ISO 27001 certification is not a one-time event. The CB conducts regular surveillance audits to ensure the organization maintains its ISMS and continues to comply with the standard. Recertification audits are conducted every three years to renew the certification.
- Surveillance Audits: These are conducted annually to monitor the ongoing effectiveness of the ISMS. The scope of surveillance audits is typically smaller than the Stage 2 audit.
- Recertification Audits: These audits are conducted every three years to reassess the entire ISMS and ensure continued compliance with ISO 27001. The recertification process is similar to the Stage 2 audit.
- Maintaining Certification: The organization must maintain its ISMS and address any non-conformities identified during surveillance audits. Failure to do so can result in the suspension or withdrawal of certification.
What to Expect During the Certification Audit
Organizations undergoing an ISO 27001 certification audit should be prepared for a thorough and professional assessment. Understanding what to expect can help organizations prepare effectively and ensure a smooth audit process.
- Auditor Expertise: The audit will be conducted by qualified auditors with expertise in information security and ISO 27001. The auditors will have a deep understanding of the standard and its requirements.
- Interview Process: Auditors will interview employees at various levels of the organization to assess their understanding of the ISMS and their roles and responsibilities. Interviews are a key component of the audit process.
- Document Review: Auditors will review relevant documentation, including policies, procedures, records, and reports. The document review helps to verify the effectiveness of the ISMS.
- On-Site Observation: Auditors may observe processes and activities to assess how the ISMS is implemented in practice. This can include observing access control procedures or security incident response.
- Non-Conformity Management: Auditors will document any non-conformities identified during the audit. The organization will be required to address these non-conformities through a corrective action plan.
- Audit Report: The auditors will provide a comprehensive audit report summarizing the findings, including any non-conformities and recommendations for improvement.
- Communication: Open and transparent communication between the organization and the auditors is crucial throughout the audit process. The organization should be prepared to answer questions and provide evidence of compliance.
Choosing a Certification Body
Selecting the right certification body is a crucial step in the ISO 27001 certification journey. The choice significantly impacts the efficiency, cost, and ultimately, the credibility of your certification. A well-chosen body will provide a smooth and supportive audit process, while a poor choice can lead to delays, increased costs, and potential dissatisfaction. This section Artikels the key factors to consider when making this important decision.
Factors for Selecting an Accredited Certification Body
Several key considerations should guide your selection process. Careful evaluation of these factors ensures you choose a body that aligns with your organization’s needs and objectives.
- Accreditation: Ensure the certification body is accredited by a recognized accreditation body, such as the ANSI National Accreditation Board (ANAB) in North America or the United Kingdom Accreditation Service (UKAS) in the UK. Accreditation signifies that the certification body meets international standards for competence and impartiality. Verification of accreditation is paramount.
- Experience and Expertise: Look for a certification body with extensive experience in your industry or a similar one. Assess their auditors’ expertise in information security management systems (ISMS) and their understanding of your organization’s specific context. This ensures a more relevant and insightful audit.
- Reputation and Credibility: Research the certification body’s reputation within the industry. Check for client testimonials, case studies, and any reported issues or complaints. A strong reputation indicates a commitment to quality and integrity.
- Cost and Fees: Obtain quotes from multiple certification bodies and compare their fees. Be sure to understand the breakdown of costs, including initial assessment, surveillance audits, and recertification. Consider the overall value offered, not just the lowest price.
- Audit Approach and Methodology: Inquire about the certification body’s audit approach. Does it involve a risk-based approach? Does it provide clear and concise audit reports? A transparent and thorough audit process is essential for identifying areas for improvement.
- Geographic Reach and Availability: Consider the certification body’s geographic reach and the availability of auditors in your region. Local auditors can often provide more personalized service and are familiar with local regulations.
- Language Capabilities: Ensure the certification body can provide audits and documentation in the language your organization uses. This minimizes the risk of miscommunication and ensures a clear understanding of the audit findings.
- Support and Communication: Evaluate the certification body’s level of support and communication. Do they provide clear guidance throughout the certification process? Are they responsive to your inquiries? Effective communication is critical for a smooth and successful certification.
Comparing and Contrasting Certification Bodies
Different certification bodies may exhibit varying strengths and weaknesses. Understanding these differences allows you to select the body that best suits your organization’s specific needs.
For example, some certification bodies might specialize in specific industries, such as finance or healthcare, while others have a broader focus. This specialization can translate to deeper expertise and a more tailored audit process. Some bodies may offer a more streamlined and efficient audit process, while others might prioritize a more in-depth and comprehensive assessment. The choice depends on your organization’s priorities and risk profile.
Example: Let’s compare two hypothetical certification bodies, “CertifySecure” and “GlobalCert.” CertifySecure has a strong reputation in the technology sector, with auditors who possess deep technical knowledge. Their audits are known for being thorough and insightful. However, their fees might be slightly higher. GlobalCert, on the other hand, offers competitive pricing and a global presence. They may have a more standardized audit process, which could be beneficial for organizations with less complex ISMS.
However, their auditors might not have the same level of industry-specific expertise as CertifySecure.
Consider the following table summarizing potential strengths and weaknesses:
| Feature | CertifySecure | GlobalCert |
|---|---|---|
| Strengths | Deep industry expertise in technology, thorough and insightful audits. | Competitive pricing, global presence, standardized audit process. |
| Weaknesses | Higher fees, potentially less experience in other industries. | Less industry-specific expertise, potentially less flexible audit approach. |
Importance of Verifying Accreditation Status
Verifying the accreditation status of a certification body is non-negotiable. Accreditation serves as a critical assurance of the body’s competence, impartiality, and adherence to international standards.
Why is verification so important?
- Ensuring Competence: Accreditation bodies rigorously assess certification bodies to ensure they have the necessary competence to perform audits and issue certifications. This includes assessing their auditors’ qualifications, their audit processes, and their management systems.
- Maintaining Impartiality: Accreditation bodies monitor certification bodies to ensure they maintain impartiality and avoid conflicts of interest. This protects the integrity of the certification process and ensures that certifications are issued fairly.
- Providing International Recognition: Accreditation by a recognized accreditation body, such as those mentioned earlier, provides international recognition of your ISO 27001 certification. This enhances the credibility of your certification and facilitates international trade and collaboration.
- Protecting Against Fraud: Verification helps protect against fraudulent certification bodies that may not meet the required standards.
How to Verify Accreditation:
You can verify the accreditation status of a certification body by visiting the website of the relevant accreditation body (e.g., ANAB, UKAS) and searching for the certification body’s name. The accreditation body’s website will provide information on the certification body’s accredited scope, which specifies the standards and industries for which it is accredited.
Example: If you are based in the United States and considering a certification body, you would go to the ANAB website. You can search for the certification body’s name and verify its accreditation status, including the scope of its accreditation. If the certification body is not accredited, or if its accreditation scope does not include ISO 27001, you should not use that body.
Developing an ISMS: Key Components
An effective Information Security Management System (ISMS) is the cornerstone of ISO 27001 certification. It’s a systematic approach to managing sensitive company information so that it remains secure. This section Artikels the core components necessary for building a robust ISMS.
Core Components of an ISMS
An ISMS comprises several interconnected elements that work together to protect information assets. Implementing these components is critical for achieving and maintaining ISO 27001 compliance.
- Information Security Policy: The cornerstone of the ISMS, this document Artikels the organization’s commitment to information security, defines its objectives, and provides a framework for managing information security risks. It should be approved by top management and communicated to all employees.
- Risk Assessment and Treatment: This involves identifying information security risks, analyzing their likelihood and impact, and selecting appropriate controls to mitigate them. The risk treatment process involves choosing from options such as risk avoidance, risk transfer, risk mitigation, or risk acceptance.
- Statement of Applicability (SoA): The SoA documents the chosen security controls from ISO 27001 Annex A, explaining why each control is relevant or not relevant to the organization. It serves as a roadmap for implementing the chosen controls.
- Security Controls: These are the measures implemented to address identified risks. They can be technical (e.g., firewalls, intrusion detection systems), operational (e.g., access control procedures, incident response plans), or managerial (e.g., security awareness training, policy enforcement).
- Monitoring and Review: The ISMS must be continuously monitored to ensure its effectiveness. This includes regular audits, vulnerability assessments, and reviews of security incidents. The ISMS should be reviewed and updated periodically to adapt to changing threats and business needs.
- Incident Management: A well-defined incident management process is crucial for responding to security breaches and other incidents. This includes procedures for detecting, reporting, responding to, and recovering from security incidents.
- Business Continuity and Disaster Recovery: Planning for business continuity and disaster recovery ensures that critical business processes can continue to operate even in the face of disruptions. This includes developing plans for data backup, system recovery, and business operations.
Steps for Creating and Implementing an ISMS Policy
Developing and implementing an ISMS policy is a structured process that ensures the policy is effective and aligned with the organization’s objectives.
- Obtain Management Support: Secure commitment from top management. Their support is crucial for providing resources and fostering a security-conscious culture.
- Define Scope and Objectives: Determine the scope of the ISMS (e.g., the entire organization, a specific department) and define clear, measurable information security objectives.
- Conduct a Risk Assessment: Identify information assets, threats, vulnerabilities, and the impact of potential security incidents.
- Develop a Statement of Applicability (SoA): Select and document the security controls that will be implemented based on the risk assessment.
- Develop the ISMS Policy: Write a comprehensive policy that Artikels the organization’s approach to information security, including roles, responsibilities, and procedures.
- Implement Security Controls: Implement the selected security controls. This may involve acquiring new technologies, updating existing processes, and training employees.
- Train Employees: Provide security awareness training to all employees to ensure they understand their roles and responsibilities in protecting information assets.
- Monitor and Measure: Establish metrics to monitor the effectiveness of the ISMS. Regularly review the ISMS and make necessary updates.
- Conduct Internal Audits: Perform internal audits to assess the effectiveness of the ISMS and identify areas for improvement.
- Seek Certification: Engage a certification body to conduct an independent audit and grant ISO 27001 certification.
Main Control Objectives and Controls from Annex A of ISO 27001
Annex A of ISO 27001 provides a comprehensive set of security controls that organizations can use to manage their information security risks. The following table Artikels some of the main control objectives and controls, along with examples.
| Control Objective | Control | Description | Example |
|---|---|---|---|
| Information security policies | Information security policy | Define and document an information security policy. | A written document outlining the organization’s approach to information security, approved by senior management and communicated to all employees. |
| Organization of information security | Information security roles and responsibilities | Define and assign information security roles and responsibilities. | Designating a Chief Information Security Officer (CISO) or assigning specific security responsibilities to IT staff and other employees. |
| Asset management | Inventory of assets | Identify and document information assets. | Creating a database or spreadsheet listing all critical information assets, such as servers, databases, and sensitive data. |
| Access control | User access management | Manage user access rights. | Implementing a system for granting, modifying, and revoking user access to systems and data, based on the principle of least privilege. |
| Cryptography | Cryptographic controls | Use cryptography to protect sensitive information. | Encrypting sensitive data at rest and in transit using strong encryption algorithms. |
| Physical and environmental security | Physical security perimeter | Protect physical areas containing information assets. | Implementing access controls to physical locations, such as data centers, and using security cameras and other surveillance systems. |
| Operations security | Malware protection | Protect against malware. | Implementing anti-malware software, regularly scanning systems, and educating users about malware threats. |
| Communications security | Network security | Secure network communications. | Implementing firewalls, intrusion detection systems, and other network security controls. |
| System acquisition, development and maintenance | Secure development | Ensure security is considered throughout the software development lifecycle. | Using secure coding practices, conducting security testing, and reviewing code for vulnerabilities. |
| Supplier relationships | Information security in supplier relationships | Ensure information security is addressed in supplier relationships. | Including information security requirements in contracts with suppliers and conducting security audits of suppliers. |
| Information security incident management | Incident management process | Manage information security incidents. | Establishing a process for reporting, investigating, and resolving security incidents, including data breaches. |
| Business continuity management | Business continuity planning | Plan for business continuity. | Developing and testing a business continuity plan to ensure critical business functions can continue during a disruption. |
| Compliance | Compliance with legal and contractual requirements | Comply with legal and contractual requirements. | Ensuring compliance with data privacy regulations, such as GDPR or CCPA, and contractual obligations related to information security. |
Implementing Security Controls
Implementing security controls is a critical step in achieving ISO 27001 certification. This involves putting in place the specific measures needed to manage and mitigate identified information security risks. The controls, Artikeld in Annex A of ISO 27001, are designed to address various aspects of information security, ensuring the confidentiality, integrity, and availability of information assets. The selection and implementation of these controls must be tailored to the organization’s specific context, risk appetite, and business objectives.
Access Control Best Practices
Access control is fundamental to information security, limiting access to information and resources based on defined roles and responsibilities. Implementing robust access controls minimizes the risk of unauthorized access, data breaches, and other security incidents.
- Principle of Least Privilege: Grant users only the minimum level of access necessary to perform their job functions. This limits the potential damage from compromised accounts. For example, a financial analyst should only have access to the financial reporting system and not to the HR database.
- Role-Based Access Control (RBAC): Assign access rights based on job roles rather than individual users. This simplifies access management and ensures consistency. When an employee changes roles, their access rights can be easily updated.
- Strong Authentication: Implement multi-factor authentication (MFA) for all critical systems and applications. MFA requires users to provide multiple forms of identification, such as a password and a one-time code from a mobile device, making it much harder for attackers to gain access.
- Regular Access Reviews: Conduct periodic reviews of user access rights to ensure they are still appropriate and aligned with current job roles. This helps identify and remove unnecessary access permissions. The review should be performed at least annually.
- Password Management: Enforce strong password policies, including minimum length, complexity requirements, and regular password changes. Educate users on password security best practices, such as avoiding common words and phrases.
Incident Management Best Practices
An effective incident management process is crucial for responding to and mitigating security incidents promptly and effectively. This process includes preparation, detection, analysis, containment, eradication, recovery, and post-incident activity.
- Incident Response Plan: Develop a comprehensive incident response plan that Artikels the steps to be taken in the event of a security incident. This plan should include roles and responsibilities, communication protocols, and escalation procedures.
- Incident Detection and Reporting: Implement tools and procedures to detect and report security incidents. This includes monitoring network traffic, security logs, and user activity for suspicious behavior. Employees should be trained to report any suspected security incidents promptly.
- Incident Analysis and Containment: Analyze security incidents to determine their scope, impact, and root cause. Contain the incident to prevent further damage, such as isolating affected systems or changing passwords.
- Eradication and Recovery: Eradicate the root cause of the incident and recover affected systems and data. This may involve patching vulnerabilities, removing malware, or restoring data from backups.
- Post-Incident Activity: Conduct a post-incident review to identify lessons learned and improve the incident response process. This includes analyzing the incident, documenting the findings, and implementing corrective actions.
Data Protection Best Practices
Data protection is a critical aspect of information security, ensuring the confidentiality, integrity, and availability of sensitive information. Implementing robust data protection measures minimizes the risk of data breaches, unauthorized access, and data loss.
- Data Classification: Classify data based on its sensitivity and criticality. This helps determine the appropriate security controls needed to protect the data. Common classifications include public, internal, confidential, and highly confidential.
- Data Encryption: Encrypt sensitive data both in transit and at rest. This protects the data from unauthorized access, even if the storage medium is compromised.
- Data Loss Prevention (DLP): Implement DLP tools to monitor and prevent sensitive data from leaving the organization. This includes monitoring email, network traffic, and removable media.
- Data Backup and Recovery: Implement a robust data backup and recovery strategy to ensure data can be restored in the event of a disaster or data loss incident. This includes regular backups, offsite storage, and testing of the recovery process.
- Data Retention and Disposal: Establish policies and procedures for the retention and disposal of data. This includes defining how long data should be retained, how it should be securely disposed of, and who is responsible for these tasks.
Risk Assessment and Risk Treatment Plan Development
A risk assessment is a systematic process of identifying, analyzing, and evaluating information security risks. The risk treatment plan Artikels the actions to be taken to manage those risks.
- Identify Assets: Identify all information assets, including hardware, software, data, and personnel. Determine the value and criticality of each asset.
- Identify Threats: Identify potential threats that could exploit vulnerabilities in the organization’s assets. Threats can be internal or external, intentional or unintentional. Examples include malware, phishing attacks, and natural disasters.
- Identify Vulnerabilities: Identify vulnerabilities in the organization’s systems, processes, and controls. Vulnerabilities are weaknesses that could be exploited by a threat. Examples include unpatched software, weak passwords, and inadequate physical security.
- Analyze Risks: Analyze the likelihood and impact of each risk. Determine the level of risk based on the probability of the threat exploiting the vulnerability and the potential damage that could result. A risk matrix can be used to visualize the risk levels.
- Evaluate Risks: Evaluate the risks based on the organization’s risk appetite. Determine which risks require treatment and the priority for addressing them.
- Develop a Risk Treatment Plan: Develop a risk treatment plan that Artikels the actions to be taken to manage identified risks. The plan should include the following options:
Risk Level = Likelihood x Impact
- Risk Avoidance: Eliminate the risk by not undertaking the activity that creates the risk.
- Risk Transfer: Transfer the risk to another party, such as through insurance or outsourcing.
- Risk Mitigation: Reduce the likelihood or impact of the risk through the implementation of security controls.
- Risk Acceptance: Accept the risk if the cost of treatment is greater than the potential impact.
Documentation and Records
Documentation and meticulous record-keeping are cornerstones of a successful ISO 27001 certification journey. A well-documented Information Security Management System (ISMS) not only demonstrates compliance with the standard but also provides a framework for consistent security practices, efficient incident response, and continuous improvement. It acts as a living, breathing guide for your organization’s security posture.
Significance of Documentation in ISO 27001 Certification
Documentation is crucial because it provides evidence of your ISMS’s effectiveness and conformity with ISO 27001 requirements. It demonstrates how your organization plans, implements, operates, monitors, reviews, maintains, and improves its information security. A comprehensive documentation set allows auditors to assess your organization’s adherence to the standard, ensuring that security controls are in place and functioning as intended.
Essential Documents Required for Certification
A robust set of documents is essential for demonstrating compliance with ISO 27001. These documents provide the necessary evidence to auditors.
- Scope of the ISMS: Defines the boundaries of your ISMS, specifying which areas of your organization are covered by the ISMS.
- Information Security Policy: A high-level document that Artikels your organization’s commitment to information security, including its objectives and principles.
- Risk Assessment and Treatment Plan: Details the process for identifying, analyzing, evaluating, and treating information security risks. This includes the risk assessment methodology, the identified risks, the likelihood and impact assessments, and the chosen risk treatment options (e.g., avoidance, transfer, mitigation, or acceptance).
- Statement of Applicability (SoA): Lists the security controls selected from Annex A of ISO 27001 that are applicable to your ISMS, along with the justification for their selection or exclusion.
- Security Controls Implementation Documentation: Detailed descriptions of how the selected security controls are implemented, including procedures, guidelines, and technical specifications.
- Procedures: Step-by-step instructions for performing various security-related tasks, such as incident response, access control, and data backup.
- Records: Evidence that the ISMS is being operated effectively. This includes logs, reports, and other documents that demonstrate compliance with the established procedures and controls. Examples include:
- Audit trails of system access.
- Results of vulnerability scans and penetration tests.
- Records of security awareness training.
- Incident reports and resolution details.
- Internal Audit Reports: Document the results of internal audits, including findings, nonconformities, and corrective actions.
- Management Review Records: Minutes and reports from management reviews of the ISMS, including decisions and actions taken.
Maintaining and Updating ISMS Documentation
Maintaining and updating your ISMS documentation is an ongoing process that ensures its relevance and effectiveness. It should be a continuous cycle of review, revision, and improvement.
- Establish a Document Control System: Implement a system to manage your documentation, including version control, access control, and document approval processes. This system ensures that only the current, approved versions of documents are used.
- Regular Reviews: Schedule regular reviews of all documentation, typically at least annually, or more frequently if there are significant changes to your organization, its IT infrastructure, or the threat landscape. The reviews should be conducted by the relevant stakeholders, such as the information security manager, IT staff, and process owners.
- Document Updates: Update documents as needed to reflect changes in the organization, its environment, or the requirements of ISO 27001. This includes updates to policies, procedures, and risk assessments.
- Training and Awareness: Ensure that all relevant personnel are aware of the documentation and its importance. Provide training on how to access and use the documentation, as well as any changes that have been made.
- Version Control: Maintain version control of all documents to track changes and ensure that the most up-to-date versions are always available. This includes using unique identifiers (e.g., document numbers and version numbers) and dates of revision.
- Record Keeping: Keep records of all document reviews, updates, and approvals. This provides an audit trail of the changes made to the documentation and demonstrates your commitment to maintaining a current and effective ISMS.
Effective documentation is not merely a compliance requirement; it is a strategic asset that enables organizations to protect their information assets, mitigate risks, and achieve their business objectives.
Internal Audits and Management Review
Internal audits and management reviews are critical components of an ISO 27001-compliant Information Security Management System (ISMS). They provide a mechanism for continuous improvement, ensuring the ISMS remains effective and aligned with the organization’s security objectives and the requirements of the standard. These processes help identify weaknesses, evaluate the effectiveness of implemented controls, and drive necessary changes to maintain and enhance information security posture.
Importance of Internal Audits and Management Reviews
Regular internal audits and management reviews are essential for several reasons. They help organizations maintain compliance, identify areas for improvement, and ensure the ISMS remains relevant and effective.
- Ensuring Compliance: Internal audits verify that the ISMS adheres to the requirements of ISO 27001 and relevant legal and regulatory requirements. This includes assessing the implementation and effectiveness of security controls.
- Identifying Improvement Opportunities: Audits and reviews highlight areas where the ISMS can be improved. This includes identifying control weaknesses, gaps in documentation, and opportunities to enhance security practices.
- Monitoring Effectiveness: They provide a means to monitor the effectiveness of implemented security controls and measure progress towards achieving information security objectives. This helps to ensure that the organization’s security efforts are yielding the desired results.
- Driving Continuous Improvement: The findings from audits and reviews are used to drive continuous improvement of the ISMS. This iterative process ensures that the ISMS evolves to meet changing threats and business needs.
- Demonstrating Commitment: Conducting regular audits and reviews demonstrates the organization’s commitment to information security and provides evidence to stakeholders, including customers, partners, and regulators.
Performing an Internal Audit
The internal audit process is a systematic examination of the ISMS to determine its conformity with ISO 27001 and the organization’s established information security policies and procedures. This involves planning, conducting, reporting, and following up on audit findings.
- Audit Planning: The audit process begins with planning. This involves defining the audit scope, objectives, criteria, and schedule. The audit scope should clearly define the areas and processes to be audited.
- Audit Scope: The audit scope should cover all relevant aspects of the ISMS, including policies, procedures, controls, and records. It should be aligned with the organization’s information security objectives and the requirements of ISO 27001. The scope is often determined by the organization’s risk assessment and the criticality of the information assets.
- Audit Methodology: Auditors typically employ various methodologies, including document review, interviews, observation, and testing. The methodology should be appropriate for the audit scope and objectives.
- Audit Execution: The audit team gathers evidence by examining documents, interviewing personnel, observing processes, and testing controls. Auditors compare the ISMS against the audit criteria and document any findings.
- Audit Reporting: The audit team prepares a report summarizing the audit findings, including any nonconformities, observations, and recommendations for improvement. The report is typically presented to management.
- Follow-up: The organization takes corrective actions to address any nonconformities identified during the audit. The audit team verifies the effectiveness of the corrective actions through follow-up audits.
Management Review Report Template
The management review is a formal process where top management assesses the ISMS’s performance and effectiveness. A well-structured report documenting the management review is crucial for demonstrating compliance and driving improvement.
| Section | Description | Example Content |
|---|---|---|
| Introduction | Provides an overview of the management review, including the date, participants, and objectives. | “This report summarizes the findings of the management review of the ISMS, conducted on [Date]. The review was attended by [List of participants] and aimed to assess the ISMS’s performance and identify opportunities for improvement.” |
| Review of Previous Management Review Actions | Assesses the status of actions from the previous management review. | “All actions from the previous management review held on [Date] have been completed, with the exception of [List any outstanding actions].” |
| Performance of the ISMS | Evaluates the performance of the ISMS, including the results of internal audits, monitoring activities, and security incidents. | “The internal audit conducted on [Date] identified [Number] nonconformities, which have been addressed through corrective actions. [Summarize key findings from monitoring activities, such as vulnerability scans and penetration tests.] There were [Number] security incidents reported during the review period, and all were resolved according to established procedures.” |
| Feedback from Interested Parties | Summarizes feedback from internal and external stakeholders, such as customers, partners, and employees. | “Feedback from customers has been generally positive, with [Number] positive comments regarding our information security practices. Employee surveys indicated [Summarize employee feedback]. No significant concerns were raised by our partners.” |
| Status of Corrective and Preventive Actions | Reviews the status of corrective and preventive actions taken to address nonconformities and security incidents. | “Corrective actions have been implemented to address the nonconformities identified during the internal audit. The effectiveness of these actions will be verified during the next internal audit. Preventive actions are in place to mitigate the risk of future incidents.” |
| Changes That Could Affect the ISMS | Identifies any changes in the internal or external context that could affect the ISMS, such as changes in regulations, business objectives, or technology. | “The organization is planning to implement a new cloud-based service, which will require adjustments to our ISMS. The new GDPR requirements have been fully incorporated into our ISMS.” |
| Recommendations for Improvement | Provides recommendations for improving the ISMS, based on the findings of the review. | “It is recommended that the organization enhance its incident response plan to include [Specific recommendations]. The organization should consider investing in [Specific security technologies or training].” |
| Action Items | Defines specific action items, including the responsible parties and deadlines. |
|
| Conclusion | Summarizes the key findings and conclusions of the management review. | “The management review concluded that the ISMS is effectively implemented and maintained. The recommendations and action items Artikeld in this report will be implemented to further enhance the ISMS.” |
Maintaining Certification and Continuous Improvement
Maintaining ISO 27001 certification is not a one-time event but an ongoing process. It requires a commitment to continuous improvement and adaptation to evolving threats and business needs. This section Artikels the steps involved in maintaining certification, provides examples of how to continually improve your Information Security Management System (ISMS), and shares strategies for responding to audit findings.
Steps for Maintaining ISO 27001 Certification
To maintain your ISO 27001 certification, a series of ongoing activities are required. These activities ensure that your ISMS remains effective and aligned with the standard’s requirements.
- Surveillance Audits: These audits are conducted periodically (typically annually) by your certification body. Their primary purpose is to verify that your ISMS continues to meet the requirements of ISO 27001 and that you are effectively implementing your security controls. The scope of the surveillance audit can vary but generally covers a selection of controls, processes, and documentation. The frequency and duration of these audits are determined by the certification body and the initial certification audit findings.
- Recertification Audits: A recertification audit is a comprehensive audit that occurs every three years. It’s essentially a full reassessment of your ISMS, similar to the initial certification audit. The recertification audit ensures that your ISMS remains robust, effective, and up-to-date with the latest version of the standard. The recertification process typically follows a similar structure to the initial certification process, involving document review, interviews, and on-site observations.
- Internal Audits: Conducting regular internal audits is a crucial element of maintaining certification. These audits are performed by your organization’s internal auditors (or external auditors) to assess the effectiveness of your ISMS and identify areas for improvement. The frequency of internal audits is determined by your organization’s risk assessment and the complexity of your ISMS. Internal audits should cover all aspects of your ISMS, including security controls, policies, procedures, and documentation.
- Management Review: Management review is a periodic assessment of your ISMS by top management. This review evaluates the ISMS’s performance, effectiveness, and suitability, considering changes in the internal and external context, security threats, and business objectives. The management review should result in documented decisions and actions to address any identified issues or opportunities for improvement. The frequency of management reviews is typically annual, but can be more frequent based on the organization’s needs.
- Continuous Improvement: This is the ongoing process of identifying and implementing improvements to your ISMS. It involves analyzing audit findings, monitoring security incidents, reviewing performance metrics, and adapting to changes in the threat landscape and business environment. Continuous improvement is essential for maintaining the effectiveness of your ISMS and ensuring that it remains relevant and aligned with your organization’s goals.
Examples of Continually Improving an ISMS
Continuous improvement is a core principle of ISO 27001. It involves a proactive approach to identifying and implementing enhancements to your ISMS. Several areas can be targeted for improvement.
- Risk Assessment and Treatment: Regularly review and update your risk assessment process. This includes identifying new threats and vulnerabilities, reassessing the likelihood and impact of risks, and updating your risk treatment plan accordingly. For instance, if a new vulnerability is discovered in a widely used software, you should update your risk assessment to reflect the potential impact and implement appropriate mitigation measures, such as patching or implementing compensating controls.
- Security Controls: Periodically review and update your security controls. This includes evaluating the effectiveness of existing controls, identifying new controls that may be needed, and implementing improvements to existing controls. For example, if your organization experiences a phishing attack, you might enhance your employee training program, implement stricter email filtering rules, or introduce multi-factor authentication.
- Documentation: Maintain and update your ISMS documentation, including policies, procedures, and records. This ensures that your documentation accurately reflects your ISMS and that it is readily available to all relevant personnel. Consider updating your incident response plan regularly based on lessons learned from security incidents or changes in the threat landscape.
- Employee Training and Awareness: Continuously improve your employee training and awareness programs. This includes providing regular training on security awareness, specific security controls, and the latest threats. Consider implementing phishing simulations to test employee awareness and identify areas for improvement.
- Incident Management: Review and improve your incident management process. This includes regularly testing your incident response plan, analyzing security incidents to identify root causes, and implementing corrective actions to prevent future incidents. For instance, if a data breach occurs, analyze the incident to determine the cause and implement measures to prevent future occurrences, such as strengthening access controls or improving data encryption.
Strategies for Responding to Audit Findings and Implementing Corrective Actions
Audit findings, whether from internal or external audits, are valuable opportunities for improvement. Effective responses to audit findings are crucial for maintaining certification and improving your ISMS.
- Understand the Finding: Thoroughly understand the audit finding. Review the evidence cited by the auditor and clarify any ambiguities. Ensure that you fully grasp the nature of the nonconformity and its potential impact on your ISMS.
- Root Cause Analysis: Conduct a root cause analysis to determine the underlying cause of the nonconformity. This will help you identify the specific actions that led to the finding and prevent similar issues in the future. Techniques such as the “5 Whys” or a fishbone diagram can be useful in this analysis.
- Develop a Corrective Action Plan: Develop a detailed corrective action plan that addresses the root cause of the nonconformity. The plan should include specific actions to be taken, the responsible person(s), and a target completion date.
- Implement Corrective Actions: Implement the corrective actions Artikeld in your plan. This may involve updating policies and procedures, implementing new security controls, or providing additional training.
- Verify Effectiveness: After implementing the corrective actions, verify their effectiveness. This can be done through internal audits, testing, or monitoring. Ensure that the corrective actions have resolved the nonconformity and prevented similar issues from recurring.
- Document Everything: Maintain thorough documentation of all audit findings, root cause analyses, corrective action plans, and verification activities. This documentation is essential for demonstrating your commitment to continuous improvement and for maintaining your certification.
Final Wrap-Up
In conclusion, achieving ISO 27001 certification is a testament to your organization’s commitment to information security. By following the Artikeld steps, embracing best practices, and prioritizing continuous improvement, you can not only secure your valuable data but also gain a competitive advantage. This guide serves as your compass, leading you towards a robust and resilient ISMS, ensuring long-term success in the ever-evolving landscape of information security.
FAQ Summary
What is the typical timeframe for ISO 27001 certification?
The certification process can take anywhere from 6 to 18 months, depending on the size and complexity of your organization, the maturity of your existing security controls, and the efficiency of your implementation and audit process.
How much does ISO 27001 certification cost?
The cost varies widely based on several factors, including the size of your organization, the scope of the ISMS, and the fees charged by the certification body. Costs typically include consulting fees, internal resources, and the certification body’s audit fees. Expect a comprehensive budget plan to accommodate this process.
Is ISO 27001 certification mandatory?
While ISO 27001 certification is not legally mandated, it is often a requirement for doing business with certain clients or in specific industries. It demonstrates a commitment to information security and can significantly enhance your organization’s reputation and competitiveness.
What happens if we fail the certification audit?
If your organization fails the initial certification audit, you’ll receive a non-conformity report outlining the areas needing improvement. You’ll then have a period to address these issues and undergo a follow-up audit to demonstrate compliance. Addressing these issues promptly is key to successfully achieving certification.
How often is ISO 27001 certification renewed?
ISO 27001 certification is typically valid for three years. During this period, you’ll undergo annual surveillance audits to ensure continued compliance with the standard. After three years, a recertification audit is required to renew your certification.