Application portfolio analysis for migration is a critical process, often underestimated, yet fundamentally crucial for organizations undergoing digital transformation. It provides a structured, data-driven approach to understanding an organization’s application landscape, making informed decisions about which applications to migrate, modernize, or retire. This preliminary assessment lays the groundwork for a successful migration strategy, minimizing risks and maximizing the return on investment.
This process involves a comprehensive evaluation of existing applications, examining their functionality, dependencies, technical architecture, and business value. The ultimate goal is to align the IT portfolio with the organization’s strategic objectives, optimizing resource allocation and ensuring that migration efforts support business growth. This structured approach allows for a clear understanding of the complexities involved, enabling efficient resource allocation and risk mitigation.
Defining Application Portfolio Assessment for Migration
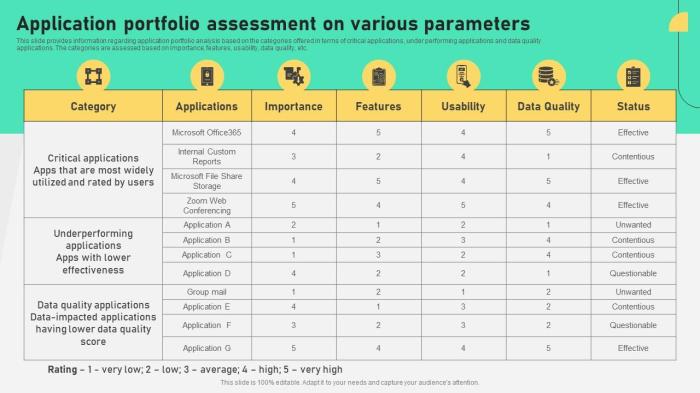
Application Portfolio Assessment (APA) for migration is a critical preliminary step in any organizational effort to move its software applications to a new environment, such as the cloud, a different infrastructure, or a modernized platform. This process systematically evaluates an organization’s application landscape to understand its composition, dependencies, and suitability for migration. It provides a data-driven foundation for making informed decisions, mitigating risks, and optimizing the migration process.
Core Purpose of Application Portfolio Assessment in Migration
The fundamental purpose of an application portfolio assessment in the context of migration is to determine the most effective and efficient strategy for moving an organization’s applications. This involves understanding the current state of each application, identifying its critical dependencies, assessing its technical and business value, and evaluating its readiness for migration. The assessment ultimately aims to minimize disruption, reduce costs, and maximize the benefits of the migration effort.
Concise Definition of the Process
Application Portfolio Assessment for migration is a structured process of evaluating an organization’s software applications to understand their characteristics, dependencies, and migration readiness. It involves collecting data on each application, analyzing its functionality, technical architecture, business value, and operational costs. The assessment culminates in a set of recommendations that inform the migration strategy, including prioritization, target platform selection, and migration approach.
The process is typically conducted before any actual migration work begins, allowing for a proactive and informed approach.
Key Benefits of Performing This Assessment Before Migration Efforts
Performing an application portfolio assessment prior to migration offers numerous benefits, significantly increasing the likelihood of a successful and cost-effective migration. These benefits are realized through informed decision-making, risk mitigation, and optimized resource allocation.
- Informed Decision-Making: The assessment provides a comprehensive understanding of the application landscape, enabling organizations to make data-driven decisions about which applications to migrate, when to migrate them, and how to migrate them. For example, by assessing the interdependencies between applications, the assessment helps determine the optimal migration order to minimize disruption.
- Risk Mitigation: By identifying potential risks and challenges early in the process, such as compatibility issues, security vulnerabilities, and regulatory compliance concerns, the assessment allows organizations to proactively address these issues. This reduces the likelihood of costly rework and project delays. A common risk identified is the “shadow IT” phenomenon, where unauthorized applications may be running. The assessment helps uncover and manage these instances.
- Cost Optimization: The assessment helps identify opportunities to optimize migration costs by evaluating application complexity, infrastructure requirements, and potential for modernization. This can lead to significant cost savings by avoiding unnecessary migrations, choosing the most cost-effective migration strategies, and identifying opportunities to retire or replace applications. Consider a scenario where an application is found to have very low business value and high maintenance costs; the assessment could recommend its retirement rather than migration.
- Prioritization and Sequencing: The assessment provides a framework for prioritizing applications for migration based on their business value, technical complexity, and dependencies. This allows organizations to sequence the migration efforts in a way that maximizes business benefits and minimizes disruption. For example, applications that are critical to revenue generation might be prioritized over those that are less essential.
- Improved Migration Planning: The assessment provides valuable insights for developing a detailed migration plan, including the selection of appropriate migration tools and methodologies. It helps define the scope of the migration project, estimate resource requirements, and establish a realistic timeline. This leads to better project management and reduces the likelihood of scope creep.
- Enhanced Business Alignment: The assessment ensures that the migration efforts are aligned with the organization’s overall business strategy. By considering the business value of each application, the assessment helps prioritize migrations that support the organization’s strategic goals. For instance, if a company is focusing on expanding its e-commerce capabilities, the assessment would prioritize the migration of related applications.
Objectives of the Assessment
Application portfolio assessment for migration serves multiple critical objectives, fundamentally guiding organizations towards more efficient, cost-effective, and strategically aligned IT landscapes. These objectives are not isolated; they are interwoven and contribute to a holistic transformation process, ensuring that the migration journey is well-planned, executed, and delivers tangible business value.
Identifying Primary Business Goals
A core objective is to pinpoint the specific business goals the organization aims to achieve through application portfolio evaluation. This involves a deep understanding of the current state and desired future state of the IT environment, translating business objectives into actionable IT strategies.
- Cost Reduction: The assessment identifies opportunities to consolidate applications, retire redundant systems, and optimize infrastructure, leading to significant cost savings. For instance, a large retail company, after an application portfolio assessment, discovered several overlapping CRM systems. By consolidating these, they reduced annual operational costs by 15% and licensing fees by 20%.
- Enhanced Agility and Innovation: By streamlining the application landscape, organizations can become more responsive to market changes and embrace new technologies more quickly. This includes identifying applications that hinder innovation and proposing modern alternatives. A financial services firm, for example, used an assessment to identify legacy systems preventing them from adopting cloud-based solutions. Migrating these systems enabled them to launch new products 30% faster.
- Improved Operational Efficiency: The assessment helps to identify areas where processes can be automated and optimized, leading to improved efficiency and reduced operational overhead. A manufacturing company, through assessment, identified a need to integrate its supply chain management systems. Integrating these systems reduced order fulfillment time by 25%.
- Increased Business Value: The ultimate goal is to align IT investments with business priorities, ensuring that the application portfolio supports strategic initiatives and delivers measurable business value. This involves evaluating how well each application contributes to revenue generation, customer satisfaction, and market competitiveness.
Aligning IT with Business Strategy
Application portfolio assessment plays a pivotal role in ensuring that IT initiatives, particularly migration projects, are closely aligned with the overarching business strategy. This alignment is critical for maximizing the return on investment (ROI) and ensuring that IT investments support business growth and objectives.
- Strategic Roadmap Development: The assessment provides the data and insights necessary to develop a strategic roadmap for the application portfolio, ensuring that IT investments support the business’s long-term goals. This roadmap includes prioritized migration projects, technology selections, and resource allocation strategies.
- Prioritization of Migration Projects: The assessment helps to prioritize migration projects based on their strategic importance, business value, and technical feasibility. This ensures that resources are allocated to the most impactful projects first.
- Technology Selection and Standardization: The assessment informs technology selection decisions, ensuring that chosen technologies are aligned with business needs and can support future growth. This may involve standardizing on specific platforms or cloud services to reduce complexity and improve manageability.
- Stakeholder Alignment: The assessment process facilitates collaboration and alignment among IT and business stakeholders, ensuring that everyone understands the goals and objectives of the migration project. This includes regular communication and feedback sessions to ensure that the project remains on track.
Risk Mitigation for Migration Projects
A comprehensive application portfolio assessment is a crucial step in mitigating the risks associated with migration projects. By identifying potential issues early on, organizations can proactively address them, minimizing disruptions and ensuring a smoother transition.
- Technical Risk Assessment: The assessment identifies potential technical challenges, such as compatibility issues, data migration complexities, and performance bottlenecks. This allows organizations to develop mitigation strategies, such as pilot projects or phased migrations.
- Financial Risk Assessment: The assessment provides a realistic estimate of the costs associated with the migration project, including hardware, software, labor, and training. This helps organizations to budget effectively and avoid cost overruns.
- Operational Risk Assessment: The assessment identifies potential disruptions to business operations during the migration process, such as downtime, data loss, and security vulnerabilities. Mitigation strategies include detailed contingency plans and robust testing procedures.
- Compliance and Security Risk Assessment: The assessment ensures that the migration project complies with all relevant regulations and security standards. This includes data privacy, data governance, and cybersecurity requirements. For example, a healthcare provider migrating patient data must ensure compliance with HIPAA regulations.
Steps Involved in the Process
Conducting an application portfolio assessment for migration is a structured process. This process requires a methodical approach to ensure a comprehensive evaluation of the existing application landscape, ultimately informing a successful migration strategy. The steps involved are designed to provide a clear roadmap for organizations embarking on this endeavor.
Step-by-Step Procedure
The following steps Artikel the key activities involved in performing an application portfolio assessment. Each step builds upon the previous one, contributing to a holistic understanding of the application landscape and its suitability for migration. The steps are presented in a logical sequence to facilitate ease of understanding and execution.
- Define Scope and Objectives: Before commencing the assessment, it is crucial to clearly define the scope of the assessment. This includes identifying which applications are to be evaluated, the specific objectives of the migration (e.g., cost reduction, improved performance, enhanced security), and the target environment (e.g., cloud, on-premises).
- Data Collection and Inventory: This step involves gathering comprehensive data about each application within the defined scope. Data collection methods include reviewing documentation, interviewing stakeholders (business users, IT staff), and utilizing automated discovery tools. The collected data should encompass application characteristics, dependencies, technical architecture, business criticality, and usage patterns.
- Application Profiling and Analysis: The gathered data is then used to create detailed profiles for each application. These profiles should include information on application functionality, technology stack, integration points, performance metrics, and security vulnerabilities. This analysis phase identifies interdependencies between applications, which can impact migration strategies.
- Business Value Assessment: Each application’s contribution to the business must be evaluated. This assessment considers factors such as the application’s alignment with business goals, its impact on revenue generation, and its criticality to core business processes. This analysis helps prioritize applications for migration based on their business value.
- Technical Suitability Assessment: The technical feasibility of migrating each application is assessed. This includes evaluating the application’s compatibility with the target environment, identifying any required code modifications or refactoring, and assessing the availability of equivalent services in the target environment.
- Risk and Cost Analysis: Potential risks associated with migrating each application, such as downtime, data loss, and security breaches, must be identified and evaluated. Additionally, the costs associated with each migration option (e.g., rehosting, re-platforming, refactoring) are estimated, encompassing both direct costs (e.g., infrastructure, licenses) and indirect costs (e.g., training, migration efforts).
- Migration Strategy Development: Based on the analysis of business value, technical suitability, and risk/cost, a migration strategy is developed for each application. This strategy Artikels the chosen migration approach (e.g., rehost, re-platform, refactor, retire, retain), the migration sequence, and the required resources.
- Prioritization and Planning: Applications are prioritized for migration based on their business value, technical feasibility, and risk profile. A detailed migration plan is created, including timelines, resource allocation, and risk mitigation strategies. This plan ensures a structured and controlled migration process.
- Documentation and Reporting: Throughout the assessment process, all findings, analyses, and recommendations are documented. A comprehensive report is generated, summarizing the assessment results, outlining the proposed migration strategy, and providing recommendations for the migration execution.
Data Gathering and Analysis Techniques
The success of application portfolio migration hinges on the meticulous collection and analysis of data. This process involves understanding the intricacies of each application, from its technical specifications to its business value and dependencies. Rigorous data gathering and analysis provide the foundation for informed decision-making, ensuring a smooth and efficient migration process. This section details the methods employed for data collection and the analytical techniques used to assess application suitability for migration.
Methods for Gathering Application Data
Effective data gathering requires a multi-faceted approach to capture the necessary information about each application. These methods should be tailored to the specific context of the organization and the applications under consideration.
- Application Discovery and Inventory: This initial step involves identifying and cataloging all applications within the portfolio. Tools such as automated discovery software, manual surveys, and documentation review can be used. This process should include identifying the application’s name, purpose, and basic technical details.
- Technical Assessment: A detailed examination of the application’s technical aspects is crucial. This involves analyzing the application’s architecture, code base, programming languages, frameworks, and underlying infrastructure. Tools like static code analysis tools and dependency scanners are helpful. The technical assessment also includes identifying the application’s dependencies on other applications, services, and infrastructure components.
- Business Value Assessment: Understanding the business value of each application is essential for prioritizing migration efforts. This involves evaluating the application’s contribution to revenue, operational efficiency, and strategic goals. Metrics such as user base, transaction volume, and criticality to business processes should be considered.
- Dependency Mapping: Identifying and mapping the dependencies between applications and infrastructure components is a critical part of the assessment. This involves understanding how applications interact with each other, databases, middleware, and other services. This process ensures that dependencies are addressed during the migration process.
- Cost Analysis: Assessing the current and projected costs associated with each application, including maintenance, licensing, and infrastructure costs, is crucial. This information is vital for determining the cost-effectiveness of migrating an application to a new environment.
Analysis Techniques for Migration Readiness
Once the data is gathered, various analysis techniques are applied to evaluate applications for migration readiness. These techniques help determine the best migration strategy and identify potential challenges.
- Application Rationalization: This process involves evaluating the application portfolio to identify redundant, obsolete, or underutilized applications. Rationalization can reduce the scope of the migration effort and optimize the IT landscape.
- Dependency Analysis: Analyzing application dependencies to understand the impact of migrating one application on others. This analysis helps in determining the order of migration and mitigating potential risks. The use of dependency mapping tools and techniques is crucial for this analysis.
- Migration Strategy Selection: Based on the assessment, the most appropriate migration strategy for each application is selected. This could include rehosting (lift and shift), re-platforming, refactoring, re-architecting, or replacing.
- Risk Assessment: Identifying and assessing the risks associated with each migration strategy. This includes evaluating technical, business, and financial risks. Mitigation plans should be developed to address the identified risks.
- Cost-Benefit Analysis: Comparing the costs and benefits of migrating each application to determine the return on investment (ROI). This analysis helps prioritize migration efforts and justify the investment.
Comparison of Data Collection Methods
The following table compares different data collection methods based on their scope, effort, and the type of data they yield. This provides a quick reference for choosing the appropriate data collection methods for a given application portfolio.
| Data Collection Method | Scope | Effort | Data Collected | Example Tools |
|---|---|---|---|---|
| Automated Discovery | Entire Portfolio | Low to Medium | Application Inventory, Basic Technical Details | Network scanners, application discovery tools |
| Manual Surveys | Specific Applications | Medium to High | Application Details, Business Value, Dependencies | Spreadsheets, questionnaires, interviews |
| Code Analysis | Individual Applications | Medium to High | Code Quality, Dependencies, Architecture | Static code analysis tools, dependency scanners |
| Documentation Review | Specific Applications | Low to Medium | Technical Specifications, Architecture, Dependencies | Application documentation, architecture diagrams |
Key Considerations for Migration
Successful application migration hinges on a comprehensive understanding of various factors that influence the process. This section delves into the critical aspects that must be carefully evaluated to ensure a smooth, efficient, and secure migration strategy. Failure to address these considerations can lead to significant delays, cost overruns, and operational disruptions.
Application Dependencies and Their Impact on Migration Planning
Application dependencies represent the relationships between different software components, systems, and external services. Understanding these dependencies is crucial for accurate migration planning, as they directly impact the order, complexity, and potential risks associated with the process. Identifying these dependencies early in the assessment phase is essential for a successful migration strategy.
- Inter-Application Dependencies: Applications frequently rely on other applications for data exchange, processing, or functionality. For example, a customer relationship management (CRM) system might depend on a financial accounting system for billing information. Migrating the CRM system without considering the accounting system’s availability and compatibility could disrupt critical business processes. Thorough dependency mapping, often achieved through code analysis and documentation review, is essential to identify these connections.
- Infrastructure Dependencies: Applications rely on the underlying infrastructure, including servers, databases, and network components. Migrating to a new infrastructure (e.g., cloud-based services) requires careful consideration of these dependencies. For example, migrating a database-driven application to the cloud necessitates assessing database compatibility, network latency, and data transfer requirements.
- Data Dependencies: Data migration is often the most complex and time-consuming aspect of application migration. Applications depend on the data they store and use. Understanding the data structure, volume, and quality is critical for successful data migration. This includes identifying data formats, ensuring data integrity during the transfer, and minimizing downtime. For instance, migrating a large data warehouse might involve complex ETL (Extract, Transform, Load) processes to ensure data consistency and accuracy.
- External Service Dependencies: Applications frequently integrate with external services, such as payment gateways, APIs, and third-party libraries. These dependencies must be carefully considered during migration. For example, migrating an e-commerce platform that uses a specific payment gateway requires ensuring compatibility with the new environment and minimizing disruption to online transactions.
Compliance and Security in the Assessment
Compliance and security are paramount concerns during application migration. Migrating applications without addressing these aspects can expose the organization to significant risks, including data breaches, regulatory violations, and reputational damage. The assessment must include a thorough review of compliance requirements and security vulnerabilities.
- Regulatory Compliance: Organizations must adhere to various regulations, such as GDPR, HIPAA, and PCI DSS, depending on their industry and the type of data they handle. The assessment must identify all applicable regulations and assess the application’s compliance with those regulations in the new environment. This includes evaluating data residency requirements, data encryption, and access controls. For example, a healthcare application must comply with HIPAA regulations, including ensuring the secure storage and transmission of protected health information (PHI).
- Security Vulnerability Assessment: Identifying and mitigating security vulnerabilities is critical to protecting applications and data from cyberattacks. The assessment should include a thorough security review of the application code, infrastructure, and data. This may involve vulnerability scanning, penetration testing, and code reviews. For example, an application with known vulnerabilities, such as SQL injection or cross-site scripting (XSS), must be remediated before migration.
- Data Protection: Protecting sensitive data is a key security consideration. The assessment must evaluate data encryption, access controls, and data loss prevention (DLP) measures. This includes ensuring that data is encrypted both in transit and at rest, implementing strong access controls to limit who can access sensitive data, and implementing DLP measures to prevent data leakage. For example, credit card information should be encrypted and stored securely, and access to this information should be restricted to authorized personnel.
- Identity and Access Management (IAM): IAM is critical for controlling access to applications and data. The assessment should evaluate the application’s IAM capabilities and ensure that they are compatible with the new environment. This includes evaluating authentication methods, authorization policies, and user provisioning processes. For example, migrating an application to the cloud might involve integrating it with a cloud-based IAM solution to manage user identities and access.
Evaluation Criteria and Scoring
The evaluation of an application portfolio for migration suitability necessitates a structured and objective scoring system. This system provides a quantifiable method to assess each application based on predefined criteria, facilitating informed decision-making and prioritization. The scoring process helps to avoid subjective biases and ensures that migration efforts are focused on applications that will yield the greatest benefits and have the highest likelihood of success.
Designing a Scoring System for Migration Suitability
A robust scoring system is built upon a set of weighted criteria that reflect the key factors influencing migration feasibility and desirability. These criteria should be clearly defined, measurable, and relevant to the organization’s strategic goals. Each criterion is assigned a weight reflecting its relative importance, and each application is scored against these criteria. The final score for an application is calculated by multiplying its score for each criterion by the criterion’s weight and summing the results.
This weighted scoring approach allows for a nuanced evaluation, reflecting the differing impacts of various factors.
- Defining the Criteria: The first step is to identify the critical factors that determine an application’s suitability for migration. These factors can be broadly categorized into:
- Business Value: Assessing the application’s contribution to business operations, revenue generation, and strategic objectives.
- Technical Complexity: Evaluating the application’s architecture, dependencies, and compatibility with the target environment.
- Migration Effort: Estimating the resources, time, and cost required to migrate the application.
- Risk Assessment: Identifying potential risks associated with the migration, such as data loss, downtime, or security vulnerabilities.
- Weighting the Criteria: Assigning weights to each criterion based on its relative importance. For example, business value might be weighted more heavily than technical complexity if the primary goal of the migration is to improve business agility. Weights should sum to 100%.
- Defining Scoring Scales: Establishing a consistent scoring scale for each criterion. A common approach is to use a scale of 1 to 5 or 1 to 10, where a higher score indicates greater suitability or lower risk. The scoring scale should be clearly defined with specific descriptions for each score level.
- Scoring the Applications: Evaluating each application against each criterion and assigning a score based on the defined scoring scale. This process often involves input from various stakeholders, including business users, IT staff, and security experts.
- Calculating the Total Score: Multiplying the score for each criterion by its weight and summing the results to obtain a total score for each application. This total score provides a quantitative measure of the application’s migration suitability.
Demonstrating the Use of a Scoring Matrix for Prioritization
A scoring matrix is a powerful tool for visualizing and prioritizing applications based on their migration suitability scores. The matrix typically presents applications in a grid, with the migration suitability score as one dimension and other relevant factors, such as business criticality or cost of migration, as other dimensions. This visualization allows for a quick identification of high-priority applications that are both suitable for migration and align with the organization’s strategic objectives.
The matrix facilitates a data-driven approach to decision-making, enabling the IT team to prioritize migration efforts effectively.
- Creating the Matrix: The scoring matrix can be created using a spreadsheet or dedicated application portfolio management software. The matrix should include columns for application name, total score, business value, technical complexity, migration effort, risk assessment, and any other relevant factors.
- Populating the Matrix: Entering the scores for each application based on the scoring system. The total score is calculated automatically based on the weighted scores for each criterion.
- Analyzing the Results: Reviewing the matrix to identify applications with the highest total scores. These applications are typically the highest priority for migration. Consider also the other dimensions to refine prioritization.
- Prioritizing Applications: Using the matrix to rank applications based on their total scores and other relevant factors. Applications with high scores, low migration effort, and high business value should be prioritized for migration.
- Creating a Migration Roadmap: Developing a migration roadmap that Artikels the order in which applications will be migrated, based on the prioritization results. The roadmap should also include timelines, resource allocation, and risk mitigation strategies.
Example Scoring Matrix Using an HTML Table
The following table demonstrates an example of a scoring matrix. This 4-column table illustrates the scoring criteria for three example applications: “Customer Relationship Management (CRM)”, “Legacy Order Processing”, and “New Analytics Platform”. Each application is scored across four key criteria, and the final score is calculated based on the weights assigned to each criterion. The scoring is on a scale of 1 to 5, where 1 is the lowest and 5 is the highest.
This simplified example demonstrates the basic structure and functionality of a scoring matrix.
| Application | Business Value (30%) | Technical Complexity (25%) | Migration Effort (25%) | Risk Assessment (20%) | Total Score |
|---|---|---|---|---|---|
| Customer Relationship Management (CRM) | 5 (15) | 3 (7.5) | 4 (10) | 4 (8) | 40.5 |
| Legacy Order Processing | 3 (9) | 5 (12.5) | 5 (12.5) | 2 (4) | 38 |
| New Analytics Platform | 4 (12) | 4 (10) | 3 (7.5) | 3 (6) | 35.5 |
The table provides a snapshot of the application portfolio, with scores in parentheses representing the weighted score for each criterion. For instance, the CRM system, scoring a 5 for business value (multiplied by the 30% weight resulting in 15), is shown to be the highest in business value. The total score for each application is derived by summing the weighted scores for each criterion, resulting in the total score for the application.
This helps in comparing applications based on their migration suitability, enabling the organization to prioritize effectively.
Technology Stack and Compatibility
The technology stack assessment is a critical component of application portfolio analysis for migration, focusing on understanding the underlying technologies that support each application and their suitability for the target environment. This evaluation directly impacts migration feasibility, effort estimation, and potential risks. It necessitates a thorough examination of programming languages, frameworks, databases, operating systems, and associated middleware.
Technology Stack Assessment Process
The assessment of an application’s technology stack involves a systematic examination of its constituent components to determine its migration readiness. This analysis aims to identify potential compatibility issues, dependencies, and complexities that could hinder the migration process. This involves cataloging all the technologies used and analyzing their interdependencies.
- Identification of Technologies: The initial step involves identifying all the technologies used by the application. This includes programming languages, frameworks, databases, operating systems, web servers, application servers, and any third-party libraries or services.
- Version Analysis: Determining the specific versions of each technology is crucial. Older versions may have compatibility issues with the target environment or may no longer be supported, necessitating upgrades or replacements.
- Dependency Mapping: Understanding the dependencies between different components of the technology stack is vital. This includes identifying which components rely on others and the impact of changes to a single component on the overall application.
- Skills Gap Analysis: Assess the availability of in-house skills for the target technology stack. If there is a significant skills gap, it could increase migration costs and timelines.
- Licensing Considerations: Analyze the licensing implications of the current technology stack. This includes understanding the licensing costs associated with the target environment and any potential compliance issues.
Evaluating Application Compatibility
Evaluating application compatibility with the target environment is a key aspect of the technology stack assessment. This process determines the feasibility of migrating the application and identifies potential challenges that need to be addressed. It involves comparing the current technology stack with the capabilities and limitations of the target environment.
- Operating System Compatibility: Applications need to be compatible with the operating system of the target environment. This involves assessing whether the application is designed to run on the target OS and identifying any required modifications. For example, an application running on Windows Server 2008 may need to be re-architected to run on a Linux-based cloud environment.
- Database Compatibility: Evaluate the compatibility of the application’s database with the target database system. This includes assessing data migration requirements, schema changes, and performance considerations. For instance, migrating from an on-premises Oracle database to a cloud-based PostgreSQL database might require significant data transformation efforts.
- Middleware and Framework Compatibility: Middleware and frameworks are crucial components of many applications. Assess the compatibility of these components with the target environment, including support for the same versions or equivalent alternatives.
- API and Integration Compatibility: Applications often rely on APIs and integrations with other systems. Verify that these integrations are compatible with the target environment, including the availability of necessary connectors and the ability to maintain data integrity.
- Performance and Scalability Assessment: Evaluate whether the application can meet performance and scalability requirements in the target environment. This includes considering factors such as network latency, server resources, and the ability to handle increased user loads.
Technology Stack Considerations Examples
Several technology stack elements require specific consideration during the assessment. Each component’s compatibility and suitability for the target environment must be carefully evaluated.
- Programming Languages: Consider the compatibility of programming languages used, such as Java, .NET, Python, and PHP. For example, an application written in .NET Framework may require significant refactoring to run on .NET Core or .NET.
- Databases: Assess database compatibility, including Oracle, SQL Server, MySQL, and PostgreSQL. For instance, migrating from a legacy Oracle database to a cloud-based database service might involve data migration and schema conversion.
- Web Servers: Evaluate web server compatibility, including Apache, Nginx, and IIS. Ensure that the target environment supports the web server used or that a suitable alternative is available.
- Application Servers: Analyze application server compatibility, such as Tomcat, WebLogic, and JBoss. For example, migrating an application running on WebLogic to a containerized environment might involve re-architecting the application to utilize a more lightweight application server like Tomcat.
- Frameworks and Libraries: Consider the compatibility of frameworks and libraries, such as Spring, React, Angular, and jQuery. Verify that the target environment supports these frameworks and that the application’s dependencies are compatible.
- Operating Systems: Assess operating system compatibility, including Windows Server, Linux, and macOS. Ensure that the application is designed to run on the target OS and that all necessary drivers and libraries are available.
- Middleware: Evaluate middleware compatibility, including message queues, caching systems, and service buses. Verify that the target environment supports the middleware used or that a suitable alternative is available.
Decision Making and Prioritization

The culmination of application portfolio assessment, encompassing data gathering, analysis, and evaluation, is informed decision-making regarding application migration. This process moves beyond mere identification of applications to a structured framework for prioritizing migration efforts, ensuring alignment with business objectives and optimizing resource allocation. The findings serve as a critical input for strategic planning, risk mitigation, and the ultimate success of the migration initiative.
Informing Migration Decisions
The assessment findings provide a comprehensive understanding of each application’s characteristics, dependencies, and suitability for migration. This understanding informs the decisions made about the
- what*,
- when*, and
- how* of migration.
- Application Suitability: The assessment reveals whether an application is a suitable candidate for migration. Factors such as technical debt, vendor support, and architectural compatibility are evaluated to determine if migrating the application is feasible and beneficial. Applications deemed unsuitable may be retired, modernized, or re-platformed.
- Migration Strategy: The assessment helps to define the most appropriate migration strategy for each application. This includes choices such as rehosting (lift-and-shift), re-platforming, refactoring, or replacing the application. The optimal strategy is selected based on factors like complexity, cost, and business requirements.
- Migration Sequence: The assessment aids in determining the order in which applications should be migrated. Prioritization is crucial for managing risks, minimizing disruption, and achieving early wins.
- Resource Allocation: The assessment results provide insights into the resources required for migration, including budget, personnel, and infrastructure. This information facilitates effective resource allocation and ensures the migration project is adequately supported.
- Risk Mitigation: The assessment identifies potential risks associated with each application’s migration, such as data loss, downtime, and security vulnerabilities. This allows for the development of mitigation strategies to minimize the impact of these risks.
Prioritizing Applications for Migration
Prioritization is a critical step in application portfolio migration. It is essential to define a structured approach to rank applications based on the assessment results and business objectives. A well-defined prioritization framework ensures that the most critical applications are migrated first, maximizing the return on investment and minimizing risks.
- Business Value: Applications that provide significant business value, such as revenue generation, customer engagement, or core operational functions, should be prioritized. This can be determined by assessing factors like the application’s impact on key performance indicators (KPIs), its role in supporting business processes, and its strategic importance.
- Technical Complexity: Applications with lower technical complexity and fewer dependencies are generally easier and faster to migrate. This reduces the risk of delays and complications. Conversely, applications with high technical complexity may require more in-depth planning and phased migration approaches.
- Risk Assessment: Applications with a high risk profile, such as those with security vulnerabilities, high maintenance costs, or a lack of vendor support, should be prioritized to mitigate potential risks.
- Cost of Migration: Applications with lower migration costs should be considered for early migration to demonstrate value and build momentum. However, cost should not be the sole determinant, and it must be balanced with other factors like business value and risk.
- Dependencies: Applications with fewer dependencies or that are independent of other systems can be migrated earlier. This minimizes the impact on other applications and reduces the risk of cascading failures.
The prioritization process can utilize a scoring system, where each application receives a score based on the evaluation criteria. For instance, a simple scoring model might assign points for business value, technical complexity, and risk. The applications with the highest scores are prioritized for migration. A more sophisticated model may use weighted scoring, where different criteria are assigned different weights based on their relative importance.
Stakeholder Involvement in Decision-Making
Successful application migration requires the active involvement and collaboration of various stakeholders. Each stakeholder brings unique perspectives, expertise, and responsibilities, which are crucial for informed decision-making and the overall success of the project.
- Business Owners: Represent the business units that use the applications. Their input is essential for understanding the business value, criticality, and future requirements of each application. They provide insights into the impact of migration on business processes and user experience.
- IT Operations: Responsible for the technical aspects of the migration, including infrastructure, security, and application performance. They assess the technical feasibility of migration, identify potential risks, and ensure that the migrated applications are compatible with the target environment.
- Application Development Teams: Possess deep knowledge of the application’s architecture, code, and dependencies. They provide expertise in the migration process, including refactoring, re-platforming, and testing.
- Security Teams: Ensure that the migration complies with security policies and regulations. They identify and mitigate security vulnerabilities, and ensure that the migrated applications are secure in the target environment.
- Project Management Office (PMO): Responsible for managing the overall migration project, including planning, budgeting, and communication. They coordinate the activities of different stakeholders and ensure that the project stays on track.
Effective communication and collaboration among stakeholders are critical for making informed decisions. This involves regular meetings, status reports, and open communication channels. The stakeholders should be involved in all stages of the decision-making process, from defining the evaluation criteria to prioritizing applications for migration. By involving all stakeholders, organizations can ensure that the migration is aligned with business objectives, technically feasible, and successfully implemented.
Tools and Technologies for Assessment
Application portfolio assessment relies heavily on specialized tools and technologies to streamline the data gathering, analysis, and decision-making processes. These tools automate many manual tasks, improve accuracy, and provide valuable insights that would be difficult or impossible to obtain otherwise. The selection of appropriate tools depends on the size and complexity of the application portfolio, the specific objectives of the assessment, and the available budget and expertise.
Tools Used to Support App Portfolio Assessment
A variety of tools support application portfolio assessment, spanning different functionalities and approaches. These tools can be broadly categorized based on their primary functions.
- Discovery and Inventory Tools: These tools automatically scan the IT environment to identify and catalog applications, their dependencies, and associated infrastructure. They often use techniques like network scanning, agent-based data collection, and integration with configuration management databases (CMDBs). Examples include tools from ServiceNow, BMC Software, and various open-source solutions.
- Data Analysis and Reporting Tools: Once the inventory is established, these tools are used to analyze the collected data, identify patterns, and generate reports. They often incorporate features for data visualization, filtering, and custom report generation. Examples include business intelligence (BI) platforms like Tableau and Power BI, as well as specialized assessment tools that offer built-in analytical capabilities.
- Dependency Mapping Tools: Understanding application dependencies is crucial for migration planning. These tools visualize relationships between applications, databases, servers, and other components, aiding in the identification of potential risks and impacts of migration. Examples include tools that integrate with application performance monitoring (APM) solutions and network monitoring tools.
- Cost Analysis Tools: Migration projects involve significant costs. Cost analysis tools help estimate the total cost of ownership (TCO) of applications, including both current and future costs, considering factors like infrastructure, licensing, and operational expenses. These tools often integrate with cloud cost management platforms.
- Assessment and Prioritization Tools: These tools provide frameworks and methodologies for evaluating applications based on various criteria, such as business value, technical fit, and risk. They often incorporate scoring mechanisms and prioritization algorithms to help determine the optimal migration strategy. Examples include tools from CAST, Micro Focus, and specialized assessment platforms.
Advantages and Disadvantages of Various Assessment Tools
Each type of assessment tool offers unique advantages and disadvantages, influencing its suitability for specific assessment scenarios. The following highlights some of the key considerations.
- Discovery and Inventory Tools:
- Advantages: Automated data collection, reduced manual effort, improved accuracy, and comprehensive inventory.
- Disadvantages: Can be resource-intensive to deploy and maintain, may require agents or access credentials, and may struggle with shadow IT or undocumented applications.
- Data Analysis and Reporting Tools:
- Advantages: Powerful data visualization, custom reporting capabilities, and identification of trends and patterns.
- Disadvantages: Requires data to be fed from other tools, the quality of the analysis depends on the data, and may require specialized skills to use effectively.
- Dependency Mapping Tools:
- Advantages: Visual representation of complex dependencies, identification of critical paths, and improved migration planning.
- Disadvantages: Can be complex to set up and configure, may require detailed configuration data, and can be time-consuming to maintain as dependencies change.
- Cost Analysis Tools:
- Advantages: Accurate cost estimation, TCO analysis, and identification of cost optimization opportunities.
- Disadvantages: Requires detailed cost data, can be complex to model, and may be sensitive to changing market conditions.
- Assessment and Prioritization Tools:
- Advantages: Structured assessment framework, standardized evaluation criteria, and improved decision-making.
- Disadvantages: May require customization to align with specific business needs, the scoring mechanism can be subjective, and requires expertise to interpret the results.
Detailed Description of a Specific Tool and Its Features
CAST Highlight is a software intelligence platform designed to assess application portfolios and provide insights for modernization and migration initiatives. It offers a range of features that automate many of the tasks involved in application portfolio assessment.
- Automated Application Discovery and Inventory: CAST Highlight automatically discovers applications within the IT environment through agentless scanning. It identifies technology stacks, code languages, and frameworks used by each application.
- Code-Level Analysis: The tool performs a deep dive into the application’s source code to analyze its structure, complexity, and technical debt. It identifies potential issues such as security vulnerabilities, performance bottlenecks, and maintainability problems. This analysis is based on a comprehensive set of rules and metrics.
- Business Value Assessment: CAST Highlight allows users to assess the business value of applications based on factors such as their criticality, user base, and alignment with business objectives. This enables prioritization based on both technical and business considerations.
- Cloud Readiness Assessment: The platform assesses each application’s suitability for cloud migration, considering factors such as its technical architecture, dependencies, and compliance requirements. It provides recommendations on the best migration strategy (e.g., rehost, replatform, refactor).
- Risk Assessment: CAST Highlight identifies and quantifies risks associated with each application, including security risks, compliance risks, and operational risks. This helps in prioritizing remediation efforts and mitigating potential problems.
- Visualization and Reporting: The platform provides interactive dashboards and reports that visualize the assessment results, enabling stakeholders to easily understand the portfolio’s composition, identify areas for improvement, and track progress over time. It supports a variety of export formats, allowing for easy sharing and integration with other systems.
- Integration Capabilities: CAST Highlight integrates with various third-party tools and platforms, including CMDBs, cloud providers, and DevOps tools, streamlining the assessment process and providing a holistic view of the application portfolio.
The advantages of CAST Highlight include its automated discovery, in-depth code analysis, comprehensive assessment framework, and visualization capabilities. However, like any tool, it has potential disadvantages. The accuracy of the analysis depends on the quality of the source code and the configuration of the tool. The initial setup and configuration may require some effort. The cost of the platform may be a factor, especially for smaller organizations.The use of tools like CAST Highlight can significantly accelerate the application portfolio assessment process, providing actionable insights that drive informed decision-making for migration and modernization initiatives.
For example, a financial institution might use CAST Highlight to assess its legacy core banking system. The tool could identify critical dependencies, security vulnerabilities, and cloud readiness issues. Based on the assessment results, the institution could then prioritize the modernization of the core banking system and choose the most appropriate migration strategy, reducing the risk and cost of the migration.
Final Conclusion
In conclusion, application portfolio analysis for migration is more than just a preliminary step; it’s a strategic imperative. By systematically evaluating applications, organizations can make informed decisions, mitigate risks, and streamline the migration process. The insights gained through this analysis drive strategic alignment, cost optimization, and improved agility, ultimately paving the way for a successful digital transformation. Embracing this methodology ensures that migration efforts are not only technically sound but also strategically aligned with the overarching business goals, leading to a more resilient and adaptable IT landscape.
Essential Questionnaire
What is the primary benefit of application portfolio analysis?
The primary benefit is informed decision-making, allowing organizations to prioritize migration efforts based on business value, technical feasibility, and risk assessment, leading to more efficient resource allocation and reduced project costs.
How does this analysis reduce migration risk?
By identifying application dependencies, potential compatibility issues, and security vulnerabilities upfront, the analysis allows for proactive mitigation strategies, minimizing the likelihood of disruptions and failures during the migration process.
Who typically performs this assessment?
This assessment is typically performed by a combination of internal IT staff, consultants specializing in application portfolio analysis, and cloud migration experts, depending on the organization’s resources and expertise.
What are the key outputs of an application portfolio analysis?
Key outputs include a detailed application inventory, a migration roadmap, a prioritized list of applications for migration, and recommendations for modernization or retirement, along with associated cost estimates and timelines.