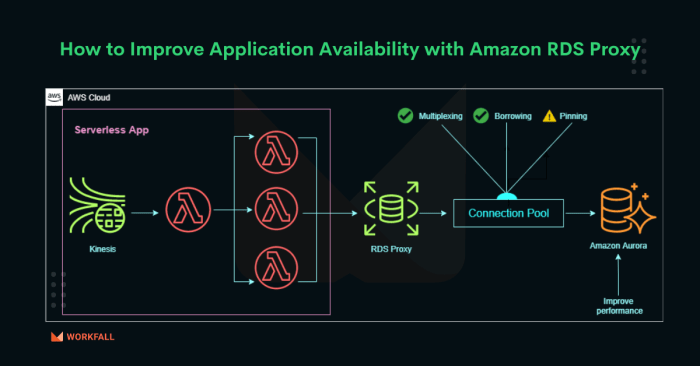
Managing database connections efficiently is crucial for application performance and scalability, particularly in dynamic environments. Amazon RDS Proxy offers a robust solution, acting as a middleman between your applications and your databases, optimizing connection management, and enhancing security. This approach minimizes the direct exposure of your database credentials while providing connection pooling and failover capabilities, ultimately leading to a more resilient and performant system.
This guide delves into the intricacies of RDS Proxy, exploring its core functionalities, setup procedures, and benefits. We will dissect the advantages of utilizing RDS Proxy over direct database connections, examine its configuration within the AWS environment, and illustrate its impact on database performance and security. From understanding connection pooling to implementing security best practices, this document provides a comprehensive overview of RDS Proxy and its practical applications.
Introduction to RDS Proxy
Amazon RDS Proxy is a fully managed, highly available database proxy that makes applications more scalable, more resilient to database failures, and more secure. It acts as an intermediary between your application and your database, managing connections efficiently and improving overall database performance. This allows applications to handle database connections more effectively, reducing the load on the database and improving the user experience.RDS Proxy enhances application performance and reliability by pooling database connections.
It also provides improved security through features like IAM authentication and connection encryption.
RDS Proxy Versus Direct Database Connections
Direct database connections require applications to manage connections directly to the database. This can lead to inefficiencies, especially under heavy load. RDS Proxy provides a layer of abstraction that simplifies connection management and offers several advantages over direct connections.
- Connection Pooling: RDS Proxy maintains a pool of database connections, reusing them to serve new requests. This reduces the overhead of establishing new connections for each request, improving application responsiveness and reducing database load. Direct connections require the application to handle connection pooling, which can be complex and resource-intensive to manage.
- Failover Support: RDS Proxy automatically handles database failover. If the primary database instance becomes unavailable, RDS Proxy transparently redirects connections to a standby instance, minimizing downtime. With direct connections, the application must be designed to detect and handle failovers, which can be a complex and error-prone process.
- Security: RDS Proxy supports IAM authentication, allowing applications to authenticate to the database using IAM credentials. This simplifies security management and provides fine-grained access control. Direct connections may require the application to manage database credentials directly, increasing the risk of security breaches.
- Improved Scalability: RDS Proxy allows applications to scale more easily. By pooling connections and reducing database load, RDS Proxy enables applications to handle a higher volume of requests without requiring changes to the application code. Direct connections can limit the scalability of applications, as each connection consumes database resources.
Advantages of Using RDS Proxy for Connection Pooling
Connection pooling is a critical aspect of database performance and scalability, especially in applications with a high volume of concurrent requests. RDS Proxy excels in connection pooling, offering several advantages over other connection pooling mechanisms.
- Reduced Database Load: RDS Proxy maintains a pool of persistent database connections. When a new request arrives, RDS Proxy retrieves a connection from the pool instead of establishing a new connection. This significantly reduces the number of new connections established to the database, lowering the database’s CPU and memory consumption.
- Faster Response Times: Reusing existing connections from the pool is much faster than establishing new connections. This results in quicker response times for application requests, improving the user experience. The time saved in connection establishment can be substantial, particularly in applications with frequent database interactions.
- Improved Scalability: Connection pooling allows the database to handle a higher volume of concurrent requests. RDS Proxy’s connection pooling capabilities enable applications to scale more effectively, as they can serve more users and handle increased traffic without significant performance degradation.
- Connection Management: RDS Proxy handles the complexities of connection management, such as connection timeouts and idle connection cleanup. This simplifies application development and reduces the risk of connection-related errors.
- Efficient Resource Utilization: By reusing existing connections, RDS Proxy optimizes database resource utilization. This can lead to cost savings and improved database performance. The reduction in connection establishment overhead also frees up database resources for other tasks.
Setting Up an RDS Proxy
RDS Proxy setup involves a structured process within the AWS Management Console. This process requires careful configuration to ensure optimal performance, security, and availability of database connections. The following sections detail the steps and configurations necessary to establish an effective RDS Proxy.
Designing the Steps to Create an RDS Proxy in the AWS Management Console
The creation of an RDS Proxy within the AWS Management Console involves a sequence of actions, each with specific parameters. Understanding these steps is crucial for a successful deployment.
- Access the RDS Console: Navigate to the Amazon RDS service within the AWS Management Console.
- Select RDS Proxy: In the left-hand navigation pane, choose “Proxies”.
- Initiate Proxy Creation: Click the “Create proxy” button. This starts the proxy creation wizard.
- Configure Proxy Details:
- Proxy name: Provide a unique name for the proxy.
- Target database: Select the target database cluster or instance. This includes specifying the engine type (e.g., MySQL, PostgreSQL, MariaDB, SQL Server).
- Proxy engine: Select the RDS Proxy engine version. Choose the engine version that is compatible with the database instance.
- Authentication: Configure the authentication method (e.g., IAM authentication, database authentication).
- Configure Connection Pooling: Set the connection pool configuration. Connection pooling parameters, such as connection idle timeout and maximum connections, must be carefully configured to avoid performance bottlenecks.
- Configure Network Settings: Specify the VPC, subnets, and security groups. The security groups must allow inbound traffic to the proxy and outbound traffic to the database instance.
- Review and Create: Review all configurations and click “Create proxy”. The creation process will start, which may take a few minutes.
- Verification: After the proxy is created, verify the status and connection details. Ensure the proxy is running and accessible from your application.
Organizing the Configuration Settings Required for an RDS Proxy
The configuration settings for an RDS Proxy are critical for defining its behavior and ensuring proper connectivity. These settings govern the proxy’s interaction with the database and client applications.
- Target Database Selection: This involves specifying the database engine, database instance, and associated credentials. The RDS Proxy needs to know which database it is fronting.
- Engine Type: The engine type must match the database instance’s engine (e.g., MySQL, PostgreSQL, MariaDB, SQL Server).
- Database Instance: The database instance is the specific RDS instance or cluster that the proxy will connect to.
- Credentials: Credentials are required to authenticate the proxy with the target database. This can be a username and password or IAM role-based authentication.
- Security Group Configuration: Security groups control the inbound and outbound traffic to the RDS Proxy. They are crucial for network security.
- Inbound Rules: These rules specify which traffic is allowed to access the proxy. Typically, you would allow traffic from the application servers.
- Outbound Rules: These rules specify which traffic the proxy can send. The proxy needs to be able to connect to the target database instance.
- VPC and Subnets: The proxy must be deployed within a VPC and subnets. These define the network environment in which the proxy operates.
- Connection Pooling: Connection pooling manages database connections efficiently, reducing latency and improving scalability.
- Connection Idle Timeout: This setting specifies the amount of time a connection can remain idle before being closed.
- Maximum Connections: This setting defines the maximum number of connections the proxy can maintain.
- Connection Borrowing: Allows the proxy to reuse existing connections to the database, which is a key performance optimization.
- Authentication: Authentication mechanisms secure access to the database.
- IAM Authentication: Integrates with AWS IAM for authentication, providing enhanced security and access control.
- Database Authentication: Uses database-specific authentication methods (e.g., username and password).
Creating a Step-by-Step Guide to Configuring Network Settings for RDS Proxy
Network settings are fundamental to establishing connectivity between client applications, the RDS Proxy, and the target database. Incorrect configuration can lead to connection failures and performance issues.
- VPC Selection: Select the Virtual Private Cloud (VPC) where the RDS Proxy will reside. The VPC should be the same one as the target database instance or a VPC peered with it.
- Subnet Selection: Choose the subnets within the VPC where the RDS Proxy will be deployed. It is recommended to select multiple subnets in different Availability Zones for high availability.
- Security Group Configuration:
- Create or Select a Security Group: Create a new security group specifically for the RDS Proxy or select an existing one.
- Inbound Rules Configuration: Add inbound rules to allow traffic from the application servers. Specify the source IP addresses or security groups of the application servers and the port used by the database (e.g., 3306 for MySQL, 5432 for PostgreSQL).
- Outbound Rules Configuration: Add outbound rules to allow the RDS Proxy to connect to the target database instance. Specify the security group or IP address range of the database instance and the port used by the database.
- Network ACLs (Optional): Configure Network Access Control Lists (ACLs) if needed. Network ACLs provide an additional layer of security by controlling traffic at the subnet level.
- Testing Network Connectivity: After configuring the network settings, test the connectivity to ensure the application servers can connect to the RDS Proxy, and the proxy can connect to the database instance. This can be done by using the database client to connect to the proxy endpoint.
Database Compatibility and Support
RDS Proxy’s functionality is intrinsically linked to the supported database engines and their respective versions. Understanding this compatibility is crucial for determining the suitability of RDS Proxy within a given database environment. The following sections detail the supported database engines, their compatible versions, and illustrative scenarios for their effective deployment.
Supported Database Engines
RDS Proxy offers compatibility with a selection of popular database engines, enhancing its utility across diverse application landscapes. This support extends to both relational and, indirectly, to NoSQL databases through compatible connectors or intermediary services.
- MySQL: RDS Proxy provides robust support for MySQL databases, allowing for efficient connection management and improved application performance. This includes compatibility with various MySQL versions, enabling its use across diverse deployments.
- PostgreSQL: PostgreSQL, known for its advanced features and extensibility, is also supported. This allows users to leverage RDS Proxy for connection pooling and failover capabilities within their PostgreSQL environments.
- MariaDB: RDS Proxy extends its support to MariaDB, a popular open-source database, offering similar benefits as with MySQL and PostgreSQL. This support facilitates connection optimization and resilience for MariaDB deployments.
- SQL Server: For environments utilizing Microsoft SQL Server, RDS Proxy offers compatibility. This enables users to benefit from connection pooling and improved performance in their SQL Server deployments.
Compatible Database Engine Versions
The compatibility of RDS Proxy with specific database engine versions is a critical aspect to consider. Staying up-to-date on supported versions ensures optimal performance, security, and access to the latest features. The following provides details on the versions supported at the time of this writing; however, it is crucial to refer to the official AWS documentation for the most current and accurate information.
- MySQL: RDS Proxy generally supports a range of MySQL versions, often including the latest stable releases. Specific version support is continuously updated, and it’s essential to consult the AWS documentation for the most up-to-date list. For instance, versions like 8.0.x and 5.7.x are commonly supported, offering a wide selection for various application needs.
- PostgreSQL: Similarly, PostgreSQL support spans several major versions. This often includes the most recent stable releases and several previous versions to accommodate diverse operational requirements. AWS documentation provides specific version details. For example, versions such as 15.x, 14.x, and 13.x are typically supported, reflecting a commitment to provide a variety of options for database environments.
- MariaDB: MariaDB support mirrors the commitment to the latest stable releases, ensuring that users can integrate RDS Proxy with current versions of MariaDB. The supported versions typically include the latest stable releases, such as 10.x. Consult the official documentation for the most up-to-date compatibility matrix.
- SQL Server: SQL Server support is maintained to cover recent and frequently used versions. This ensures that RDS Proxy users can take advantage of the latest security patches and feature enhancements. For example, versions like SQL Server 2019 and SQL Server 2022 are commonly supported. The official documentation will provide specific details on supported editions and versions.
Suitable Scenarios for Different Database Types
The utility of RDS Proxy varies based on the database type and the specific application requirements. Several scenarios highlight the applicability of RDS Proxy for each supported database engine.
- MySQL: In high-traffic web applications built on MySQL, RDS Proxy can be invaluable. Consider an e-commerce platform that experiences significant traffic spikes during sales events. RDS Proxy can efficiently manage a large number of concurrent connections, prevent connection exhaustion, and improve overall response times. For example, a platform using a connection pool size of 500 connections can, during peak loads, efficiently handle a sudden surge in user activity without performance degradation.
- PostgreSQL: For applications requiring robust data integrity and complex queries, PostgreSQL combined with RDS Proxy offers significant advantages. Imagine a financial services application processing numerous transactions. RDS Proxy can ensure efficient connection management, minimizing latency and maximizing the availability of database resources. A practical example is a trading platform using PostgreSQL; RDS Proxy can maintain consistent performance even during volatile market conditions, where rapid data updates are critical.
- MariaDB: MariaDB, known for its open-source flexibility, benefits from RDS Proxy in environments requiring high availability and scalability. Consider a content management system (CMS) built on MariaDB. RDS Proxy facilitates seamless failover and connection pooling, ensuring continuous content delivery. A CMS serving millions of pages, for instance, can use RDS Proxy to handle surges in user requests without compromising performance.
- SQL Server: Applications relying on Microsoft SQL Server can significantly improve performance and resilience by leveraging RDS Proxy. Consider a business intelligence (BI) platform that processes large datasets and complex queries. RDS Proxy can efficiently manage connections, optimizing query performance, and improving the platform’s responsiveness. For instance, a BI platform with a user base that performs complex data analysis can use RDS Proxy to ensure that data analysis operations remain efficient and reliable.
Connection Management and Pooling
RDS Proxy’s architecture is designed to optimize database interactions, and a key component of this optimization is its sophisticated approach to connection management and pooling. This feature significantly enhances database performance and scalability, especially in environments with a high volume of client connections.
Connection Pooling in RDS Proxy
RDS Proxy employs connection pooling, a crucial technique for managing database connections efficiently. This mechanism involves maintaining a pool of pre-established database connections. When a client application requests a connection, RDS Proxy retrieves an existing connection from the pool instead of establishing a new one. After the client is finished with the connection, it’s returned to the pool for reuse by other clients.
This drastically reduces the overhead associated with repeatedly establishing and tearing down database connections.The benefits of connection pooling are substantial.
- Reduced Connection Latency: Establishing a new database connection involves several steps, including network communication, authentication, and resource allocation. By reusing existing connections, RDS Proxy eliminates these delays, resulting in faster response times for client applications.
- Improved Database Resource Utilization: Establishing a high number of concurrent connections can strain database resources, such as memory and CPU. Connection pooling limits the number of active connections to the database, preventing resource exhaustion and improving overall database performance.
- Enhanced Scalability: Connection pooling allows RDS Proxy to handle a significantly larger number of client connections than would be possible without it. This is because the proxy efficiently manages the connections, allowing the database to focus on processing queries.
RDS Proxy’s connection pooling mechanism provides several advantages:
- Connection Reuse: RDS Proxy reuses existing database connections to serve new client requests. This avoids the overhead of establishing new connections, reducing latency.
- Connection Limits: RDS Proxy can limit the number of concurrent connections to the database. This protects the database from being overwhelmed by excessive connection requests.
- Connection Lifecycle Management: RDS Proxy manages the lifecycle of database connections, including creation, maintenance, and closure. This simplifies connection management for client applications.
RDS Proxy Connection Management Efficiency
RDS Proxy’s efficiency in connection management stems from its ability to multiplex connections and its intelligent connection handling strategies. It intelligently manages connections based on client request patterns and database resource availability.RDS Proxy multiplexes client connections onto a smaller number of database connections. This means that multiple client requests can be served using the same database connection. This further reduces the load on the database and improves overall efficiency.The proxy also employs a “least recently used” (LRU) strategy for connection management.
When the connection pool is full and a new connection is needed, the least recently used connection is closed and replaced with the new one. This ensures that frequently used connections are kept active, minimizing connection establishment overhead.RDS Proxy also monitors connection health and proactively closes connections that are idle or experiencing errors. This helps maintain the stability and reliability of the connection pool.
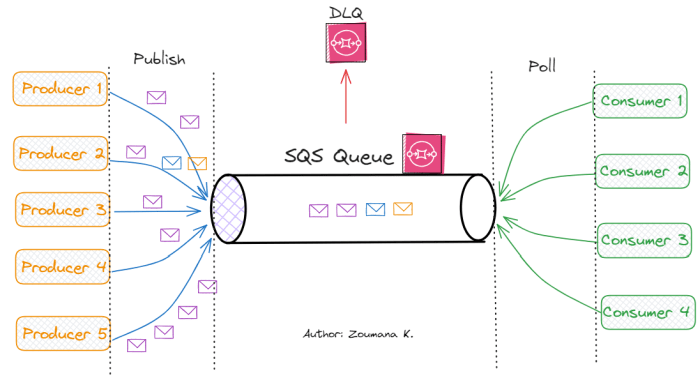
Diagram of Connection Pooling Mechanism
The following illustrates the connection pooling mechanism within RDS Proxy.
The diagram depicts a simplified representation of the connection pooling process.
* Client Applications: Multiple client applications, represented by individual boxes, each initiating database connection requests. These clients send requests to RDS Proxy.
RDS Proxy
The central component, represented by a box labeled “RDS Proxy,” receives client requests and manages the connection pool.
Connection Pool
Within the RDS Proxy, a pool of pre-established database connections is maintained. This is visualized as a collection of connection objects. Each object represents an established connection to the database.
Database
The database server, represented by a box labeled “Database,” receives the actual database queries from RDS Proxy.
The process flows as follows:
- A client application sends a database connection request to RDS Proxy.
- RDS Proxy checks the connection pool for an available connection.
- If a connection is available, RDS Proxy assigns the connection to the client application.
- The client application uses the connection to execute database queries.
- Once the client application is finished with the connection, it releases the connection back to the pool.
- If no connection is available, RDS Proxy either creates a new connection (if the pool isn’t at its maximum size) or queues the request (if the pool is full).
- The database processes queries received through the connections managed by RDS Proxy.
This diagram illustrates the key components and interactions involved in RDS Proxy’s connection pooling mechanism, showcasing how client requests are efficiently routed through the proxy to the database, minimizing connection overhead and maximizing resource utilization.
Security Considerations
Securing your database environment is paramount, and RDS Proxy provides several features to enhance the security posture of your applications. Properly configuring these features, along with best practices for both the proxy and the underlying database, is crucial to protect sensitive data and maintain the integrity of your system. This section will delve into the security features offered by RDS Proxy, provide guidance on configuring security groups, and detail best practices for a secure deployment.
IAM Authentication and SSL/TLS
RDS Proxy integrates with AWS Identity and Access Management (IAM) for authentication, allowing you to control access to your database resources based on IAM policies. This integration provides a centralized and secure mechanism for managing database access. Additionally, RDS Proxy supports Secure Sockets Layer/Transport Layer Security (SSL/TLS) encryption for all connections, ensuring that data in transit is protected from eavesdropping.IAM authentication enables fine-grained control over database access.
You can define IAM policies that grant specific permissions to users, groups, or roles, limiting their ability to perform actions on the database. This approach adheres to the principle of least privilege, minimizing the potential impact of a security breach. The following points detail IAM authentication and SSL/TLS.
- IAM Authentication: RDS Proxy can authenticate database connections using IAM credentials. This eliminates the need to store and manage database usernames and passwords within your application code. IAM authentication supports both database user authentication and IAM role-based authentication. For example, a web application running on an EC2 instance can assume an IAM role that grants it permission to connect to the database via the RDS Proxy.
- SSL/TLS Encryption: RDS Proxy supports SSL/TLS encryption for all connections between clients and the proxy, and between the proxy and the database. This protects data in transit from interception. When configuring your database connection, you can specify that SSL/TLS encryption is required. RDS Proxy automatically handles the encryption and decryption of data, ensuring secure communication. This encryption protects data privacy and integrity, safeguarding sensitive information from unauthorized access.
- Certificate Management: RDS Proxy manages SSL/TLS certificates for you. This simplifies the process of securing your database connections and eliminates the need to manually install and renew certificates. The certificates used by RDS Proxy are provided by AWS and are automatically rotated.
Configuring Security Groups for Access Control
Security groups act as virtual firewalls, controlling inbound and outbound traffic to your RDS Proxy and underlying database instances. Properly configuring security groups is essential for limiting access to your database and preventing unauthorized connections. This involves defining rules that specify which IP addresses, CIDR blocks, or other security groups are allowed to connect to the proxy and database.To configure security groups effectively, consider the following points:
- RDS Proxy Security Group: Create a security group specifically for your RDS Proxy. This security group should allow inbound traffic from the resources that need to connect to the database, such as your application servers or other services. The inbound rules should specify the port that the database is listening on (e.g., 3306 for MySQL, 5432 for PostgreSQL).
- Database Instance Security Group: Configure the security group associated with your database instance to allow inbound traffic only from the RDS Proxy’s security group. This restricts direct access to the database instance, enhancing security.
- Restricting Access: Employ the principle of least privilege. Only allow access from the specific IP addresses or security groups that require it. Avoid using overly permissive rules, such as allowing access from the entire internet (0.0.0.0/0).
- Regular Review: Regularly review and audit your security group rules to ensure they remain appropriate and secure. Make necessary adjustments as your infrastructure evolves.
- Example Scenario: Imagine an application running on EC2 instances within a specific subnet. Create a security group for the EC2 instances, allowing outbound traffic to the RDS Proxy security group. The RDS Proxy security group, in turn, should allow inbound traffic from the EC2 instances’ security group and outbound traffic to the database instance security group. The database instance security group should only allow inbound traffic from the RDS Proxy security group.
Best Practices for Securing RDS Proxy and the Underlying Database
Implementing best practices is crucial for a robust and secure database environment. This involves securing both the RDS Proxy itself and the underlying database instance. These practices encompass various aspects, from access control and encryption to monitoring and patching.Consider these practices for a secure deployment:
- Enforce IAM Authentication: Utilize IAM authentication for database connections whenever possible. This simplifies credential management and enhances security by leveraging IAM’s centralized access control.
- Enable SSL/TLS Encryption: Always enforce SSL/TLS encryption for all connections to the RDS Proxy and the database. This protects data in transit from eavesdropping.
- Regularly Update: Keep your RDS Proxy and database instances up-to-date with the latest security patches. AWS regularly releases updates to address vulnerabilities. Enable automatic patching where appropriate.
- Monitor and Log: Enable detailed logging for your RDS Proxy and database instances. Monitor these logs for suspicious activity, such as failed login attempts, unusual queries, or unauthorized access. Use tools like Amazon CloudWatch to analyze logs and set up alerts.
- Use Strong Passwords: If you are using database user accounts, enforce strong passwords and regularly rotate them.
- Limit Database Privileges: Grant database users only the necessary privileges. Avoid granting excessive permissions that could be exploited in the event of a security breach.
- Regular Security Audits: Conduct regular security audits of your database environment to identify and address any vulnerabilities. These audits can be performed internally or by a third-party security specialist.
- Network Segmentation: Isolate your database instances within a private subnet and restrict access to the public internet. This limits the attack surface and prevents unauthorized access.
- Data Encryption at Rest: Enable encryption at rest for your database instances. This encrypts the data stored on the underlying storage volumes, protecting it from unauthorized access even if the storage is compromised.
- Vulnerability Scanning: Regularly scan your RDS Proxy and database instances for vulnerabilities. Use tools like AWS Inspector or third-party vulnerability scanners to identify potential weaknesses.
- Implement a Web Application Firewall (WAF): If your application is exposed to the internet, consider implementing a WAF to protect against common web application attacks, such as SQL injection.
Monitoring and Logging
Monitoring and logging are critical components for maintaining the health, performance, and security of RDS Proxy. Effective monitoring allows for proactive identification and resolution of issues, while comprehensive logging provides valuable insights for troubleshooting, auditing, and capacity planning. This section details the monitoring metrics, log access, and alarm configuration available for RDS Proxy.
Monitoring Metrics for RDS Proxy
RDS Proxy provides a rich set of metrics that can be used to monitor its performance and health. These metrics are accessible through Amazon CloudWatch and offer granular insights into various aspects of the proxy’s operation.
- Connections: These metrics track the number of client connections to the proxy and the number of connections the proxy has established with the database.
- `ClientConnections`: The number of client connections currently connected to the proxy. This metric helps to understand the current load on the proxy.
- `DatabaseConnections`: The number of connections the proxy has established with the database. This metric is important for understanding how the proxy is utilizing database resources.
- Connection Pool: These metrics provide insights into the efficiency of the connection pool.
- `ConnectionPoolBorrow`: The number of times a connection was borrowed from the connection pool.
- `ConnectionPoolCreated`: The number of new database connections created by the proxy.
- `ConnectionPoolReturned`: The number of times a connection was returned to the connection pool.
- `ConnectionPoolWaitTime`: The amount of time clients are waiting for a connection from the pool, measured in milliseconds. High wait times can indicate that the proxy is under heavy load or that the database is not scaling properly.
- `ConnectionPoolMaxConnections`: The maximum number of connections allowed in the connection pool.
- Transactions: Metrics related to database transactions.
- `TransactionsStarted`: The number of transactions started.
- `TransactionsCommitted`: The number of transactions committed.
- `TransactionsRolledBack`: The number of transactions rolled back. This can signal application issues or database errors.
- Queries: Metrics related to database queries.
- `QueriesIssued`: The number of queries issued by clients.
- `QueryLatency`: The time taken to execute queries, measured in milliseconds. High query latency can point to database performance bottlenecks.
- Errors: Metrics related to errors encountered by the proxy.
- `ClientErrors`: The number of errors encountered by the proxy when communicating with clients.
- `DatabaseErrors`: The number of errors encountered by the proxy when communicating with the database.
- CPU Utilization: Metrics tracking the CPU usage of the proxy instances.
- `CPUUtilization`: The percentage of CPU utilization. High CPU utilization can indicate that the proxy is overloaded.
- Memory Utilization: Metrics tracking the memory usage of the proxy instances.
- `MemoryUtilization`: The percentage of memory utilization. High memory utilization can impact proxy performance.
These metrics are crucial for identifying performance bottlenecks, monitoring resource utilization, and diagnosing issues within the RDS Proxy environment. They can be visualized using CloudWatch dashboards for easier monitoring and analysis.
Accessing and Interpreting RDS Proxy Logs
RDS Proxy logs provide detailed information about its operations, including connection attempts, query execution, and errors. Accessing and interpreting these logs is essential for troubleshooting and auditing.
RDS Proxy logs are stored in Amazon CloudWatch Logs. The logs are organized by proxy name and database connection. The logs are structured in JSON format, providing detailed information about each event. The following steps Artikel how to access and interpret these logs:
- Accessing Logs: Navigate to the CloudWatch service in the AWS Management Console. Select “Logs” and then “Log groups.” Locate the log group associated with your RDS Proxy instance. The log group name typically follows the pattern `/aws/rds/proxy/
`. - Log Structure: Each log entry contains detailed information, including:
- Timestamp: The time the event occurred.
- Log level: Indicates the severity of the event (e.g., INFO, WARN, ERROR).
- Event ID: A unique identifier for the event.
- Event type: Describes the type of event (e.g., CONNECTION_ATTEMPT, QUERY, ERROR).
- Details: Contains specific information about the event, such as client IP address, database user, SQL query, and error messages.
- Filtering Logs: CloudWatch Logs allows filtering based on log level, event type, and specific s. This can be used to narrow down the scope of the search and identify relevant events. For example, filtering by “ERROR” level helps quickly identify potential issues.
- Log Insights: CloudWatch Logs Insights provides powerful query capabilities to analyze the logs. You can use SQL-like queries to extract specific information, calculate metrics, and identify patterns in the logs. For instance, you can query for the number of queries executed per second or the number of connection attempts from a specific IP address.
By analyzing these logs, administrators can identify and resolve issues such as connection failures, performance bottlenecks, and security threats. For example, a sudden increase in `DatabaseErrors` in the logs might indicate a database outage or a configuration issue.
Setting Up CloudWatch Alarms for RDS Proxy
Setting up CloudWatch alarms for RDS Proxy enables proactive monitoring and automated responses to potential issues. Alarms trigger notifications when specified metric thresholds are breached, allowing timely intervention.
The following steps Artikel the process for setting up CloudWatch alarms:
- Choose Metrics: Select the appropriate metrics to monitor based on the critical aspects of RDS Proxy performance. Key metrics include `ConnectionPoolWaitTime`, `DatabaseConnections`, `CPUUtilization`, `MemoryUtilization`, `ClientErrors`, and `DatabaseErrors`.
- Define Thresholds: Determine the threshold values for each metric that, when exceeded, should trigger an alarm. These thresholds should be based on baseline performance and acceptable operational parameters. For example:
- Set an alarm for `ConnectionPoolWaitTime` if the average wait time exceeds a certain threshold (e.g., 500 milliseconds) for a sustained period (e.g., 5 minutes).
- Set an alarm for `CPUUtilization` if it consistently exceeds a high percentage (e.g., 80%) for a sustained period (e.g., 5 minutes).
- Set an alarm for `DatabaseErrors` if the count exceeds a certain threshold (e.g., 10 errors) within a certain time period (e.g., 1 minute).
- Configure Alarm Actions: Define the actions to be taken when an alarm transitions to the ALARM state. These actions can include:
- Sending notifications via Amazon SNS to relevant stakeholders (e.g., operations team, database administrators).
- Automatically scaling the RDS Proxy instance (e.g., using Auto Scaling) to increase capacity if `CPUUtilization` or `DatabaseConnections` are high.
- Triggering AWS Lambda functions to perform automated remediation steps.
- Test Alarms: After creating the alarms, it is crucial to test them to ensure they are functioning correctly. This can be done by simulating conditions that would trigger the alarms. For example, you can simulate high connection loads to test the `ConnectionPoolWaitTime` alarm or simulate database errors to test the `DatabaseErrors` alarm.
By implementing these steps, administrators can establish a robust monitoring and alerting system for RDS Proxy, ensuring optimal performance, availability, and security.
Performance Optimization
RDS Proxy offers several avenues for optimizing database performance by efficiently managing and scaling database connections. Understanding and implementing these techniques can significantly reduce latency, improve throughput, and ultimately enhance the overall responsiveness of database-driven applications. The following sections delve into specific strategies and configurations to maximize the benefits of using RDS Proxy.
Optimizing RDS Proxy Performance Techniques
Several techniques can be employed to optimize the performance of RDS Proxy, leveraging its connection pooling and other features. These optimizations directly impact the efficiency with which connections are handled, leading to faster response times and better resource utilization.
- Connection Pooling Configuration: Fine-tuning connection pool settings is crucial. The `MaxConnections` setting dictates the maximum number of concurrent connections the proxy can maintain. Setting this value too low can limit concurrency, while setting it too high can lead to resource exhaustion on the proxy or the database instance. The optimal value depends on the application’s workload and the database instance’s capacity.
Experimentation and monitoring are vital to determine the ideal setting.
- Connection Idle Timeout: The `IdleClientTimeout` setting controls how long idle connections remain open. Shorter timeouts can free up connections more quickly, preventing them from being held open unnecessarily. However, very short timeouts can lead to frequent connection establishment and teardown, which can introduce overhead. A balance must be struck to minimize both idle connection waste and connection churn.
- Database Instance Selection: When using RDS Proxy with read replicas, consider the load balancing strategy. The proxy can distribute read traffic across available replicas. Monitoring the replica’s performance and health is critical to prevent routing traffic to overloaded or unhealthy replicas. Ensure replicas are properly sized and configured to handle the expected read load.
- Caching Queries: Although RDS Proxy doesn’t natively cache query results, integrating caching mechanisms at the application or database level can reduce the load on both the proxy and the database. Popular caching solutions like Redis or Memcached can be used to store frequently accessed data, minimizing the need to query the database.
- Monitoring and Alerting: Implementing comprehensive monitoring is essential for identifying performance bottlenecks. Monitor metrics such as connection pool utilization, connection latency, CPU utilization, and memory usage on both the proxy and the database instance. Set up alerts to proactively identify and address performance issues.
- Connection Keep-Alive: Ensure that connection keep-alive settings are correctly configured at the application and proxy levels. Keep-alive mechanisms prevent connections from being prematurely closed due to network timeouts, which can reduce connection churn.
Performance Impact of Different RDS Proxy Configurations
The configuration of RDS Proxy has a direct impact on its performance characteristics. Understanding how different settings affect metrics like latency, throughput, and connection utilization is essential for optimizing performance.
- Connection Pool Size: Increasing the `MaxConnections` setting can improve throughput by allowing more concurrent connections. However, it also increases the resource consumption of the proxy. Experimenting with different values is necessary to find the optimal balance for a specific workload. If the pool size is too small, the application may experience connection bottlenecks. If the pool size is too large, the proxy might consume excessive resources, impacting its overall performance.
- Idle Timeout: A shorter `IdleClientTimeout` can free up connections more quickly, but it can also lead to more frequent connection establishment and teardown, which increases overhead. Longer timeouts can reduce connection churn but might result in more idle connections being held open.
- Database Instance Size: The size of the database instance directly affects the performance of RDS Proxy. A larger instance can handle more connections and queries, which leads to better performance, especially under heavy load. If the database instance is under-provisioned, it can become a bottleneck, regardless of the RDS Proxy configuration.
- Network Latency: Network latency between the application, the RDS Proxy, and the database instance can significantly impact performance. Minimizing network latency is crucial. This can be achieved by placing the application, the proxy, and the database in the same AWS region and using optimized network configurations.
- Read Replica Configuration: The number and size of read replicas influence read throughput. More read replicas can handle more read traffic. Properly sized replicas are essential to ensure that the load is distributed effectively.
Recommendations for Tuning Database Connections Through RDS Proxy
Tuning database connections through RDS Proxy requires a systematic approach that involves monitoring, experimentation, and iterative refinement. The following recommendations provide a framework for optimizing connection management.
- Establish a Baseline: Before making any changes, establish a baseline performance by monitoring key metrics such as connection pool utilization, latency, and throughput. This baseline provides a reference point for evaluating the impact of subsequent changes.
- Monitor Key Metrics: Continuously monitor the performance of RDS Proxy and the database instance using CloudWatch or other monitoring tools. Track metrics such as connection pool utilization, connection latency, CPU utilization, memory usage, and database query performance.
- Iterative Tuning: Make changes to the RDS Proxy configuration incrementally and test the impact of each change. Avoid making multiple changes simultaneously, as this makes it difficult to isolate the cause of any performance improvements or degradations.
- Adjust Connection Pool Size: Carefully adjust the `MaxConnections` setting based on the application’s workload and the database instance’s capacity. Start with a conservative value and gradually increase it while monitoring performance.
- Optimize Idle Timeout: Tune the `IdleClientTimeout` setting to balance connection churn and idle connection waste. Shorter timeouts can free up connections more quickly, but they can also increase overhead.
- Load Balancing and Replica Selection: If using read replicas, monitor the health and performance of each replica and ensure that traffic is distributed effectively. Adjust the load balancing strategy as needed.
- Regular Review: Regularly review the RDS Proxy configuration and performance metrics to ensure that the settings are still optimal. As the application’s workload evolves, the optimal configuration may change.
- Use Database-Specific Optimizations: Apply database-specific optimization techniques, such as indexing, query optimization, and schema design, to improve overall database performance. RDS Proxy is a connection management tool, not a substitute for database optimization.
Troubleshooting Common Issues
RDS Proxy, while designed to enhance database connection management, can sometimes present challenges. Effective troubleshooting requires a systematic approach, encompassing the identification of common problems, understanding their root causes, and implementing appropriate solutions. This section provides a comprehensive guide to diagnosing and resolving issues that may arise when utilizing RDS Proxy.
Common Issues Encountered with RDS Proxy
Several issues can hinder the performance or availability of RDS Proxy. These problems can stem from configuration errors, network issues, database-related problems, or limitations within the proxy itself. Understanding these common pitfalls is crucial for effective troubleshooting.
- Connection Refusals: Clients are unable to establish connections to the RDS Proxy endpoint. This can manifest as “connection refused” errors.
- Connection Timeouts: Connections to the RDS Proxy take an excessively long time or fail to establish within a specified timeframe.
- Performance Degradation: Database query performance is slower than expected when routed through the RDS Proxy.
- High Latency: Increased delay in database response times, potentially affecting application responsiveness.
- Error Logs: The RDS Proxy or database logs reveal error messages indicating connection problems, query failures, or internal issues.
- Unexpected Behavior: Applications exhibit unusual behavior, such as intermittent connection drops or incorrect data retrieval.
- Resource Exhaustion: The RDS Proxy or the underlying database server may experience resource exhaustion (e.g., CPU, memory, connections).
Troubleshooting Connection Problems
Connection problems are frequently encountered, often stemming from misconfigurations, network interruptions, or database server issues. A methodical approach to troubleshooting is vital for pinpointing the source of these issues.
The initial step in addressing connection problems involves verifying the basic connectivity and configuration.
- Verify Network Connectivity: Ensure the client can reach the RDS Proxy endpoint using tools like `ping` or `traceroute`. This confirms network reachability.
- Check Security Group Rules: Verify that the security groups associated with the RDS Proxy and the database instance allow traffic from the client’s IP address or security group. Ensure the correct ports (typically 3306 for MySQL and PostgreSQL) are open.
- Confirm Proxy Endpoint and Credentials: Double-check the RDS Proxy endpoint address, port, and the database credentials used by the client. Typos or incorrect credentials are frequent causes of connection failures.
- Examine RDS Proxy Configuration: Review the RDS Proxy configuration within the AWS Management Console or using the AWS CLI. Ensure the target database instance is correctly specified and the proxy is active.
- Inspect Database Instance Status: Verify the database instance is running and accessible. Check for any maintenance windows or outages that might be impacting availability.
- Examine Client-Side Configuration: Confirm the client application is configured to connect to the RDS Proxy endpoint instead of directly to the database instance. Check the connection string and any related settings.
- Review RDS Proxy Logs: The RDS Proxy logs (available through CloudWatch Logs) provide valuable insights into connection attempts, errors, and performance metrics. Analyze these logs for clues about connection failures or other issues.
Checklist for Diagnosing and Resolving RDS Proxy-Related Issues
A structured checklist can facilitate the systematic diagnosis and resolution of issues related to RDS Proxy. This checklist promotes a consistent approach and helps prevent overlooking critical steps.
This checklist Artikels a systematic approach to diagnose and resolve RDS Proxy-related issues, providing a structured method for troubleshooting.
- Connectivity Verification:
- Can the client reach the RDS Proxy endpoint (e.g., using `ping`)?
- Are security group rules correctly configured to allow traffic?
- Is the client’s IP address or security group authorized?
- Configuration Validation:
- Is the RDS Proxy endpoint address and port correct?
- Are the database credentials accurate?
- Is the RDS Proxy active and configured correctly in AWS?
- Is the target database instance specified correctly?
- Database Instance Status:
- Is the database instance running and accessible?
- Are there any scheduled maintenance windows or outages?
- Client-Side Configuration:
- Is the client configured to connect to the RDS Proxy endpoint?
- Are the connection string and settings accurate?
- Log Analysis:
- Review the RDS Proxy logs in CloudWatch Logs for errors and warnings.
- Examine database instance logs for related issues.
- Check for any unusual patterns or error messages.
- Performance Testing:
- Measure query performance through the RDS Proxy.
- Compare performance to direct database connections.
- Identify potential bottlenecks.
- Resource Monitoring:
- Monitor CPU, memory, and connection usage on the RDS Proxy and database instance.
- Identify resource exhaustion issues.
- Troubleshooting Steps:
- Restart the RDS Proxy instance (if necessary).
- Adjust connection pool settings.
- Optimize database queries.
- Scale the RDS Proxy or database instance (if needed).
Using RDS Proxy with Different Applications
RDS Proxy’s versatility stems from its ability to seamlessly integrate with various applications, regardless of the programming language or database client used. This section provides practical guidance on configuring applications to leverage RDS Proxy, offering concrete examples and connection string configurations to facilitate immediate implementation. Understanding these configurations is crucial for maximizing the benefits of RDS Proxy, including enhanced connection management, improved performance, and increased database security.
Configuring Applications to Use RDS Proxy
The process of configuring an application to use RDS Proxy typically involves modifying the database connection string to point to the proxy endpoint instead of the database instance endpoint. This change redirects all database traffic through the proxy, allowing it to manage connections, pool resources, and provide other benefits. The specific steps vary depending on the programming language, database client, and application framework employed.
However, the core principle remains consistent: updating the connection string to reflect the proxy’s address and any necessary authentication credentials.
Examples of Connecting to RDS Proxy Using Various Programming Languages
Several programming languages and database clients commonly interact with databases. Demonstrating the connection process with RDS Proxy across diverse environments offers a comprehensive understanding of its adaptability. The following examples illustrate how to connect to an RDS Proxy instance using popular programming languages, emphasizing the connection string configuration as the key modification.
- Python with `psycopg2` (PostgreSQL): In Python, using the `psycopg2` library, the connection string is modified to include the RDS Proxy endpoint, database name, username, password, and port (typically 5432 for PostgreSQL).
- Java with JDBC (MySQL): Java applications utilizing JDBC drivers for MySQL also require adjustments to the connection string. The endpoint, database name, username, password, and port (typically 3306 for MySQL) are specified in the connection URL.
- Node.js with `mysql2` (MySQL): Node.js applications using the `mysql2` package require similar connection string modifications. The host, database name, username, password, and port are configured to point to the RDS Proxy.
- PHP with `mysqli` (MySQL): PHP scripts using the `mysqli` extension are configured by updating the database host, username, password, and database name within the `mysqli_connect()` function or its equivalent.
Connection Strings for Different Database Clients and Programming Languages
The table below provides a concise overview of connection string examples for different database clients and programming languages, illustrating the required parameters for connecting to an RDS Proxy. The examples assume the RDS Proxy endpoint is `your-proxy-endpoint.proxy-endpoint.rds.amazonaws.com` and the database name is `your_database`. Replace the placeholder values with your actual credentials.
| Programming Language/Client | Database | Connection String Example | Explanation |
|---|---|---|---|
| Python (psycopg2) | PostgreSQL | conn = psycopg2.connect(host='your-proxy-endpoint.proxy-endpoint.rds.amazonaws.com', database='your_database', user='your_username', password='your_password', port=5432) | This example uses the `psycopg2` library to connect to a PostgreSQL database through the RDS Proxy. The connection string specifies the proxy endpoint, database name, username, password, and port. |
| Java (JDBC) | MySQL | String url = "jdbc:mysql://your-proxy-endpoint.proxy-endpoint.rds.amazonaws.com:3306/your_database"; Connection conn = DriverManager.getConnection(url, "your_username", "your_password"); | This Java example uses JDBC to connect to a MySQL database via RDS Proxy. The connection URL includes the proxy endpoint, database name, and port. The `DriverManager.getConnection()` method also requires username and password. |
| Node.js (mysql2) | MySQL | const connection = mysql.createConnection( host: 'your-proxy-endpoint.proxy-endpoint.rds.amazonaws.com', user: 'your_username', password: 'your_password', database: 'your_database', port: 3306 ); | This Node.js example uses the `mysql2` package to connect to a MySQL database through the RDS Proxy. The connection parameters specify the proxy host, username, password, database name, and port. |
| PHP (mysqli) | MySQL | $conn = mysqli_connect("your-proxy-endpoint.proxy-endpoint.rds.amazonaws.com", "your_username", "your_password", "your_database", 3306); | This PHP example utilizes the `mysqli` extension to connect to a MySQL database through the RDS Proxy. The connection function includes the proxy host, username, password, database name, and port. |
Closing Summary
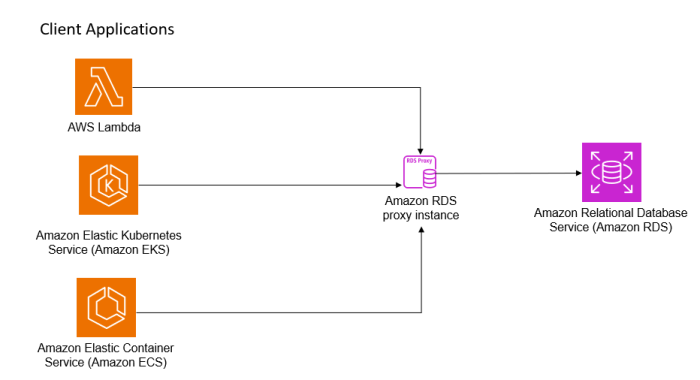
In conclusion, RDS Proxy represents a significant advancement in database connection management. By implementing connection pooling, enhancing security, and simplifying failover mechanisms, it provides a vital layer of abstraction and optimization. Understanding the principles of RDS Proxy, from initial setup to ongoing monitoring, empowers developers and database administrators to build more resilient, scalable, and secure applications. Leveraging RDS Proxy effectively ensures that database interactions are optimized, thereby enhancing the overall performance and reliability of your applications.
Clarifying Questions
What are the primary benefits of using RDS Proxy?
RDS Proxy offers connection pooling, which reduces database load and improves application responsiveness. It enhances security by minimizing direct database access and provides built-in failover support, increasing application availability. It also simplifies database credentials management.
Does RDS Proxy support all database engines?
RDS Proxy supports a variety of database engines, including MySQL, PostgreSQL, MariaDB, and SQL Server. However, the specific versions supported vary; always refer to the official AWS documentation for the most up-to-date compatibility information.
How does RDS Proxy handle database failover?
RDS Proxy automatically detects database failover events. It then redirects client connections to the new primary database instance, minimizing downtime and ensuring application continuity. This process is managed internally by RDS Proxy, without requiring application-level changes.
What security measures are integrated into RDS Proxy?
RDS Proxy integrates with AWS IAM for authentication and authorization. It supports SSL/TLS encryption for secure communication between clients and the proxy. It also allows you to configure security groups to control network access to the proxy and the underlying database.
How can I monitor the performance of RDS Proxy?
RDS Proxy provides a set of CloudWatch metrics, including connection counts, latency, and error rates. These metrics allow you to monitor the performance and health of the proxy and identify potential issues. You can also set up CloudWatch alarms to be notified of performance anomalies.