Domain-driven design (DDD) is a powerful approach to software development that emphasizes understanding the business domain. A crucial concept within DDD is the bounded context, a carefully defined segment of the system that encapsulates specific business concerns. This structured approach allows for focused development, clear communication, and maintainable systems. Understanding bounded contexts is key to building robust and adaptable software that aligns precisely with business needs.
This exploration delves into the intricacies of bounded contexts, outlining their purpose, identification, and practical application within the realm of domain-driven design. We will examine how to define boundaries, map contexts, manage communication, and ensure data consistency. Furthermore, we will address the challenges and opportunities presented by adapting and evolving these contexts.
Defining Bounded Contexts
A bounded context is a well-defined segment of a software system’s domain where specific business rules and concepts apply. It’s a crucial component of Domain-Driven Design (DDD), enabling teams to focus on a manageable subset of the overall system, fostering greater clarity, and simplifying development.The rationale behind using bounded contexts is to isolate the complexity of a large system.
By dividing the system into smaller, focused areas, teams can better understand and manage the intricacies of each domain, improving communication and reducing ambiguity. This localized focus promotes a shared understanding of the domain, leading to more robust and maintainable software.
Bounded Context Definition
A bounded context in Domain-Driven Design is a self-contained segment of a software system that encapsulates a specific domain of knowledge and business logic. It’s a circumscribed area where the domain model is valid and specific rules and concepts apply. Bounded contexts promote clarity and consistency by defining boundaries around specific areas of the system’s functionality, enabling teams to focus on particular business domains.
Purpose and Rationale
The purpose of employing bounded contexts is to foster a shared understanding of the domain amongst team members. This shared understanding simplifies communication and reduces ambiguity, thereby enhancing collaboration and reducing the risk of inconsistencies. The rationale behind this approach is to manage the complexity of large systems. By breaking down the system into smaller, manageable pieces, developers can concentrate on a specific domain model without getting overwhelmed by the overall system’s complexity.
This leads to better-defined requirements, improved code quality, and easier maintenance in the long run.
Characteristics of Bounded Contexts
Bounded contexts are distinct from other contexts within a system. Key characteristics that distinguish them include:
- Specific Domain of Knowledge: Each bounded context focuses on a specific part of the overall system, concentrating on a particular domain of knowledge and business rules. This allows for specialized expertise and understanding within the context.
- Independent Evolution: Bounded contexts can evolve independently of other parts of the system. This allows teams to adapt to changing requirements without impacting the entire system.
- Unique Domain Model: Each bounded context has its own domain model, which defines the objects, relationships, and rules relevant to that specific area.
- Distinct Communication Patterns: Different bounded contexts may employ different communication strategies, such as message queues or shared databases, to exchange information with other parts of the system.
Examples of Bounded Contexts
Different types of bounded contexts can be found in software systems. For example:
- E-commerce System: This could contain bounded contexts for product catalog management, order processing, and customer relationship management (CRM).
- Banking Application: Examples include bounded contexts for account management, loan processing, and transaction processing.
- Hospital Management System: This system might contain bounded contexts for patient records, appointment scheduling, and billing.
Key Features of Bounded Contexts
The table below illustrates the key features of bounded contexts, highlighting their importance in maintaining a well-structured and manageable system.
| Feature | Description |
|---|---|
| Domain of Focus | The specific area of the system’s functionality that the context covers. |
| Domain Model | The set of objects, relationships, and rules that define the context’s domain. |
| Communication Patterns | The methods used to exchange information between the context and other parts of the system. |
| Evolutionary Independence | The ability of the context to evolve without impacting other parts of the system. |
| Team Ownership | The team responsible for managing and maintaining the context. |
Identifying Boundaries
Defining the boundaries of a bounded context is crucial for effective domain-driven design. Clear delimitation ensures that teams focus on specific business concerns and avoid unnecessary complexity. This section details various methods and considerations for identifying and establishing these boundaries.Identifying the precise scope of a bounded context is not a one-size-fits-all process. It requires careful consideration of the business domain, stakeholder needs, and the specific goals of the project.
Different approaches may be more appropriate depending on the context.
Methods for Identifying Boundaries
Several approaches can be used to define the boundaries of a bounded context. These include analyzing business capabilities, identifying shared understanding, and examining existing systems and processes. A crucial aspect is to understand what information and functionality need to be included within the bounded context. This often involves collaboration and dialogue with stakeholders.
- Analyzing Business Capabilities: This method involves identifying the key business functions and processes that the bounded context will address. For example, if a company sells products online, a bounded context for the “order management” function might focus on the entire process from customer order placement to fulfillment. This includes order entry, inventory management, shipping, and payment processing within the context of that capability.
- Identifying Shared Understanding: Understanding how stakeholders perceive and interact with the system is crucial. Discussions with stakeholders, including domain experts and business users, help clarify what information and functionalities are relevant to the bounded context. For example, the stakeholders may agree that the “order management” bounded context should not include the complex product design process, which may belong to a different bounded context.
- Examining Existing Systems and Processes: Existing systems and processes often provide valuable clues about the boundaries of a bounded context. A detailed review of the current workflows, data flows, and system interactions can pinpoint the relevant aspects of the business domain. For example, if an existing system handles order fulfillment, this system’s scope and limitations can help define the boundary of the “order management” bounded context.
Examples of Delimiting Scope
Illustrating how to delimit the scope of a bounded context involves demonstrating specific examples. A common example is the “order management” bounded context within an e-commerce platform. This bounded context might not include the complex product design or marketing processes, which could be handled in other bounded contexts.
Role of Stakeholders in Defining Boundaries
Stakeholders play a critical role in defining bounded context boundaries. Their input is essential for understanding the needs and requirements of the system and for ensuring the bounded context aligns with the business goals. Collaboration with stakeholders helps ensure that the boundaries are well-defined and reflect the actual needs of the business.
Comparing Approaches to Defining Bounded Contexts
The following table provides a comparison of different approaches to defining bounded contexts, highlighting their strengths and weaknesses:
| Approach | Strengths | Weaknesses |
|---|---|---|
| Analyzing Business Capabilities | Focuses on core business functions, providing a clear scope. | May miss some dependencies or integrations with other contexts. |
| Identifying Shared Understanding | Ensures alignment with stakeholder expectations. | Can be time-consuming and require extensive collaboration. |
| Examining Existing Systems and Processes | Leverages existing knowledge and infrastructure. | May not reflect future needs or changes in the business. |
Identifying Scope Based on Business Capabilities
Identifying the scope of a bounded context based on business capabilities involves recognizing the distinct parts of a business that can be treated as independent units. For instance, a company’s customer service department could be a bounded context, focusing on customer interactions and support. This is distinct from the bounded context for order management, even though both might share some data.
Clearly defining the scope based on business capabilities ensures that each bounded context focuses on a specific and manageable set of functionalities.
Context Mapping

Context mapping is a crucial aspect of Domain-Driven Design (DDD), providing a visual representation of the relationships between bounded contexts within a software system. It helps teams understand the scope of each bounded context and how they interact, facilitating communication and collaboration during the development process. A well-defined context map promotes a shared understanding of the system’s architecture and ensures consistency across different teams working on separate parts of the application.Context mapping goes beyond simply identifying bounded contexts; it illustrates how these contexts relate to one another, both in terms of dependencies and potential conflicts.
This visual representation is vital for maintaining a cohesive and well-structured software system, ensuring that changes in one bounded context do not negatively impact others. This detailed understanding of interactions is essential for maintaining a system’s long-term maintainability and scalability.
Context Mapping and Bounded Contexts
Context mapping is a powerful tool for visualizing the relationships between bounded contexts. It demonstrates how different parts of a system interact and depend on each other. This visual representation helps in identifying potential conflicts and dependencies between bounded contexts, thus facilitating better communication and collaboration among development teams.
Steps in Creating a Context Map
Understanding the steps involved in creating a context map is essential for its effective application. A well-defined process ensures clarity and accuracy in representing the system’s architecture.
- Identify Bounded Contexts: The first step involves clearly defining the bounded contexts within the system. This necessitates a thorough understanding of the domain and its different sub-domains, which in turn helps identify the areas where specific business logic and data are focused. This is critical for separating concerns and promoting modularity in the design.
- Define Relationships: Once the bounded contexts are identified, the relationships between them need to be established. This includes identifying dependencies, shared responsibilities, and potential conflicts. Understanding these relationships is crucial for making informed design decisions and minimizing conflicts later on in the development cycle.
- Visual Representation: A visual representation of the bounded contexts and their relationships is created. This is often done using a diagram, where each bounded context is represented as a box or other visual element, and the relationships are depicted using lines or arrows. The chosen visual style should be clear and easy to understand.
- Iterative Refinement: The context map is not a static document. It should be regularly reviewed and updated as the system evolves. As new requirements emerge or the understanding of the domain deepens, the context map should be adjusted to reflect these changes.
Examples of Context Maps and Significance
Context maps provide valuable insights into the architecture of a system. Different types of context maps can highlight various aspects of a system’s organization. A well-constructed context map can provide a framework for effective communication and collaboration among development teams.
- Microservice Architecture: In a microservice architecture, context maps are used to illustrate how different microservices interact and communicate. This helps in understanding the dependencies and potential conflicts between the different services, allowing for more efficient and effective management of the system.
- Enterprise Applications: Context maps are particularly useful in complex enterprise applications, where multiple teams may be working on different parts of the system. They facilitate clear communication and shared understanding of the interactions between the various bounded contexts.
Sample Context Map
A sample context map with multiple bounded contexts and their interactions illustrates the application of context mapping in a practical setting. This example will demonstrate how bounded contexts are interconnected. 
Note: The image (context_map_example.png) would depict a diagram showcasing various bounded contexts like ‘Order Management’, ‘Inventory Management’, ‘Customer Relationship Management’, and ‘Payment Processing’. Arrows between the boxes would indicate dependencies, such as ‘Order Management’ depending on ‘Inventory Management’ for stock availability. This representation would visually depict the complex interactions within the system.
Types of Relationships Between Bounded Contexts
The table below Artikels the different types of relationships between bounded contexts, highlighting their significance.
| Relationship Type | Description | Significance |
|---|---|---|
| Dependency | One context relies on another for functionality or data. | Dependencies must be managed carefully to avoid cascading failures. |
| Shared Responsibility | Multiple contexts share the same data or functionality. | Coordination and consistency are crucial to avoid conflicts. |
| Interaction | Contexts communicate and exchange information. | Communication protocols and data formats must be clearly defined. |
| Independent | Contexts have no direct interaction or dependency. | These contexts can be developed and maintained independently. |
Communication & Data Exchange
Bounded contexts, by definition, encapsulate specific business concerns. Effective communication and data exchange between these contexts are crucial for a cohesive and well-functioning system. This section delves into the strategies and approaches used to connect and share information between these distinct domains.Inter-context communication requires careful planning and consideration of data structures, formats, and protocols. Different approaches cater to various communication needs, ensuring data integrity and maintainability.
Consistent data models are essential for preventing data silos and ensuring a unified view of the business domain across contexts.
Communication Approaches
Bounded contexts interact using various approaches, each with advantages and disadvantages. The best choice depends on the specific needs of the interaction, such as frequency, complexity, and data volume.
- API-based communication is a common approach where bounded contexts expose APIs for external consumption. This allows for controlled and structured interactions, enabling other contexts to request data and trigger actions in a well-defined manner. For instance, an e-commerce context might expose an API for order processing, allowing a fulfillment context to access order details for logistics operations.
- Message queues facilitate asynchronous communication. One context publishes messages to a queue, and another context subscribes to receive and process those messages. This approach is particularly suitable for handling events and non-critical interactions. For example, a user registration context might publish a new user registration event to a queue, and a welcome email context could subscribe to process and send welcome emails.
- Database integration involves using a shared database schema or employing specific database mechanisms for communication. This can be effective for simple interactions but can lead to dependencies and challenges in scaling or maintaining data consistency.
Data Exchange Approaches
Data exchange between contexts requires carefully designed data formats and mappings. These ensure that data is interpreted correctly by the receiving context.
- Data transfer objects (DTOs) are a common method for encapsulating data for exchange. They define the structure and format of the exchanged data, ensuring consistency and avoiding unintended side effects. DTOs often map to specific domain entities or attributes in each context, facilitating data transformation and handling complex structures.
- Event-driven architecture facilitates communication through events. One context publishes an event, and other contexts subscribe to receive and react to it. This allows for loose coupling and avoids direct dependencies between contexts.
Importance of Consistent Data Models
A consistent data model across bounded contexts is critical for data integrity and interoperability. This involves defining common data structures, ensuring that the same data means the same thing in different contexts. Inconsistent data models can lead to data discrepancies, errors, and difficulties in system integration.
Ensuring Consistent Data Exchange
Maintaining data consistency across contexts requires careful planning and execution.
- Data mapping and transformation are crucial steps to translate data between contexts. Rules and processes for converting data between formats are essential for avoiding data loss or corruption. Tools and frameworks facilitate these transformations.
- Versioning of data schemas is essential to support changes and evolution in different contexts. A clear versioning strategy allows for managing and tracking data modifications.
- Data validation helps to maintain data quality and ensure data integrity across contexts. Validation rules and procedures ensure that data meets the expected criteria in each context.
Communication Protocols
Different communication protocols cater to various needs. The choice depends on factors like performance requirements, security needs, and complexity.
| Protocol | Description | Use Case |
|---|---|---|
| RESTful APIs | Representational State Transfer APIs | Common approach for exchanging data between contexts, especially for web applications. |
| GraphQL | Query language for APIs | Allows clients to request specific data, improving efficiency and reducing data transfer. |
| Message Queues (e.g., RabbitMQ, Kafka) | Asynchronous messaging | Suitable for handling events, notifications, and non-critical interactions. |
| gRPC | High-performance, language-agnostic RPC framework | Ideal for microservice architectures requiring high-performance and efficient communication. |
Language & Ubiquitous Language
A crucial element of successful domain-driven design within bounded contexts is the establishment of a shared vocabulary, often referred to as a ubiquitous language. This shared language fosters a common understanding among all stakeholders, ensuring that everyone is on the same page when discussing domain concepts. A consistent and precise language reduces ambiguity and promotes clarity in communication.A ubiquitous language within a bounded context acts as a bridge between the business domain and the software implementation.
It allows developers to accurately translate complex business concepts into code and provides a common ground for stakeholders to validate the system’s design and functionality. This common understanding simplifies communication and reduces the potential for misunderstandings.
The Role of Ubiquitous Language
A ubiquitous language within a bounded context plays a vital role in maintaining a consistent understanding of domain concepts. It ensures that everyone, from domain experts to developers, speaks the same language when discussing business processes and rules. This shared understanding is fundamental for building software that accurately reflects the business domain.
Importance of a Shared Vocabulary
A shared vocabulary within a bounded context is essential for effective communication and collaboration. It ensures that everyone involved in the project – including domain experts, analysts, developers, and testers – understands the domain concepts in the same way. This shared understanding minimizes ambiguity, streamlines discussions, and ultimately leads to a more accurate and robust software solution.
Establishing a Ubiquitous Language
Establishing a ubiquitous language involves several key steps. First, identify the key concepts and terminology within the domain. Then, define precise and unambiguous definitions for each concept. These definitions should be readily accessible to all stakeholders and consistently applied throughout the project. Thorough documentation is critical for ensuring consistency and preventing misinterpretations.
Workshops, meetings, and discussions with domain experts are effective ways to achieve this. The process often includes reviewing existing documentation, brainstorming, and iterating on definitions.
Developing a Shared Language Across Bounded Contexts
Developing a shared language across different bounded contexts requires careful consideration of the relationships between these contexts. It often involves establishing a common language for frequently shared domain concepts. This approach may involve identifying shared terms and creating a glossary of terms to maintain consistency across contexts. It is important to note that complete alignment may not be possible, especially with complex or distinct domains.
However, a common vocabulary for shared concepts is often achievable. A key consideration is that a common language doesn’t necessitate identical terms in every context; rather, it ensures a common understanding and translation mechanisms.
Approaches to Building a Ubiquitous Language
Different approaches can be adopted to build a ubiquitous language within a bounded context. These approaches often vary based on the complexity of the domain and the level of detail required.
| Approach | Description |
|---|---|
| Collaborative Workshops | Bringing together domain experts, developers, and other stakeholders for focused discussions on domain concepts and terminology. |
| Concept Modeling | Using diagrams and models to visualize and represent domain concepts, facilitating a shared understanding. |
| Glossary Creation | Developing a comprehensive glossary that defines terms and their usage, ensuring consistent application across the project. |
| Iterative Refinement | Continuously reviewing and refining the language based on feedback from stakeholders and project experience, ensuring it accurately reflects the domain’s nuances. |
Data Modeling
Data modeling within a bounded context is a crucial aspect of domain-driven design. It involves defining the structure and relationships of data specific to that particular context. A well-defined data model ensures that data is organized efficiently, facilitating effective communication and minimizing ambiguity. This process plays a significant role in the overall success of a software project.Effective data modeling within a bounded context hinges on a clear understanding of the specific domain and its intricacies.
By carefully considering the entities, attributes, and relationships within the domain, developers can create a data model that accurately reflects the real-world processes and constraints. This structured approach guarantees data integrity and enables the system to function effectively within its designated context.
Data Modeling Approaches
Different data modeling approaches cater to various needs and complexities. Understanding the nuances of each approach allows for informed decisions in designing a data model tailored to the bounded context.
- Relational Databases: This traditional approach uses tables to store data and relationships between them. It’s robust and well-established, providing strong data integrity and security. This approach often utilizes foreign keys to establish links between entities, guaranteeing data consistency. Examples include applications involving financial transactions, inventory management, or customer relationship management (CRM).
- Object-Oriented Databases: These databases model data using objects, reflecting the object-oriented programming paradigm. Data is structured around classes and objects, mimicking real-world entities and their relationships. This approach often leads to simpler data models for complex systems, but might not always be as performant as relational models for certain operations. Examples include applications requiring complex object hierarchies, such as content management systems or multimedia databases.
- NoSQL Databases: NoSQL databases offer flexible schemas and scalability, making them suitable for rapidly evolving datasets. They can handle vast quantities of data with varying structures. However, maintaining data consistency can be challenging compared to relational databases. Examples include applications handling social media feeds, online gaming, or large-scale e-commerce transactions.
Consistency Across Bounded Contexts
Ensuring consistency in data models across bounded contexts is essential for preventing conflicts and maintaining data integrity. Data structures should align across the bounded contexts to avoid ambiguity and data discrepancies. Inconsistencies in data representation can cause significant integration issues.
Trade-offs in Data Modeling Approaches
Choosing the right data modeling approach involves evaluating trade-offs between factors like scalability, performance, complexity, and data consistency. The complexity of the domain and the volume of data will influence the selection of the best data model. Consider the following factors when selecting an approach:
- Scalability: The ability of the data model to handle increasing amounts of data and user load.
- Performance: The speed and efficiency of data retrieval and manipulation.
- Complexity: The ease of designing, implementing, and maintaining the data model.
- Data Consistency: The ability to maintain data accuracy and integrity across the system.
Comparison of Data Models
The table below contrasts the key characteristics of different data modeling approaches.
| Data Model | Scalability | Performance | Complexity | Consistency |
|---|---|---|---|---|
| Relational | Good | Good | Medium | High |
| Object-Oriented | Medium | Variable | High | Medium |
| NoSQL | Excellent | Variable | Low | Medium |
Interaction with Other Contexts
Effective interaction between bounded contexts is crucial for a successful Domain-Driven Design implementation. A well-defined strategy for communication and data exchange between these contexts minimizes integration complexities and promotes a cohesive system. This section explores various interaction strategies, emphasizing the importance of clear interfaces and the trade-offs between different coupling levels.A crucial aspect of domain-driven design is the ability of different parts of the system to communicate and share information effectively.
This interaction often involves multiple bounded contexts, each focusing on a specific domain concern. This section examines how to facilitate this interaction, promoting clarity and maintainability while ensuring the overall system’s integrity.
Strategies for Interaction Between Contexts
The choice of interaction strategy depends on the specific needs of each context and the desired level of coupling. Several strategies exist, each with its own set of advantages and disadvantages. A crucial consideration is the level of coupling, ranging from loose coupling, allowing contexts to be independent, to tight coupling, which promotes greater interdependence.
- Shared Kernel: This strategy involves defining a shared domain model that is used by multiple bounded contexts. This approach promotes a consistent understanding of the domain across contexts, improving communication and data consistency. However, changes to the shared model require careful coordination across all contexts.
- Anti-Corruption Layer: This strategy involves creating an interface that allows contexts to interact without needing to understand the internal structure of each other. This approach isolates each context from changes in other contexts, minimizing disruption. The anti-corruption layer translates between the different domain languages and data formats.
- Message Queue: Using a message queue allows contexts to communicate asynchronously. One context publishes a message to the queue, and another context subscribes to receive it. This decoupling makes contexts more independent and resilient to failures in other parts of the system. It is particularly effective for events or notifications that don’t require immediate responses.
- API Gateway: An API gateway acts as a single entry point for all interactions with other contexts. It manages routing, security, and potentially other aspects of the communication. This approach is beneficial for complex systems with numerous contexts, enabling centralized control and management of interactions.
Examples of Interaction Patterns
Different patterns emerge from these strategies. These patterns demonstrate how different bounded contexts can interact, ensuring data consistency and reducing complexity.
- Order Processing: A Customer Service context might send a message to the Order Fulfillment context when a customer places an order. The Order Fulfillment context then processes the order, and sends a confirmation message back to the Customer Service context. This is a typical example of asynchronous interaction using a message queue.
- Inventory Management: When a product is sold, the Sales context can send a message to the Inventory context. The Inventory context updates its records to reflect the change in inventory levels. This is an example of how a message queue can manage updates to inventory levels across different parts of the system.
Importance of Clear Interfaces
Well-defined interfaces between contexts are crucial for maintainability and scalability. These interfaces serve as a contract, ensuring that contexts understand how to communicate and exchange data. This reduces the impact of changes in one context on other contexts.
Trade-offs Between Loose and Tight Coupling
Loose coupling promotes independence and reduces the impact of changes in one context on others. Tight coupling, however, can lead to greater efficiency and faster interactions, especially in systems with frequent interactions. Choosing the right level of coupling depends on the specific needs of the system and the expected frequency of changes.
Using APIs for Context Interactions
APIs are a common mechanism for interacting between contexts. They provide a standardized way to access data and functionality in other contexts, ensuring that the different components of the system can work together smoothly. REST APIs, in particular, are often used to define the interface between contexts.
Evolution & Adaptability
Bounded contexts, as integral parts of a domain model, are not static entities. They evolve in response to changing business needs and technological advancements. Understanding how to adapt these contexts is crucial for maintaining the system’s agility and relevance over time. Successful adaptation involves careful planning and consideration of the broader system architecture.
Strategies for Evolving Bounded Contexts
Evolving bounded contexts effectively requires a strategic approach. One key strategy is incremental change, introducing new features or functionality in small, manageable steps. This minimizes disruption and allows for thorough testing and validation at each stage. Another important strategy is to maintain clear communication channels between stakeholders and developers to ensure alignment on evolving requirements. A third strategy involves creating modular architectures within the bounded context, enabling independent development and deployment of components, which enhances the flexibility of the context.
Adapting to New Requirements
Bounded contexts can be adapted to accommodate new requirements by leveraging the principle of modularity. This approach allows for the addition of new features or functionalities without disrupting existing parts of the context. For example, if a new regulatory mandate requires the inclusion of enhanced reporting capabilities, the bounded context can be adapted by adding a new module specifically dedicated to reporting, without affecting the core functionality.
This modular approach ensures that the context remains stable while accommodating the change. Furthermore, refactoring existing code to improve maintainability and readability is crucial for ensuring long-term adaptability.
Methods for Enhancing Adaptability
Methods for increasing the adaptability of bounded contexts include using a ubiquitous language that is clearly defined and easily understood by all stakeholders. A shared vocabulary helps facilitate communication and collaboration, crucial for effectively adapting to changing requirements. Another method involves designing contexts with loose coupling between components. This allows for independent evolution of different parts of the context without affecting others.
Using well-defined interfaces also facilitates the addition of new functionality or the replacement of existing components without affecting the overall system architecture. Furthermore, adopting a test-driven development approach ensures that changes are thoroughly validated, which mitigates risks associated with adapting the bounded context.
Common Scenarios of Bounded Context Evolution
| Scenario | Description |
|---|---|
| New Business Feature | The business introduces a new product or service, requiring the addition of new functionality within the bounded context. |
| Regulatory Changes | Compliance with new regulations mandates changes to data handling, reporting, or other processes within the bounded context. |
| System Integration | Integrating with a new external system necessitates modifications to data exchange protocols and communication methods within the bounded context. |
| Technological Advancements | New technologies (e.g., cloud computing, AI) might necessitate changes to data storage, processing, or other core functionalities within the bounded context. |
| User Experience Enhancements | Improvements to user interface or user experience might necessitate modifications to the way data is presented or functionalities are accessed within the bounded context. |
Design Patterns
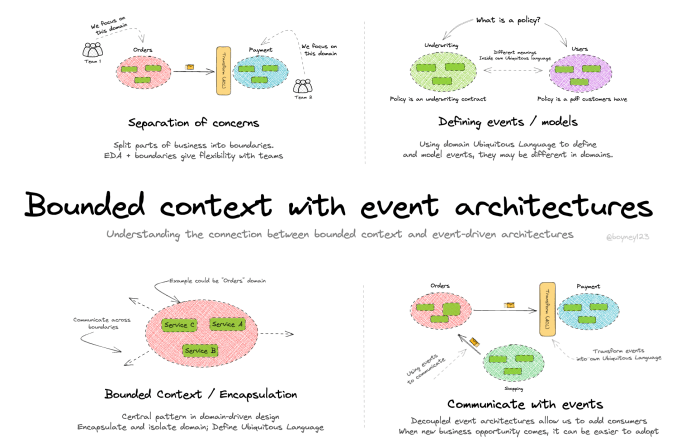
Domain-driven design (DDD) leverages design patterns to effectively structure software systems around bounded contexts. These patterns facilitate the creation of maintainable, scalable, and flexible applications that accurately reflect the business domain. Understanding and applying these patterns is crucial for translating the complex domain model into a robust software architecture.
Identifying Relevant Design Patterns
DDD’s design patterns are categorized by their focus on specific aspects of the system. They range from organizational patterns, such as bounded contexts, to patterns that define the interaction between contexts. These patterns promote consistency, communication, and a shared understanding within and across contexts. Understanding the specific challenges and opportunities of each bounded context will help identify the most appropriate design pattern.
Examples of Design Patterns in Action
- Strategic Contexts: Employing the “Onion Architecture” pattern can structure the system’s components around the core domain logic, enabling modularity and separation of concerns. This approach helps to encapsulate business rules and logic, allowing for independent evolution of specific contexts within the overall system. The core domain model resides at the center of the system, surrounded by layers for application services, infrastructure, and user interfaces.
- Tactical Contexts: The “Hexagonal Architecture” pattern is useful when dealing with multiple external systems and data sources. By encapsulating the external dependencies within a layer, the core domain logic becomes independent of specific technologies. This approach facilitates easy adaptation to different data sources or external services without affecting the core domain logic.
- Interaction Patterns: The “CQRS (Command Query Responsibility Segregation)” pattern is highly beneficial for contexts where read and write operations have different needs. In this pattern, the application distinguishes between commands (for updates) and queries (for retrieving data). This enables better scalability, performance, and maintainability, especially when dealing with high-volume read operations.
Best Practices for Applying Design Patterns
Careful consideration of the context’s specific requirements is paramount. A pattern’s effectiveness depends heavily on its suitability for the specific problem it’s intended to solve. Avoid blindly applying a pattern; instead, assess its applicability and adapt it to the particular nuances of the bounded context. Furthermore, maintain consistency in the application of the pattern throughout the entire system to avoid introducing inconsistencies.
Thorough documentation of the rationale behind the chosen patterns is crucial for future maintenance and understanding.
Table of Design Pattern Benefits and Drawbacks
| Design Pattern | Benefits | Drawbacks |
|---|---|---|
| Onion Architecture | Improved modularity, testability, maintainability, and separation of concerns. | Potentially more complex setup, overhead in handling cross-cutting concerns. |
| Hexagonal Architecture | Loose coupling, independent evolution of external dependencies, improved testability. | Potentially more complex implementation, requires careful planning. |
| CQRS | Enhanced scalability, improved performance, better maintainability, clear separation of concerns. | Increased complexity, potential for duplicated data. |
Implementation Considerations
Implementing bounded contexts effectively requires careful consideration of various practical aspects. This involves more than just conceptualizing the boundaries; it demands a practical approach to ensure smooth integration and maintainability within a larger system. The choice of technologies, data management strategies, and communication protocols all play a crucial role in the successful realization of a bounded context.The process of implementing bounded contexts isn’t a one-size-fits-all endeavor.
Challenges often arise, particularly when dealing with complex systems or integrating with existing infrastructure. Addressing these challenges head-on through well-defined strategies and adherence to best practices is key to achieving a robust and maintainable solution. This section delves into these considerations, providing a framework for successful implementation.
Practical Considerations for Implementation
Effective implementation requires careful planning and execution. Key considerations include the choice of technologies aligned with the specific needs of the bounded context, efficient data management strategies, and robust communication protocols for interactions with other contexts. This often involves careful trade-offs between different architectural patterns and their potential impacts on the project’s timeline and budget.
Implementation Challenges
Several challenges can arise during bounded context implementation. One significant challenge is integrating the bounded context with existing systems or legacy infrastructure. Another hurdle is maintaining a consistent ubiquitous language across teams working on different contexts. Ensuring seamless data exchange and avoiding data silos is crucial. The evolving nature of requirements and the need to adapt to changing business needs further complicates implementation.
Strategies for Mitigating Challenges
Addressing the challenges of bounded context implementation requires proactive strategies. One strategy is to use a well-defined migration plan for integrating with existing systems, ensuring minimal disruption to ongoing operations. Utilizing appropriate communication channels and protocols, like APIs, facilitates efficient data exchange between bounded contexts. Employing a standardized data format for all inter-context communication ensures consistency. Regular code reviews and communication between teams can help maintain a consistent ubiquitous language.
Best Practices for Implementation
Adhering to best practices is critical for successful bounded context implementation. This includes defining clear ownership and responsibility for each bounded context. Establishing well-defined communication protocols between contexts is essential. Implementing robust data validation and error handling mechanisms can prevent issues. Regularly evaluating and refining the boundaries of the context ensures alignment with evolving business needs.
Process for Building a Bounded Context
A structured process is crucial for building a bounded context in a real-world scenario. The process involves identifying the key business domain concerns and defining their boundaries. It further involves establishing a clear ubiquitous language to ensure consistent communication among team members. Developing detailed data models and appropriate interaction protocols with other contexts are crucial steps. Finally, the process should include a thorough testing phase and iterative refinement to ensure alignment with business needs.
Example: Implementing a Sales Bounded Context
Consider implementing a sales bounded context within an e-commerce platform. The bounded context might interact with inventory, customer, and payment contexts. Implementing an API for data exchange between contexts is a crucial step. Ensuring data consistency and integrity across these interactions is essential. Regular communication between teams working on different bounded contexts is crucial to prevent inconsistencies.
The implementation should be adaptable to future changes in the e-commerce platform’s requirements.
Example Scenario: An E-commerce Platform
E-commerce platforms are complex systems, handling various interactions and processes. This example illustrates a bounded context focused on the order fulfillment process within a hypothetical online retailer. This bounded context is isolated from other concerns like product catalog management or customer relationship management.
Context Description
This bounded context encapsulates the complete order fulfillment process, from order placement to delivery confirmation. Stakeholders include order processors, warehouse staff, shipping providers, and the customer. The goal is to ensure orders are accurately processed, shipped promptly, and delivered efficiently.
Stakeholders
The core stakeholders involved in this bounded context include:
- Order Processors: These individuals or systems receive orders, verify them, and initiate the fulfillment process.
- Warehouse Staff: Responsible for picking, packing, and preparing orders for shipment.
- Shipping Providers: External entities handling the actual transportation of orders.
- Customers: The end recipients of the orders, interacting with the system to track and manage their orders.
Interaction Patterns
The interaction patterns within this bounded context are crucial for smooth order fulfillment. These patterns define how stakeholders communicate and exchange information:
- Order Placement: Customers place orders through the platform’s user interface.
- Order Processing: Order processors receive orders, verify details, and update order status.
- Inventory Management: Warehouse staff check inventory availability and allocate items to orders.
- Shipping: Shipping providers receive shipping instructions and handle order delivery.
- Tracking: Customers receive updates on their order’s status and location throughout the process.
Context Map
The context map for this bounded context visually represents its interactions with other contexts. The order fulfillment context interacts with the product catalog and customer relationship management contexts. A text-based context map follows:Order Fulfillment Context
interacts with
Product Catalog Context
Customer Relationship Management Context
Entities and Relationships
The following table Artikels the key entities and their relationships within the order fulfillment bounded context:
| Entity | Description | Relationships |
|---|---|---|
| Order | Represents a customer purchase request. | Associated with Customer, Product, ShippingAddress, OrderStatus |
| Product | Represents a product offered for sale. | Associated with Order (many-to-many through OrderItems), Inventory |
| Inventory | Stores product quantities. | Associated with Product, WarehouseLocation |
| WarehouseLocation | Stores products in the warehouse. | Associated with Inventory, Order |
| Customer | Represents a customer placing an order. | Associated with Order, ShippingAddress |
| ShippingAddress | Details for shipping the order. | Associated with Order, Customer |
| OrderStatus | Tracks the current stage of the order. | Associated with Order |
Conclusion

In conclusion, bounded contexts are essential for effectively managing complexity in software development. By defining clear boundaries and establishing consistent communication, developers can build robust, adaptable, and maintainable systems. Understanding the intricacies of bounded contexts is paramount to achieving successful domain-driven design. The focus on specific business domains and consistent communication enables better alignment with business requirements, ensuring a more efficient and effective software development process.
Popular Questions
What are some common pitfalls in defining bounded contexts?
Defining overly broad or narrow bounded contexts can lead to difficulties in communication and maintenance. Carefully consider the scope of each context, ensuring it aligns with specific business capabilities and avoids overlapping responsibilities.
How do bounded contexts facilitate better communication among teams?
Bounded contexts provide a framework for clear communication by establishing well-defined boundaries. This allows teams to focus on specific business concerns and minimize ambiguity in interactions, promoting better collaboration.
What are the trade-offs between loose and tight coupling of bounded contexts?
Loose coupling allows for greater flexibility and independent evolution of bounded contexts but might require more complex communication mechanisms. Tight coupling simplifies communication but can limit the independence of contexts. The optimal approach depends on the specific needs and complexities of the system.
How does a ubiquitous language support the concept of a bounded context?
A ubiquitous language fosters a shared understanding of terminology and concepts within a bounded context. This shared vocabulary minimizes misunderstandings and facilitates seamless communication among team members working within that context.


